
How XDR Can Address Cloud Security Challenges by Gilad David Maayan
XDR is a new type of security platform which can detect threats more efficiently than previous tools, by collecting and automatically correlating information from multiple security layers. XDR monitors threats from various sources and locations in your organization.
Many attacks evade detection because attackers hide in borderline areas between security silos, such as endpoints, the network, or cloud systems. XDR covers all security silos in one system, so it can see events, which may seem separate and unrelated, as part of a single attack story.
XDR eliminates security silos with a holistic detection and response strategy. It gathers information and builds detailed attack stories across endpoints, servers, email systems, and cloud workloads. It automatically analyzes data to triage and identify real threats, without requiring analysts to spend time reviewing the data.
There are two more things XDR can do which are not possible in the previous generation of security technologies:
- Gathers in-depth forensic information and puts it at the fingertips of analysts, making it easier for them to investigate and respond to the threat.
- Allows analysts to immediately respond to the threat by activating remote systems—this is similar to endpoint detection and response (EDR), but unlike EDR, which was limited to endpoints XDR can operate at any security layer.
- Enables automated response—XDR can identify threats and run automated processes to contain and eradicate the threat without human involvement. This can dramatically reduce attacker dwell time.
How Does XDR Work?
XDR integrates with existing IT systems and security tools, and accesses raw data collected from the entire IT environment. Unlike security information and event management (SIEM), XDR does not simply collect alerts and logs from other tools. It goes in-depth, performs its own investigation and analyzes the data using advanced artificial intelligence techniques.
XDR consists of three main components:
- Telemetry and Data Analysis—XDR monitors and collects data from endpoints, networks, servers and clouds, and uses data analytics to correlate the context of thousands of alerts occurring in these tiers, to discover real threats and reduce false positives.
- Detection—XDR creates visibility of a baseline of normal behavior in the environment, allowing teams to easily detect threats, investigate their cause, and prevent them from spreading and doing damage.
- Response—XDR lets security teams manage security policies and define automated playbooks for responding to certain types of alerts. XDR can respond to threats occurring anywhere in the IT environment, by integrating with security controls such as firewalls, endpoint protection platforms, and cloud identity and access management (IAM) systems.
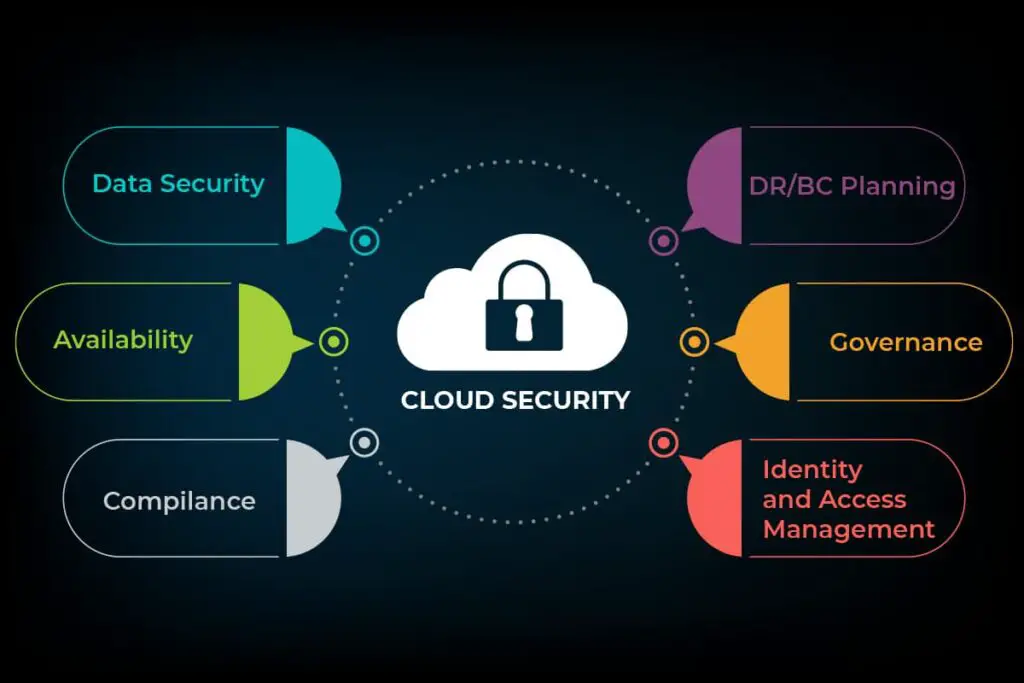
Cloud Security Challenges
As more organizations move sensitive and business-critical workloads to the cloud, cloud security is becoming a central concern for most IT and security teams. When running workloads in a public cloud-like Amazon Web Services (AWS) or Azure, teams have access to extensive security controls offered by the cloud provider.
However, there is usually no central control over which workloads are actually running the cloud and whether they have been properly secured. While XDR does not help with this fundamental problem, it can help identify and detect threats that slip through the cracks of cloud security.
Let’s discuss some of the key cloud security challenges organizations face when moving workloads to the cloud.
Misconfiguration
Misconfigured cloud security settings were the cause of many significant security breaches. While the cloud does provide security controls, organizations do not have the visibility to ensure that they are configured correctly.
In the cloud, there are a large number of ephemeral resources—for example, compute instances, containers, or serverless functions, which can run for days, hours, or even just minutes—and then shut down and are replaced by others. Each of these resources could potentially have a security misconfiguration that can let attackers in.
In addition, there is limited visibility into what is actually running the cloud, especially when organizations run workloads across multiple clouds. Security teams do not have the tooling and expertise to identify which cloud workloads are securely configured or not.
Insider Threats
Insider threats are a growing concern for all organizations, and are an even bigger threat in the cloud. When insiders access cloud resources, they can easily open access to the Internet, share resources with others, and automatically set up configurations or resources. A malicious insider with sufficient permissions can do much more damage than they could in a local environment. Cloud environments are very flexible and powerful, putting much more power at the hands of a malicious insider.
Insecure Interfaces/APIs
Cloud infrastructure relies on a large number of APIs (application programming interfaces) to allow automated, programmatic control. These interfaces are well documented and readily available to all cloud users, including attackers. If customers do not properly secure their interfaces, attackers can use the same documentation to identify and exploit vulnerabilities, access and steal sensitive data.
Unauthorized Access
Unlike an organization’s on-premise infrastructure, cloud-based deployments are outside the perimeter of the network and can be accessed directly from the public internet. This makes it easy for attackers to gain unauthorized access to cloud systems. On-premises, a sensitive server with a weak password would still be behind a firewall and protected by the overall network security perimeter. In the cloud, the same server can be directly accessed and breaches by an attacker.
XDR for Cloud Security
Cloud security is no longer an isolated field. For most organizations, the cloud is tightly integrated with on-premises systems, and security incidents in one environment can quickly spread to another. It is no longer effective to analyze and respond to on-premises and cloud incidents separately.
Another change is that cloud security has shifted left. Security teams take part in the development sprints and participate in software testing and deployment planning. However, this transformation is not possible without security tools that provide full visibility and control over
the entire hybrid environment.
XDR can contribute to cloud security in three main ways:
- Identity management—XDR can perform telemetry on human users and service roles, collecting data from heterogeneous cloud systems across multiple cloud providers. XDR can pick up anomalous activity on privileged accounts, correlate it with other activity in related environments, and immediately alert security teams.
- Cloud log analysis—cloud systems produce enormous amounts of logs, which contain detailed, valuable information, but are difficult to analyze manually. XDR parses this data and uses machine learning algorithms to identify security incidents. It can do this across an entire multi-cloud deployment, pointing analysts directly to threats and their root causes in the cloud environment.
- Analyzing network flows—cloud networking is extremely complex, with networking between cloud systems (East-West traffic) and between the cloud and on-premises or external systems (South West traffic). XDR can go beyond monitoring NetFlow on specific cloud machines. It can look at network traffic across the entire environment, pick up suspicious activity, and integrate with cloud network APIs to isolate infected resources and prevent threats from spreading.
Conclusion
In this article, I explained the tremendous potential of XDR, which is not only a platform but a new paradigm in security technology. I showed how XDR can address cloud security challenges including:
- Misconfiguration
- Insider Threats
- Insecure Interfaces/APIs
- Unauthorized Access
XDR can do this in a way traditional security technologies cannot, by taking identity management, cloud log analysis, and network flow analysis to the next level. I hope this will help your organization take your next steps in fortifying cloud security.
About the Author
Gilad David Maayan
Gilad David Maayan is a technology writer who has worked with over 150 technology companies including SAP, Imperva, Samsung NEXT, NetApp and Ixia, producing technical and thought leadership content that elucidates technical solutions for developers and IT leadership. Today he heads Agile SEO, the leading marketing agency in the technology industry.
LinkedIn: https://www.linkedin.com/in/giladdavidmaayan/

























Leave a Reply