

Discover vulnerabilities and container image misconfiguration in production environments.
Introduction
The ClusterImageScanner detects images in a Kubernetes cluster and provides fast feedback based on various security tests. It is recommended to run the Cluster Scanner in production environments in order to get up-to-date feedback on security issues where they have real impact.
Since the ClusterImageScanner itself is a service running within your Kubernetes cluster you can re-use your existing deployment procedures.
Overview
The following figure provides an overview:
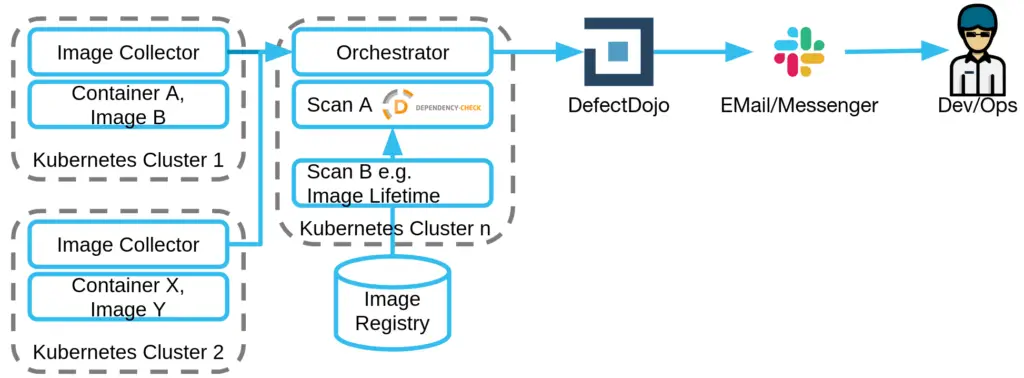
The following steps are conducted.
- The Image Collector, as the name suggests, collects the different images from a container environment like a kubernetes cluster. The Collector creates a JSON file and including information like the cluster, the responsible team, and image.
- The Orchestrator (implemented via ArgoWorkflows) starts the workflow periodically (e.g. nightly)
- The images from the Collector can be pulled by the Image Fetcher
- These files are kept in a separate directory and from there they are passed to the scanner
- This scanner – which then receives the libraries to be ignored via the suppressions file – then executes the scans described in the definitions of Dependency Check, Lifetime, Virus and further more.
- The vulnerability management system (in our case OWASP DefectDojo) then collects the results
- Non responded to findings are made available to the developers via a communication channel (Slack/Email).
Documentation Table of Contents
Video (English): SDA SE CluserImageScanner is going Open Source, 2021-03
Images
Images to be used by ArgoWorkflows are published in quay.io (2021-06-28):
cluster-image-scanner-scan-dependency-checkcluster-image-scanner-scan-runasrootcluster-image-scanner-scan-distrolesscluster-image-scanner-scan-lifetimecluster-image-scanner-scan-malwarecluster-image-scanner-scan-new-versioncluster-image-scanner-imagefetchercluster-image-scanner-notifiercluster-image-scanner-imagecollectorcluster-image-scanner-image-source-fetchercluster-image-scanner-workflow-runner- quay.io/sdase/defectdojo-client
cluster-image-scanner-base is the base for all cluster-image-scanner-* images.
Images are build with buildah. The env. parameters the image can be started with are documented via –config within the build.sh scripts within the images.
Contributing
We are looking forward to contributions. Take a look at our Contribution Guidelines before submitting Pull Requests.
Responsible Disclosure, Security
The SECURITY.md includes information on responsible disclosure and security related topics like security patches.
Legal Notice
The purpose of the ClusterImageScanner is not to replace the penetration testers or make them obsolete. We strongly recommend running extensive tests by experienced penetration testers on all your applications. The ClusterImageScanner is to be used only for testing purpose of your running applications/containers. You need a written agreement of the organization of the environment under scan to scan components with the ClusterScanner.
Author Information
This project is developed by Signal Iduna and SDA SE.



























Leave a Reply