
Project iKy – Tool That Collects Information From An Email

Project iKy is a tool that collects information from an email and shows results in a nice visual interface.
Installation
Clone repository
git clone https://gitlab.com/kennbroorg/iKy.gitInstall Backend
Redis
You must install Redis
wget http://download.redis.io/redis-stable.tar.gz
tar xvzf redis-stable.tar.gz
cd redis-stable
make
sudo make installPython stuff and Celery
You must install the libraries inside requirements.txt
python3 -m pip install -r requirements.txtInstall Frontend
Node
First of all, install nodejs.
Dependencias
Inside the directory, frontend install the dependencies
cd frontend
npm installWake up iKy Tool
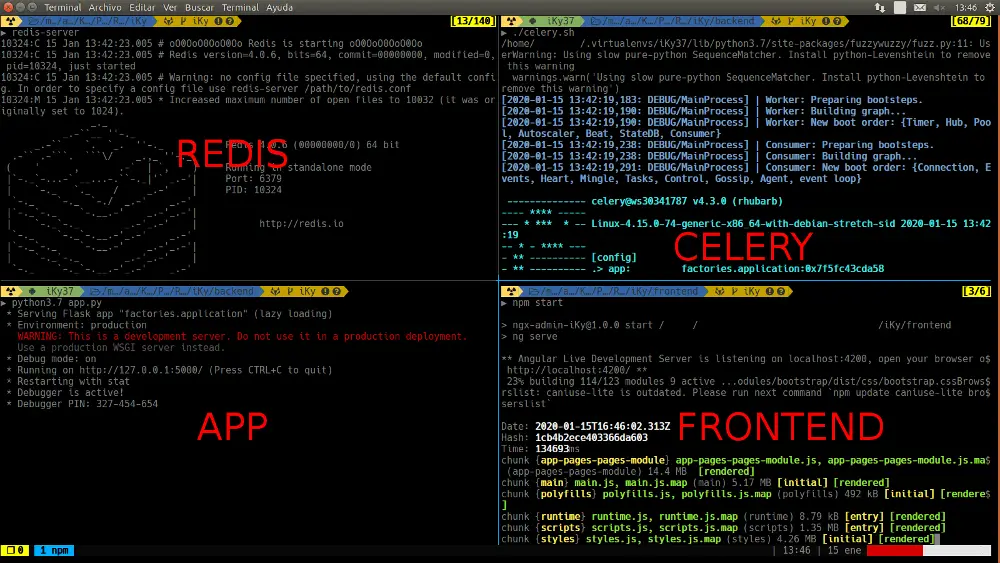
Turn on Backend
Redis
Turn on the server in a terminal
redis-serverPython stuff and Celery
Turn on Celery in another terminal, within the directory backend
./celery.shAgain, in another terminal turn on backend app from directory backend
python3 app.pyTurn on Frontend
Finally, to run frontend server, execute the following command from directory frontend
npm startScreen after turn on iKy
Demo



























Leave a Reply