
Network utility tool for Linux systems that performs some network and security administrator tasks.
This is a network utility tool that I developed to perform some network and security administrator tasks. Currently, this script can perform a good variety of tasks such as:
- Port scans, including SYN, TCP, UDP, ACK, comprehensive scan;
- Host discovery (scan for up devices on a local network);
- Banner grabbing;
- DNS checks with geolocation information;
- ifconfig;
- ping;
- traceroute;
- IP spoofing (beta);
- Packet sniffing (beta).
Other features are still being implemented. Future implementations may include WAP (web application firewall) detection, vulnerability reconnaissance, static code analysis, traffic analysis, ARP poisoning, exploits, some automated tasks and others.
Installation
Note that currently, this script can only run well on Linux. If you try it in on Windows or macOS, it may run, but numerous errors will appear.
Linux
To install the necessary packages so that the script can run withouth any problems simply run the setup.sh script with root privileges. Currently, this installation script is only supported on debian-based distros that has the apt package manager (Ubuntu, Kali, Parrot, Debian, PopOS, Mint, etc). On most systems, to install medsec simply run the following commands:
git clone https://github.com/medpaf/medsec.git
cd medsec
sudo . setup.sh
However, if you are using any other Linux distro with a different package manager, please install the packages manually using your distro’s package manager. Depending on the specific distro used, some of the required packages to run this script might be already installed on your machine. The necessary packages are:
- nmap (using your system’s package manager)
- traceroute (using your system’s package manager)
- python3-pip (using your system’s package manager)
- python-nmap (using pip3)
- colorama (using pip3)
- ipinfo (using pip3)
- scapy (using pip3)
After the installation, to run the program, simply navigate to the project’s directory and run the medsec.py file using python. Running the script as root is recommended for better performance and to avoid permission errors. The used command is the following:
sudo python3 medsec.py
How to use
Scanning ports
Multiple scan types are supported, including SYN (-scansyn), TCP (-scantcp), UDP (-scanudp), ACK (-scanack) and comprehensive scan (-scan).
-scan -host [HOST(s)]
-scan -host [HOST(s)] -p [PORT(s)]
-scan -host [HOST(s)] -prange [START PORT] [END PORT]
-scan -iprange [START IP] [END IP] -p [PORT(s)]
-scan -iprange [START IP] [END IP] -prange [START PORT] [END PORT]
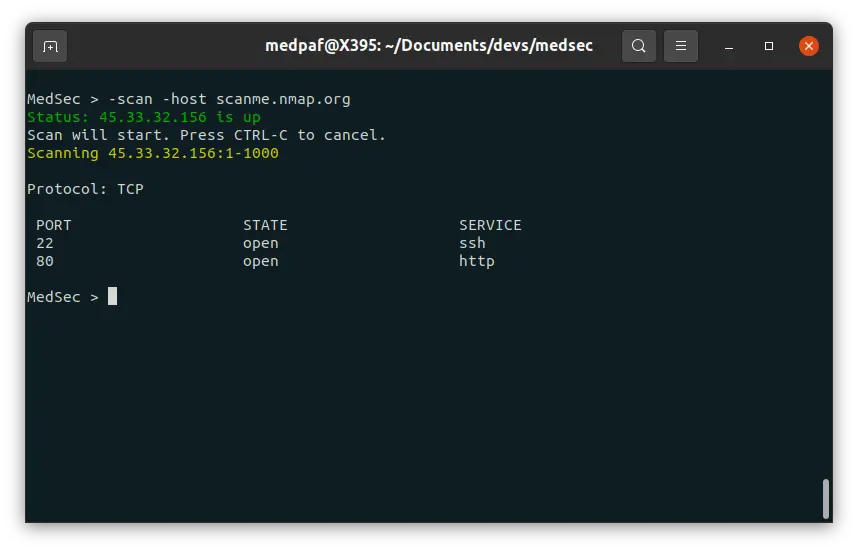
After this scan, it is possible to see that both 22 (SSH) and 80 (HTTP) ports are open.
Host discovery
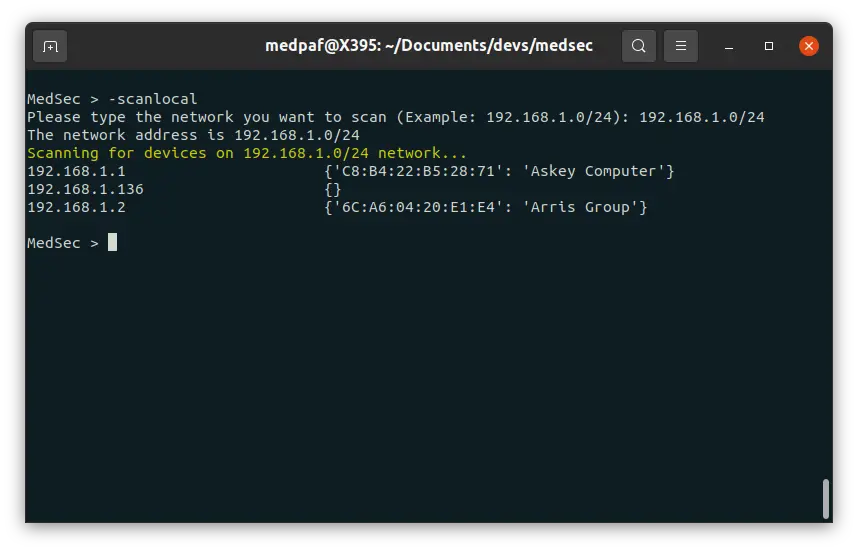
To look for current up devices on a given network type the following command:
-scanlocal
Then type the network you want to scan.
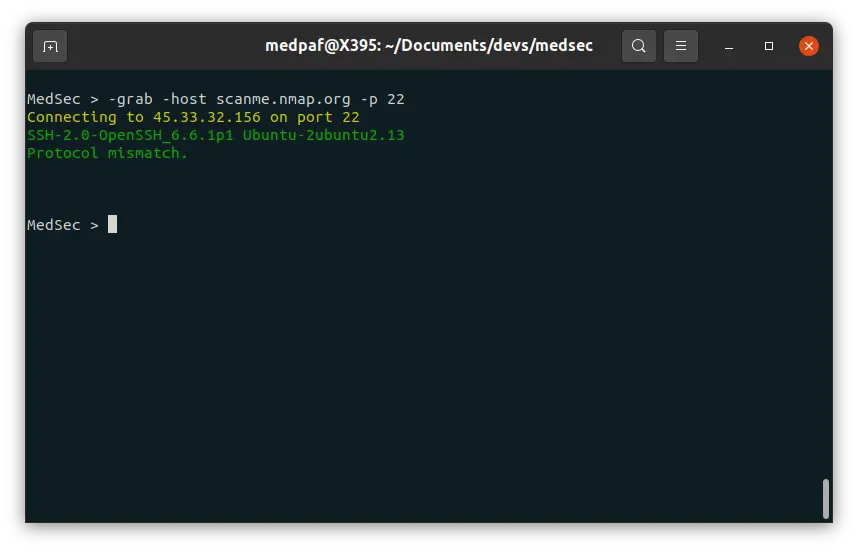
Banner grabbing
To perform banner grabbing, depending on your specific needs, type one of the following commands:
-grab -host [HOST(s)] -p [PORT(s)]
-grab -iprange [START IP] [END IP] -prange [START PORT] [END PORT]
-grab -host [HOST(s)] -prange [START PORT] [END PORT]
-grab -iprange [START IP] [END IP] -p [PORT(s)]
DNS checks
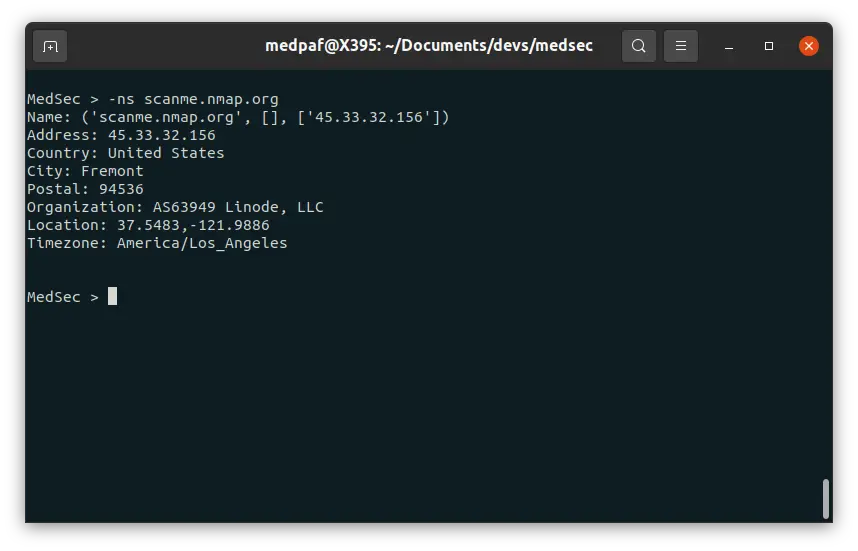
This feature is similar to the well known nslookup command used on UNIX systems. If you want to do a DNS check, type the following:
-ns [HOST(s)]
ifconfig
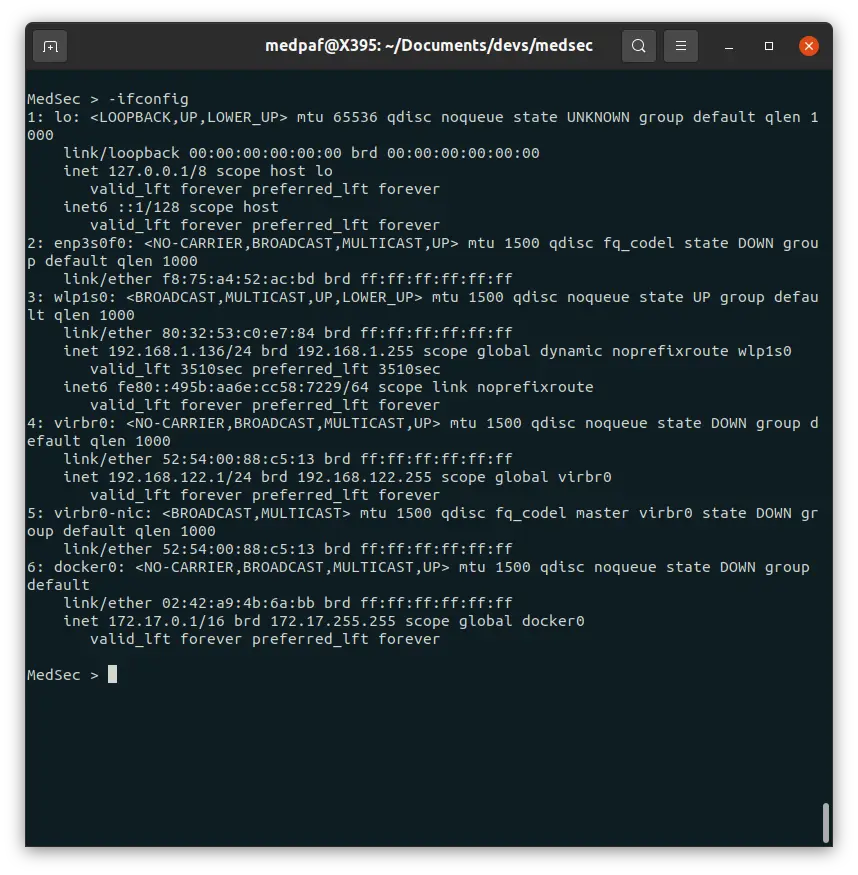
If you want to display your system’s current TCP/IP network configuration, type the following command:
-ifconfig
ping
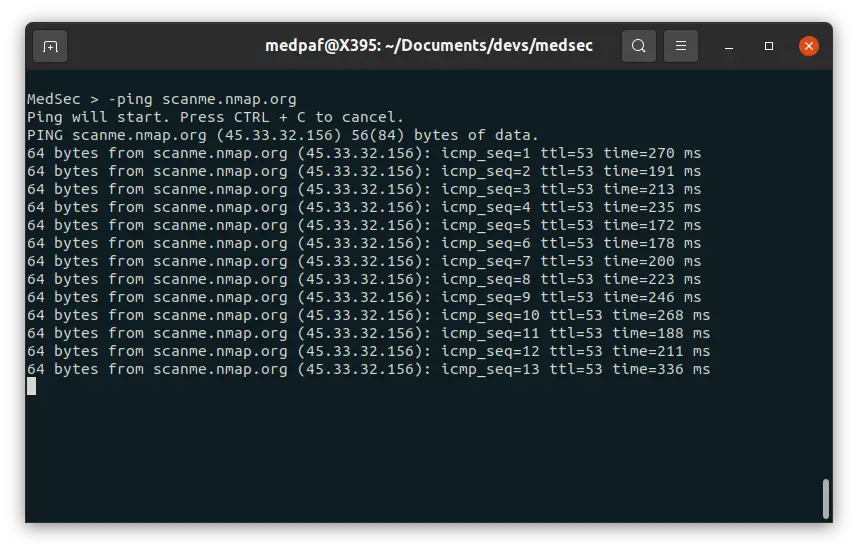
To send ICMP packets to a host to check connectivity, simply type:
-ping [HOST]
traceroute
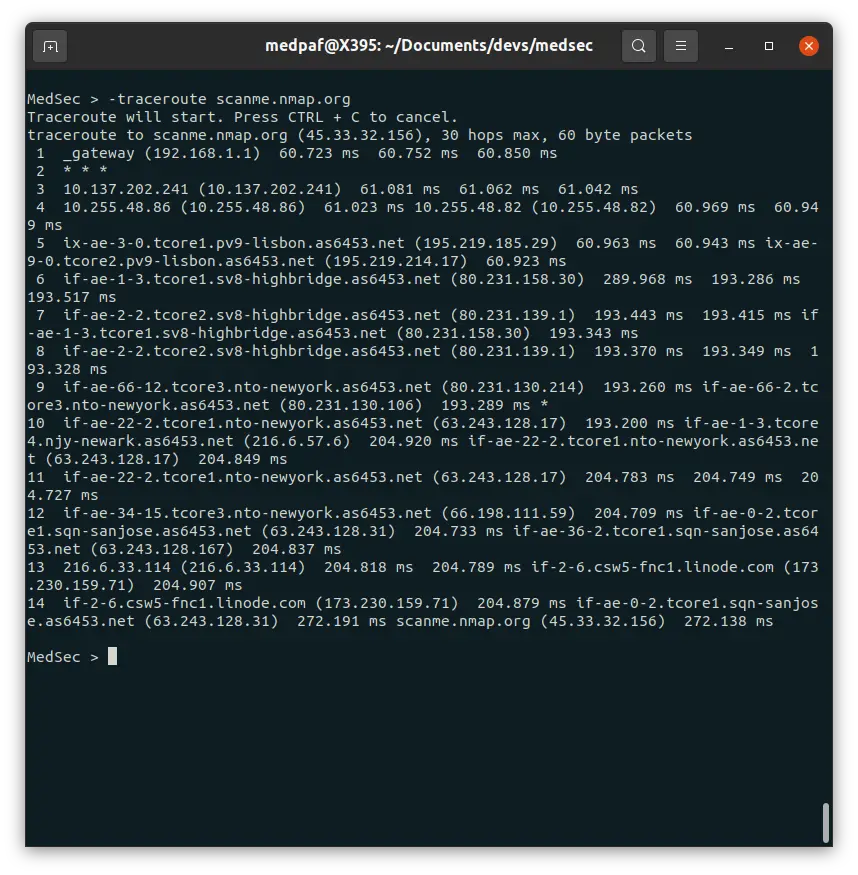
To diagnose route paths and measure transit delays, use the -traceroute command:
-traceroute [HOST]
IP spoofing
Note that this command only works on machines with unpached vulnerabilities. To performe IP spoofing on a host’s specific port, use the following command:
-spoof -host [HOST] -p [PORT]
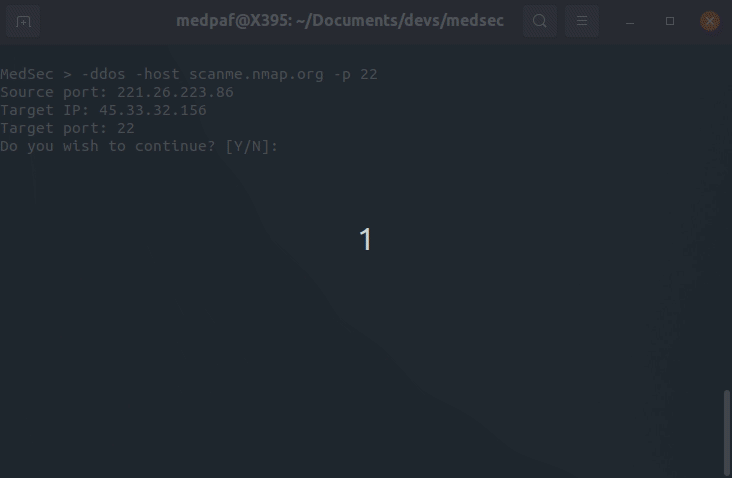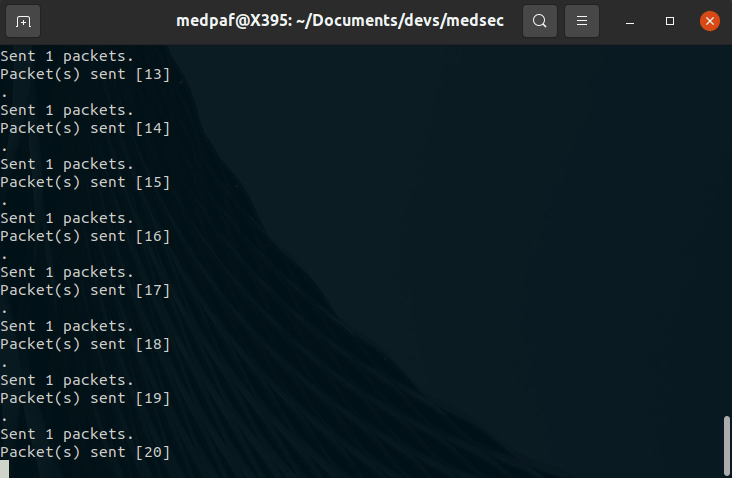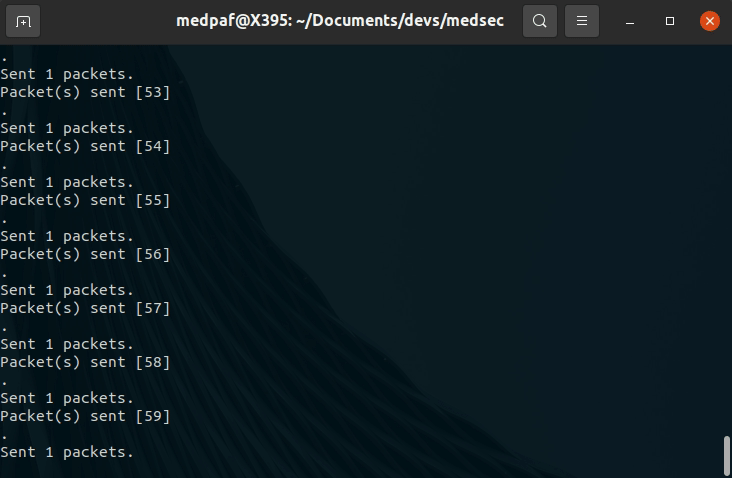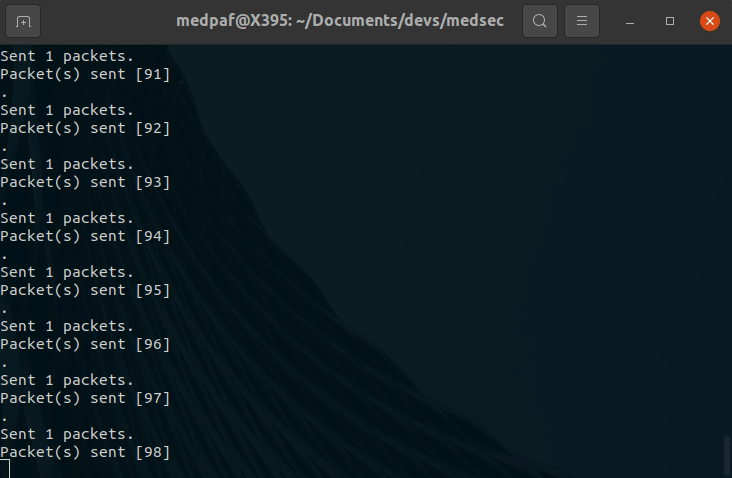
Disclaimer: Please only use this for testing purposes and target your own machines.
Packet sniffing
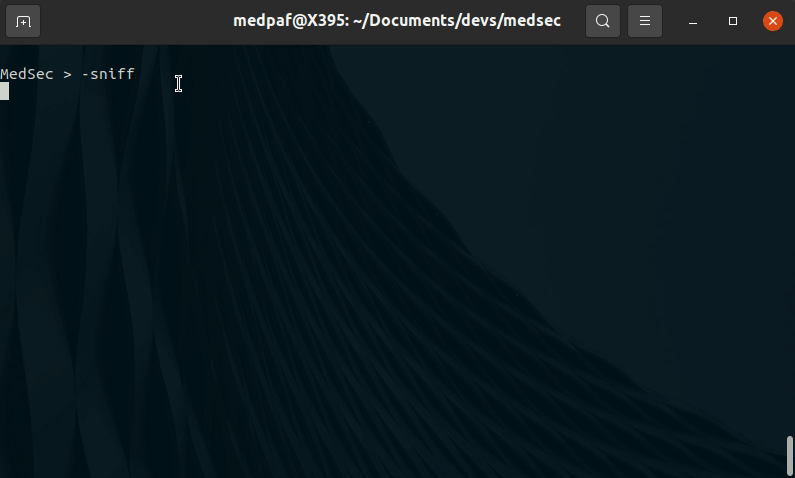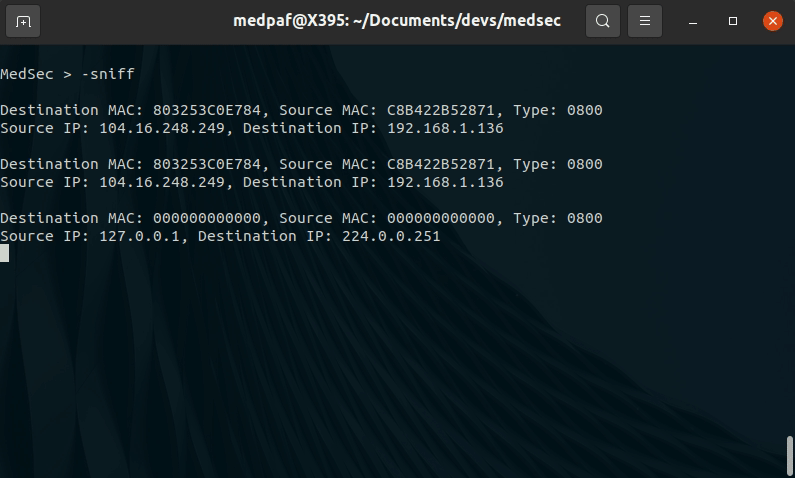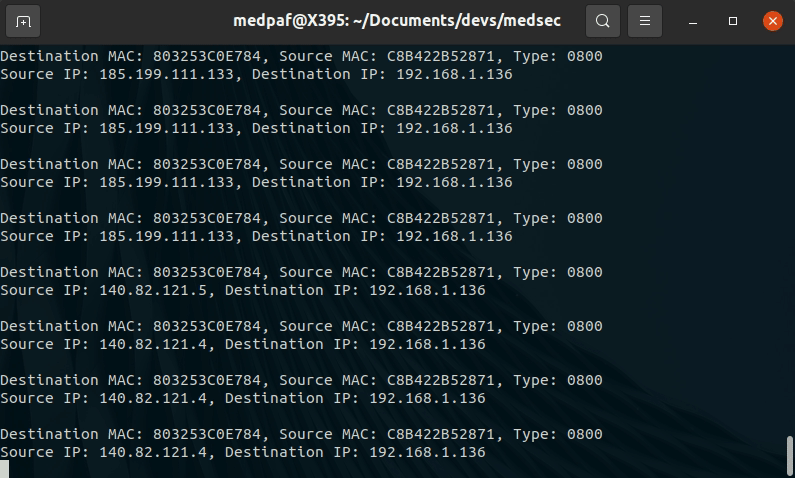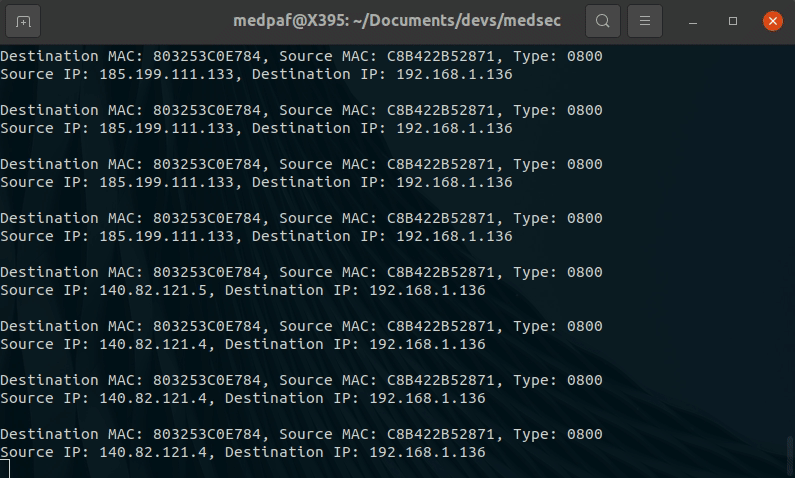
To perform packet sniffing, type:
-sniff
Contribution
Create a issue or pull request, or send me an email at pafmed@outlook.com.
License
This repository is under the MIT License.
























Leave a Reply