Hidden parameters discovery suite written in Rust. The tool helps to ...
This is a repository of resource about Malware techniques. A curated ...
What are Cloud Security Threats? The high volume of data flowing between ...
Useful Google Dorks for WebSecurity and Bug Bounty My love google ...
Useful Techniques, Tactics, and Procedures for red teamers and defenders, alike! ...
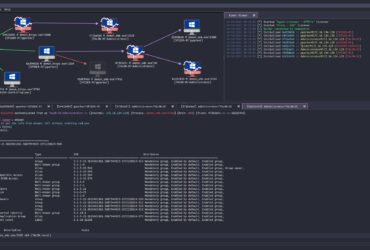
The Havoc Framework Havoc is a modern and malleable post-exploitation command ...
CVE-2022-21970 Description Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability. This vulnerability ...