

SearchMap_V1.0.2
Searchmap is a comprehensive information collection tool for pre-penetration testing that integrates domain name resolution, IP reverse domain name search, WHOIS query, CDN detection, port scanning, directory scanning, and subdomain mining.
1. Installation Instructions
- 1. The tool is developed using python3, please make sure that the python3 environment has been installed on your computer.
- 2. The port scanning function of the tool calls the nmap interface, please make sure that nmap is installed on your computer.
- 3. For the first use, please use the python3 -m pip install -r requirements.txt command to install the necessary external dependencies.
- 4. If the pip tool is not installed on this machine, please use the following command to install it:
$ curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py $ sudo python get-pip.py $ sudo python3 get-pip.py sudo apt-get install python-pip
2. How to use
1.-u Get the basic information of the website
$ python3 searchmap.py -u https://www.baidu.com
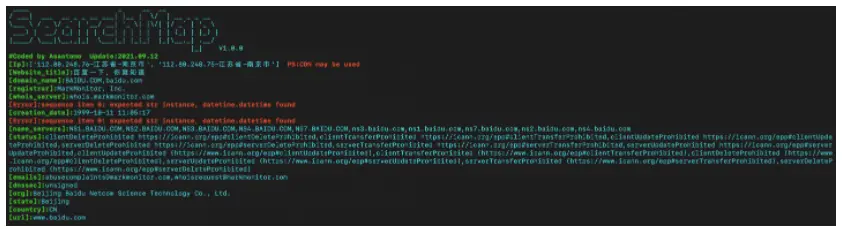
$ python3 searchmap.py -u 106.53.143.192

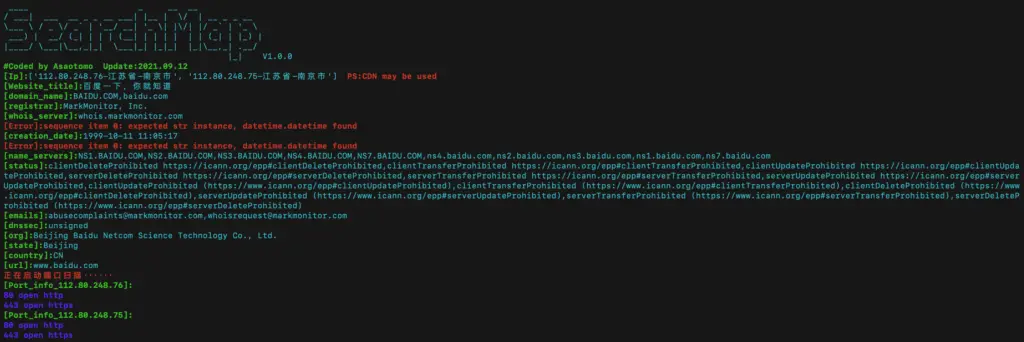
2.-p Implicit port scan using nmap
$ python3 searchmap.py -u https://www.baidu.com -p
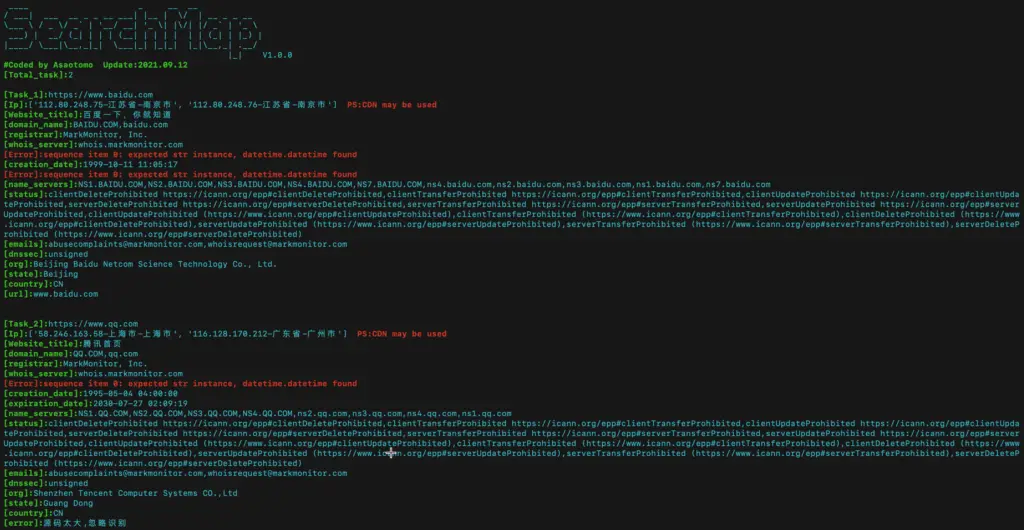
3.-r Batch scan website basic information
$ python3 searchmap.py -r myurl.txt
4.-n Use multiple pings to determine whether the target uses cdn acceleration
$ python3 searchmap.py -u https://www.baidu.com -n
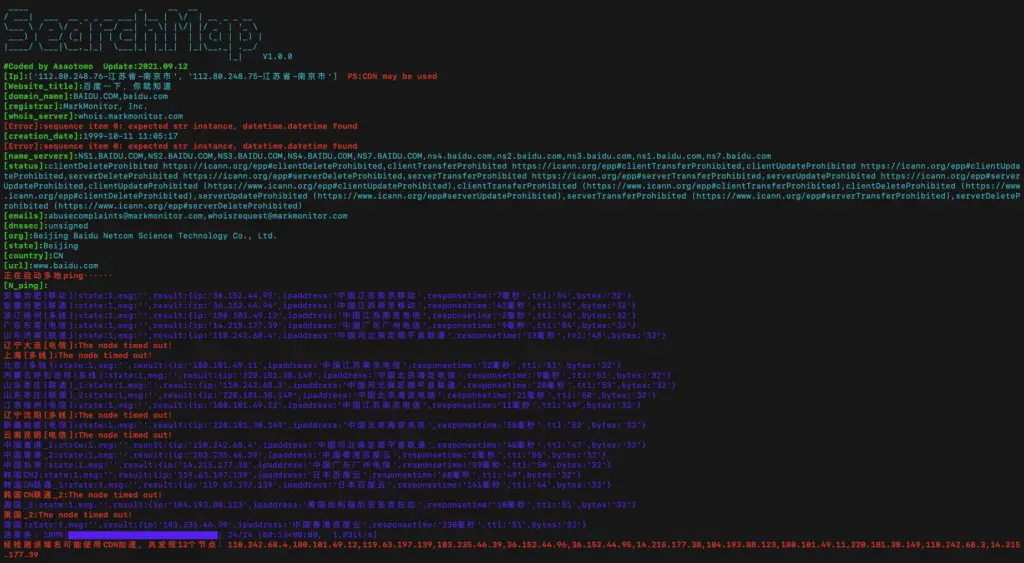
5.-d Perform multi-process scanning detection on the website directory, which can automatically identify fake response pages
PS: The default dictionary used by the program is dict/fuzz.txt, and the user can replace the dictionary content for FUZZ by himself.
$ python3 searchmap.py -u https://www.baidu.com -d
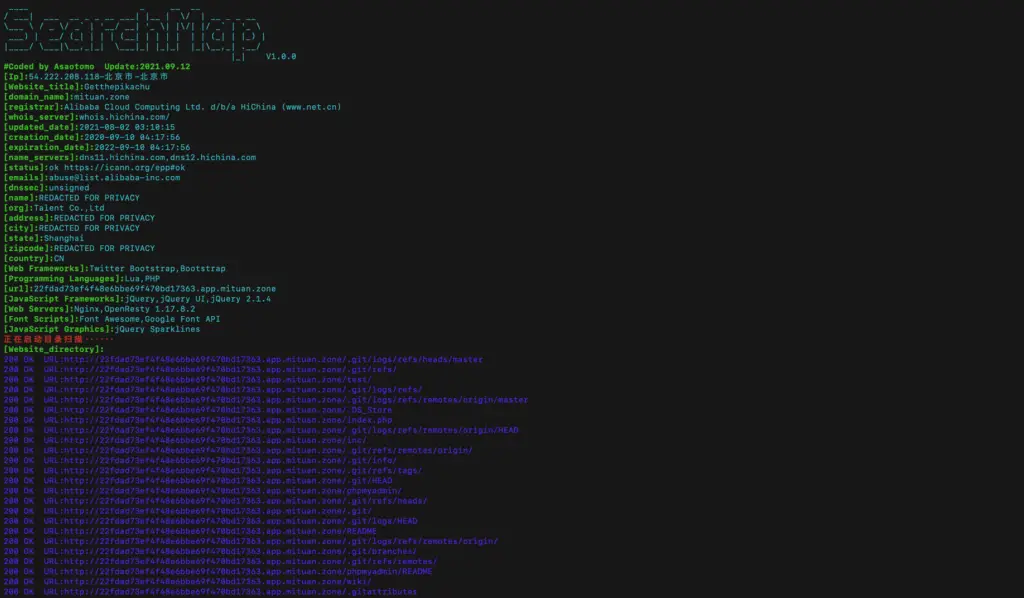
6.-s Subdomain blasting for the input domain name
PS: The default dictionary used by the program is dict/subdomain.txt, and the user can replace the dictionary content for FUZZ.
$ python3 searchmap.py -u https://www.baidu.com -s
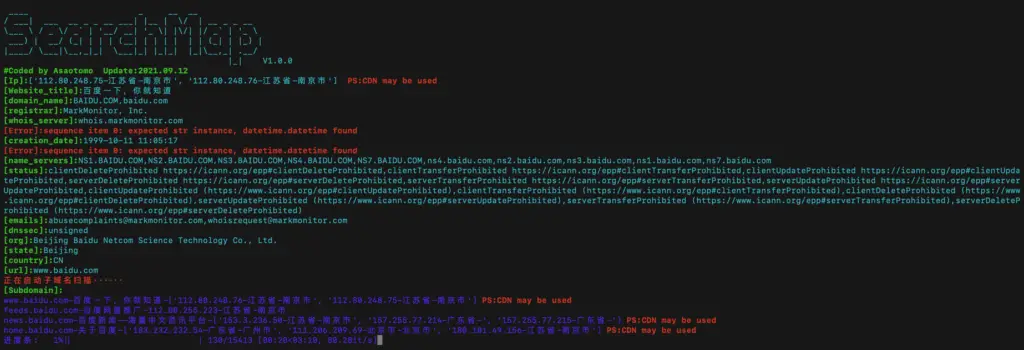
7.-a Perform a full-featured scan of the target domain name
$ python3 searchmap.py -u https://www.baidu.com -a
8.-o save scan content as log
$ python3 searchmap.py -u https://www.baidu.com -o myscan.log
9. Combination usage
$ python3 searchmap.py -u https://www.baidu.com -p -n -d -s $ python3 searchmap.py -r myurl.txt -p -n -d -s
PS: A security novice, there are many bugs in the first writing tool, everyone is welcome to submit Issues.
This tool is only provided for security testers to conduct security self-examination . All consequences caused by user abuse have nothing to do with the author. Users must abide by local laws . This program cannot be used for commercial purposes, only for learning and communication
The seearchmap is a github repository by asaotomo















Leave a Reply