
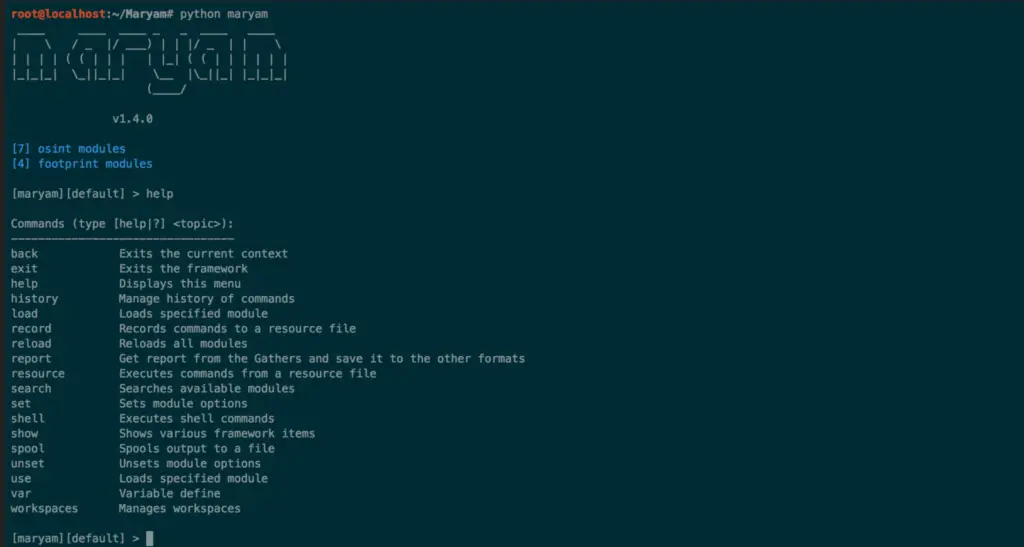
Maryam : Open-source Intelligence(OSINT) Framework
OWASP Maryam is an Open-source intelligence(OSINT) and Web-based Footprinting modular/tool framework based on the Recon-ng and written in Python. If you have skills in Metasploit or Recon-ng, you can easily use it without prerequisites. And if not, please read the Quick Guide.
What can be done
If you want
- Extracts Emails, Docs, Subdomains, Social networks from search engines
- Extracts Links, CSS and JS files, CDN links, Emails, Keywords from Web Source
- Find and Brute force DNS, TLD and important direct
- Crawl Web Pages and search your RegExp
- Identify WebApps, WAF, Interesting and important files
- And get a report with several formats
Install Maryam
git clone https://github.com/saeeddhqan/Maryam.git
cd Maryam
pip install -r requirements
chmod +x maryam
./maryamQuick Guide
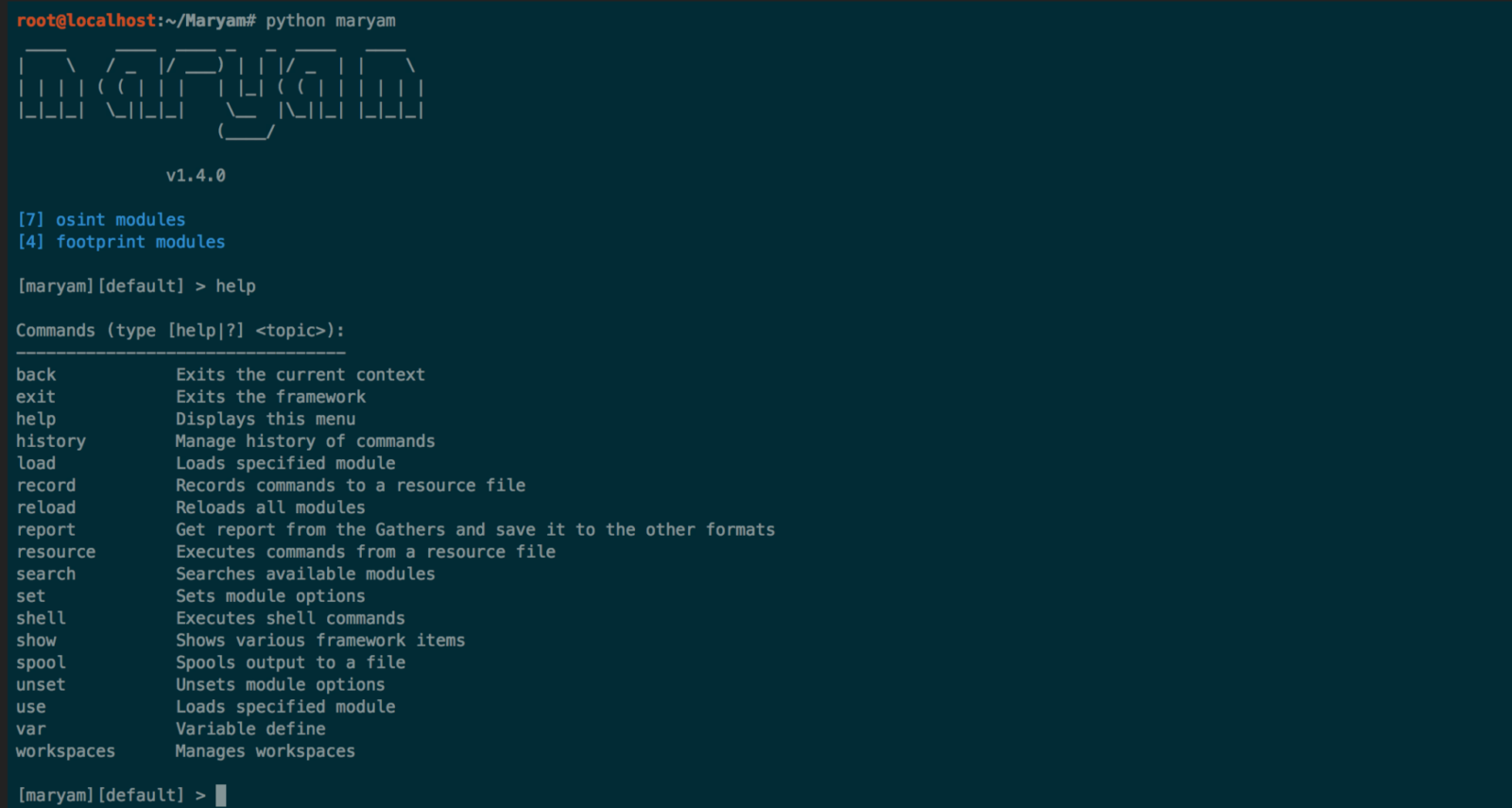
For help options
- write
helpor? - or write
help <command-name>for help your command
For show modules
- write
show modules
For use modules
- write
use <module-name>orload <module-name>
For show set options
- write
show options
For set an option
- write
set <option-name> <value> - for example
set VERBOSITY 2
For run selected module
- write
run
For add a variable
- write
var <$name> <value> - for example
var $hunter_key XXXXXXXXXXXXXXXX - for use, it writes
set HUNTER_KEY $hunter_key - for show, all of the variables write
var listcommand - for delete, a variable write
var delete <var-name>
For get report from modules output
- set ‘output’ option with True:
set output True - Or use ‘–output switch’:
wapps -d domain.com --output - And next, use
reportcommand:report <format> <file-name-for-output> <module-name> - For example
report <format> pdf_docs osint/docs_search localhost
For show history commands
- write
history all
For modules search
- write
search <string>
For record commands
- write
record start <file-name> - for stop it
record stop
For store all outputs
- write
spool start <file-name> - for stop it
spool stop
For run commands from file
- write
resource <commands-file-name>
For run shell command
- write
shell <command>or! <command>or<command>
For reload all modules
- write
reload
For config the connections
- see the options:
show options - and set the options:
set TIMEOUT 2.5
For use random user-agent
- write
set RAND_AGENT true
Examples
For search a RegExp to the web pages
python maryam
use footprint/crawl_pages
set url example.com
set regex https?://[A-z0-9\._\/\-?=]+If you want crawl in the more pages:set crawl True
If you want get keywords, emails and ..:set more True
get pdf files from search engine
python maryam
use osint/docs_search
set company EXAMPLE
set type pdf
set limit 5
set count 50
set metacrawler True
runDNS brute force
./maryam
use osint/dns_search
set dnsbrute True
set wordlist mylist.txt
set host example.com
runGet links and save data and get json report
./maryam
crawler -d <DOMAIN> --output
report json output_file_name osint/crawler
























Leave a Reply