
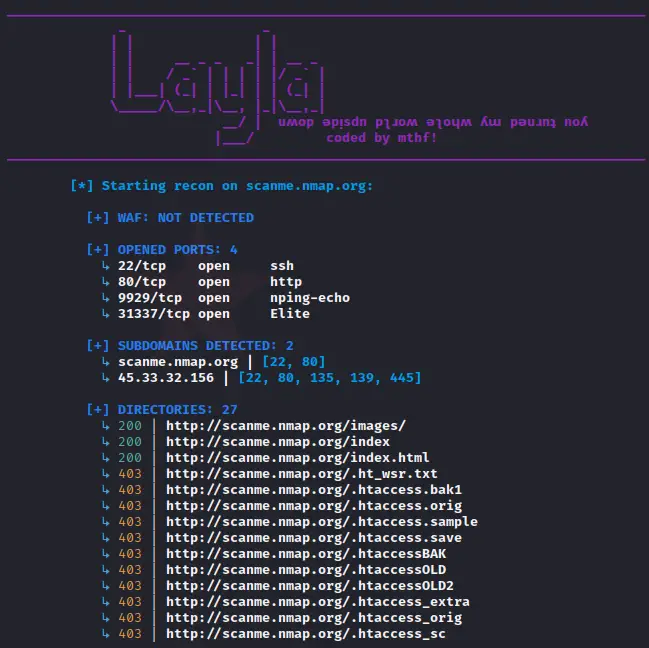
Layla is a python script that automatically performs recon on a given URL. It combines the outputs of other known tools into a single one.
Getting Started
To start, make sure that you’re using a Debian-based distro, like Kali Linux, for example. Since the script uses Python3 to run, it’s essential to have it installed on your machine.
- Cloning the project:
git clone https://github.com/mthf0/layla.git
- Get into the project’ folder:
cd layla/
- Install all dependencies
chmod +x install.sh & sudo ./install.sh
- Run the script
python3 layla.py --url owasp.org
Features:
- Web Application Firewall Detection
- Port Scanning
- Subdomain Detection
- Directory Discovery
TODO’s:
This script needs a lot of improvements, which I’ll definitely add with time. I’ll list some of them below:
Fine-tune some parameters from:
- NMAP
- AMASS
Add subdomain takeover detection with subjack.
Add visual recon, aquatone would be nice for that.
Add permutation scanning using dnsgen.
Add certificate search from crt.sh. (automated script)
Add GitHub recon.
The Layla tool is a github repository by Matheus Faria


























Leave a Reply