

1. Introduction to Vulnerability
vSphere is a virtualization platform suite launched by VMware, which includes a series of software such as ESXi and vCenter Server. VCenter Server is the control center of ESXi, which can uniformly manage all vSphere hosts and virtual machines in the data center from a single control point, enabling IT administrators to improve control capabilities, simplify entry tasks, and reduce the management complexity and cost of the IT environment .
The vSphere Client (HTML5) has a remote code execution vulnerability in the vCenter Server plug-in. An unauthorized attacker can send a carefully constructed request to vCenter Server through a server that opens port 443, thereby writing a webshell on the server, and ultimately causing remote arbitrary code execution.
2. scope of influence
– vmware:vcenter_serverVersion 7.0 before 7.0 U1c
– vmware:vcenter_server6.7 version before U3l
– vmware:vcenter_server6.5 version prior to 6.5 U3n
3. vulnerability impact
VMware has assessed the severity of this problem as severe, with a CVSSv3 score of 9.8.
4. vulnerability analysis
The vROPS plug-in API of vCenter Server has not been authenticated, and there are some sensitive interfaces. The uploadova interface has a function to upload OVA files:
@RequestMapping(
value = {"/uploadova"},
method = {RequestMethod.POST}
)
public void uploadOvaFile(@RequestParam(value = "uploadFile",required = true) CommonsMultipartFile uploadFile, HttpServletResponse response) throws Exception {
logger.info("Entering uploadOvaFile api");
int code = uploadFile.isEmpty() ? 400 : 200;
PrintWriter wr = null;
...
response.setStatus(code);
String returnStatus = "SUCCESS";
if (!uploadFile.isEmpty()) {
try {
logger.info("Downloading OVA file has been started");
logger.info("Size of the file received : " + uploadFile.getSize());
InputStream inputStream = uploadFile.getInputStream();
File dir = new File("/tmp/unicorn_ova_dir");
if (!dir.exists()) {
dir.mkdirs();
} else {
String[] entries = dir.list();
String[] var9 = entries;
int var10 = entries.length;
for(int var11 = 0; var11 < var10; ++var11) {
String entry = var9[var11];
File currentFile = new File(dir.getPath(), entry);
currentFile.delete();
}
logger.info("Successfully cleaned : /tmp/unicorn_ova_dir");
}
TarArchiveInputStream in = new TarArchiveInputStream(inputStream);
TarArchiveEntry entry = in.getNextTarEntry();
ArrayList result = new ArrayList();
The code logic is to decompress the TAR file and upload it to the /tmp/unicorn_ova_dir directory. Note the following code:
while(entry != null) {
if (entry.isDirectory()) {
entry = in.getNextTarEntry();
} else {
File curfile = new File("/tmp/unicorn_ova_dir", entry.getName());
File parent = curfile.getParentFile();
if (!parent.exists()) {
parent.mkdirs();
Directly concatenate the TAR file name with /tmp/unicorn_ova_dir and write it into the file. If there is ../ in the file name, directory traversal can be achieved.
For the Linux version, you can create a TAR file containing ../../home/vsphere-ui/.ssh/authorized_keys and upload it to log in using SSH:
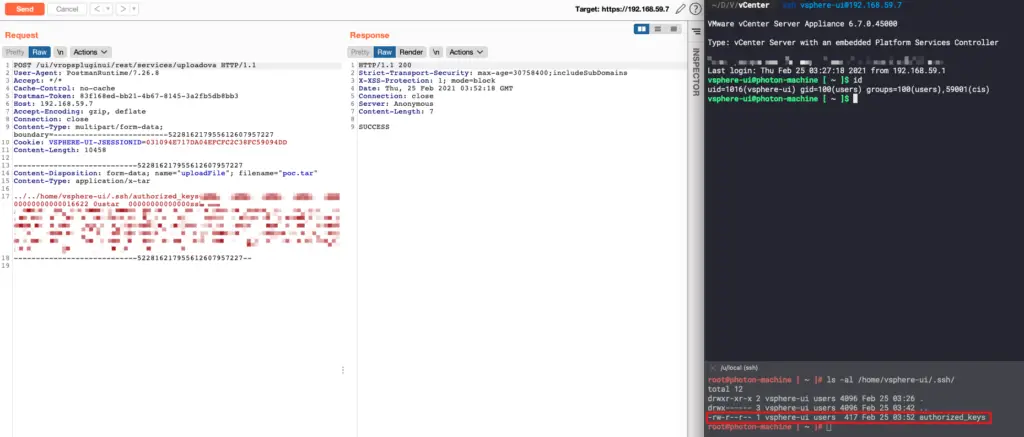
For the Windows version, you can write JSP webshell files on the target server. Since the service has System permissions, you can write to any file.
5. bug fix
Upgrade to the safe version:
– Upgrade from vCenter Server 7.0 version to 7.0.U1c
– VCenter Server 6.7 version upgraded to 6.7.U3l
– Upgrade from vCenter Server 6.5 to 6.5 U3n
Temporary repair suggestions
1. SSH remote connection to vCSA (or remote desktop connection to Windows VC)
2. Back up the following files:
– The path of the Linux system file is: /etc/vmware/vsphere-ui/compatibility-matrix.xml (vCSA)
– The Windows file path is: C:\ProgramData\VMware\vCenterServer\cfg\vsphere-ui (Windows VC)
3. Use a text editor to modify the content of the file to:
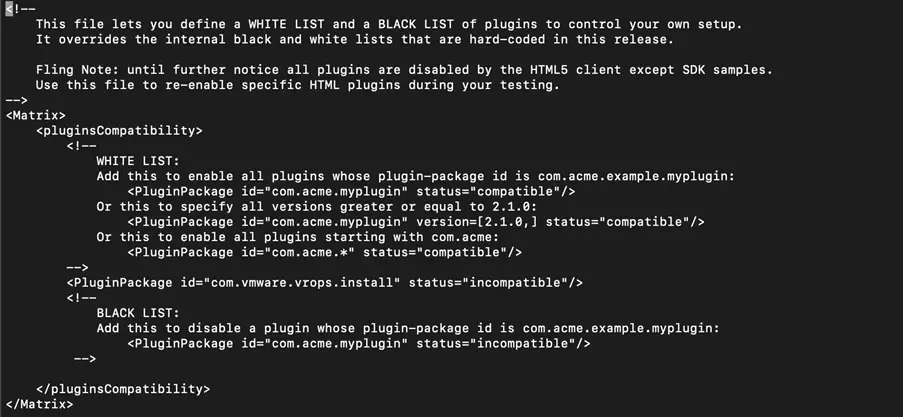
4. Use the vmon-cli -r vsphere-uicommand to restart the vsphere-uiservice
5. Access https://<VC-IP-or-FQDN>/ui/vropspluginui/rest/services/checkmobregister, display a 404 error

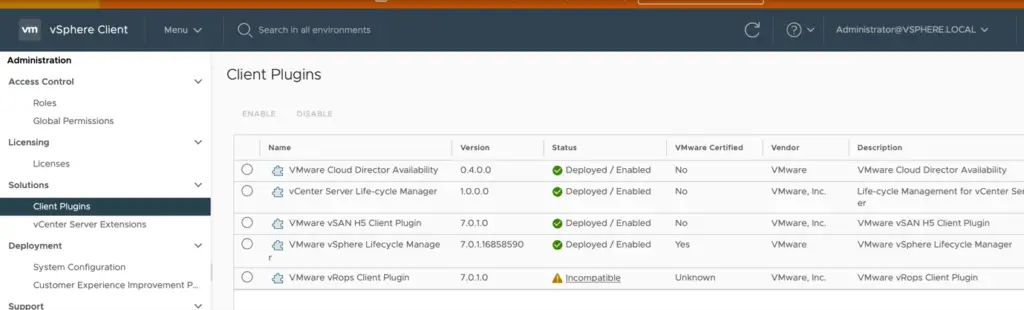
6. In vSphere Clientthe Solutions->Client Pluginsthe VMWare vROPSplug appear asincompatible
6. reference link
1. NoahLab CVE-2021-21972 vCenter 6.5-7.0 RCE vulnerability analysis


























Leave a Reply