
Karkinos – Penetration Testing and Hacking CTF’s Swiss Army Knife

What is Karkinos?
Karkinos is a light-weight ‘Swiss Army Knife’ for penetration testing and/or hacking CTF’s. Currently, Karkinos offers the following:
- Encoding/Decoding characters
- Encrypting/Decrypting text or files
- Reverse shell handling
- Cracking and generating hashes
Disclaimer
Use this tool to make penetration tests or any hacking CTF’s more efficient. This tool should be used on applications that you have permission to attack only. Any misuse or damage caused will be solely the users’ responsibility. Please check the known bugs and issues at the bottom before installation.
A Wiki page for troubleshooting is coming very soon.
More: https://github.com/helich0pper/Karkinos
Dependencies
- Any server capable of hosting PHP; tested with Apache Server
- Tested with PHP 7.4.9
- Python3
Make sure it is in your path as:
Windows:python
Linux:python3
If it is not, please change the commands inincludes/pid.php - pip3
- Raspberry Pi Zero friendly (crack hashes at your own risk)
Installing
This installation guide assumes you have all the dependencies.
Linux/BSD
git clone https://github.com/helich0pper/Karkinos.git
cd Karkinos
pip3 install -r requirements.txt
cd wordlists && tar -xf passlist.zipou can also unzip it manually using file explorer if tar is not installed. Just make sure passlist.txt is in wordlists directory.
Add extension=php_sqlite3.dll to your php.ini file.
If you don’t know where to find this, refer to the PHP docs.
That’s it! Now just host it using your preferred web server or run: php -S 127.0.0.1:8888 in the Karkinos directory.
Important: using port 5555 will conflict with the reverse shell handler server
If you insist on using port 5555, change the reverse shell handler server PORT value in /bin/Server/app.py Line 87
Windows
git clone https://github.com/helich0pper/Karkinos.git
cd Karkinos
pip3 install -r requirements.txt
cd wordlists && tar -xf passlist.zipYou can also unzip it manually using file explorer if tar is not installed. Just make sure passlist.txt is in the wordlists directory.Add extension=php_sqlite3.dll to your php.ini file.
If you don’t know where to find this, refer to the PHP docs.
That’s it! Now just host it using your preferred web server or run: php -S 127.0.0.1:8888 in the Karkinos directory.
Important: using port 5555 will conflict with the reverse shell handler server
If you insist on using port 5555, change the reverse shell handler server PORT value in /bin/Server/app.py Line 87
Demo
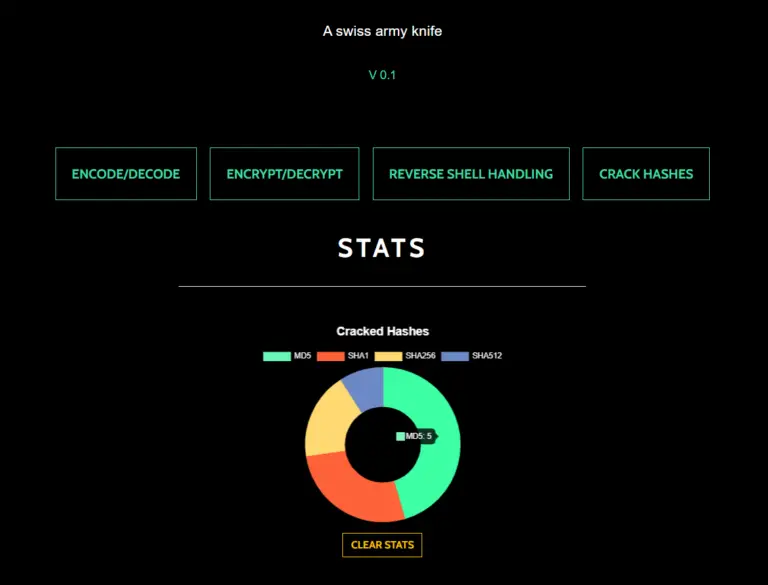
Home Menu
Landing page and quick access menu.
User stats are displayed here. Currently, the stats recorded are only the total hashes and hash types cracked successfully.
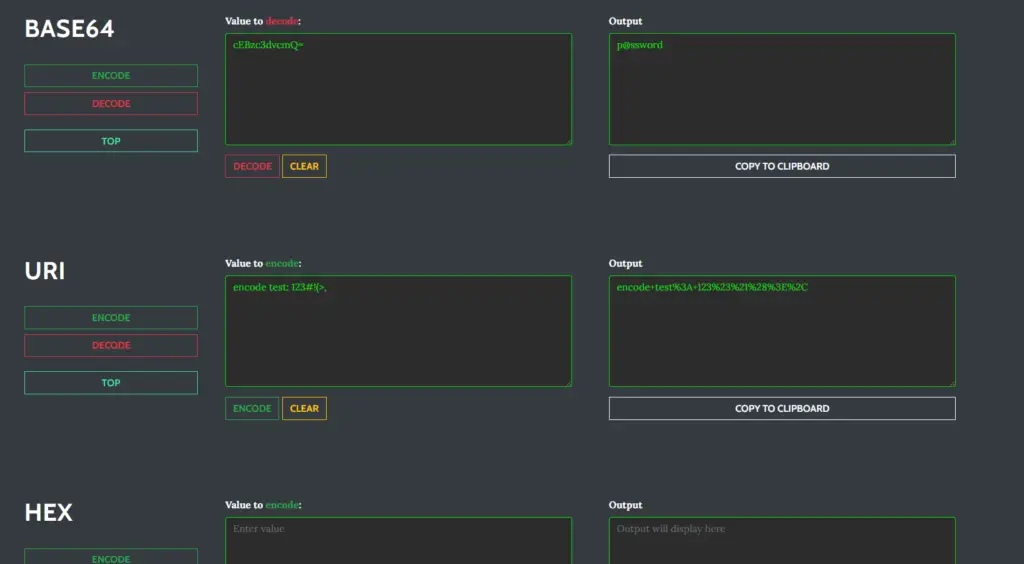
Encoding/Decoding
This page allows you to encode/decode in common formats (more may be added soon)
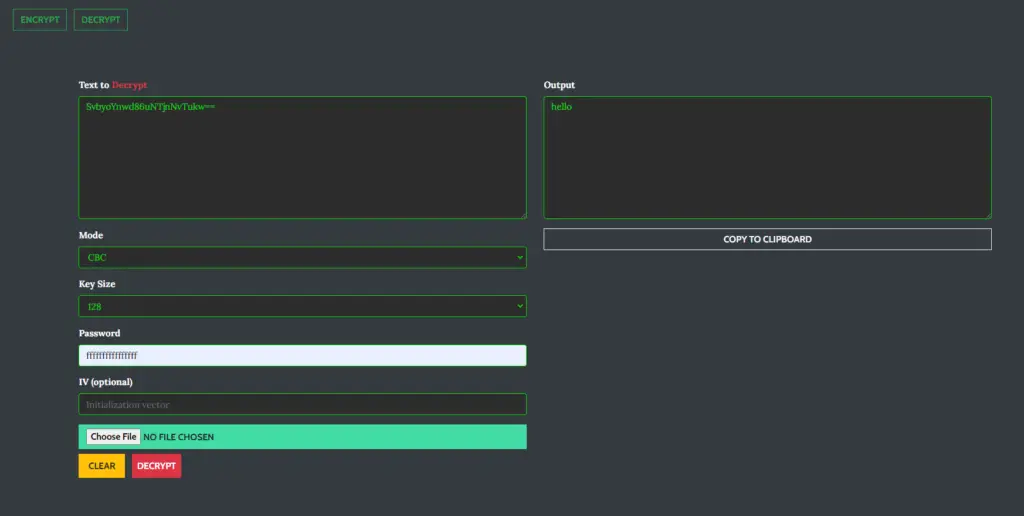
Encrypt/Decrypt
Encrypting and decrypting text or files is made easy and is fully trusted since it is done locally.
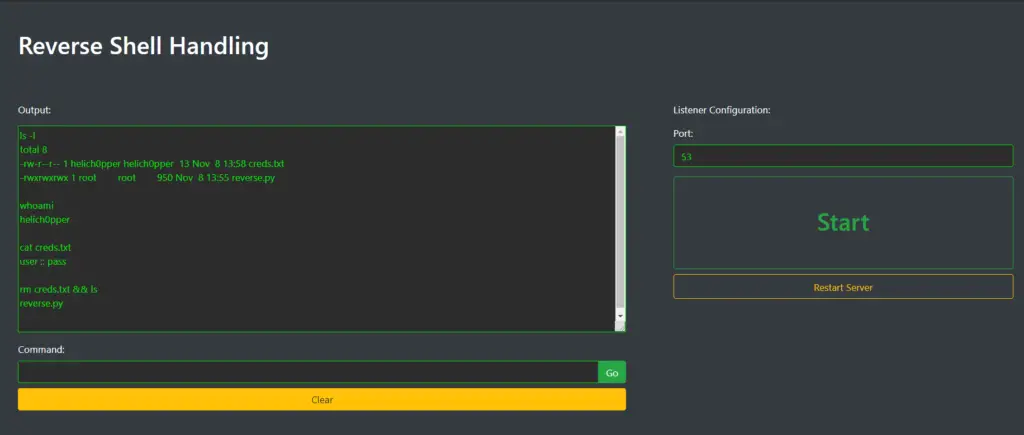
Reverse Shell Handling
Reverse shells can be captured and interacted with on this page.
Create a listener instance
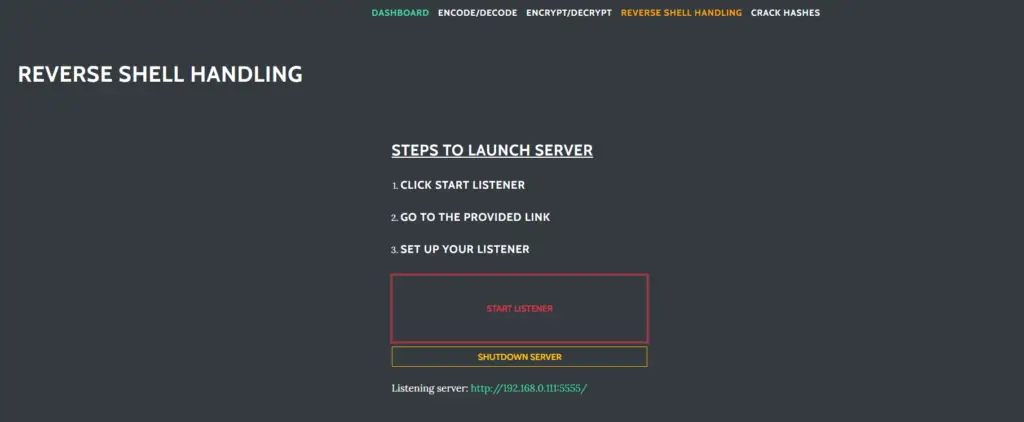
Configure the listener
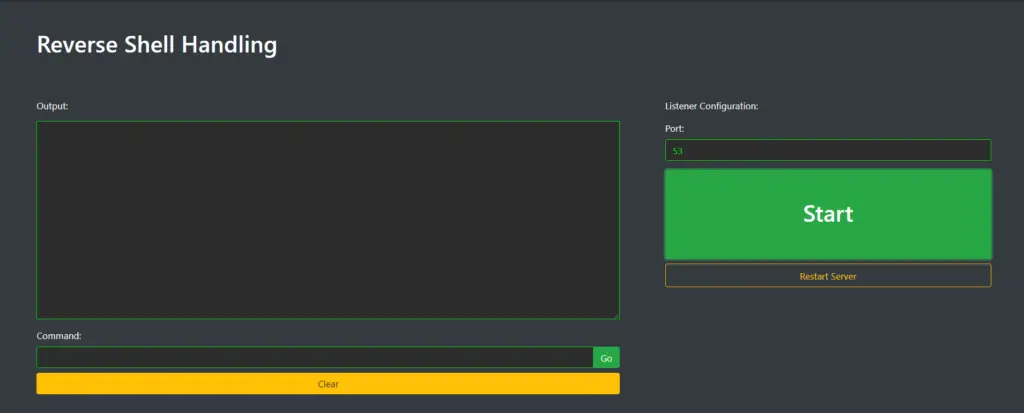
Start the listener and capture a shell
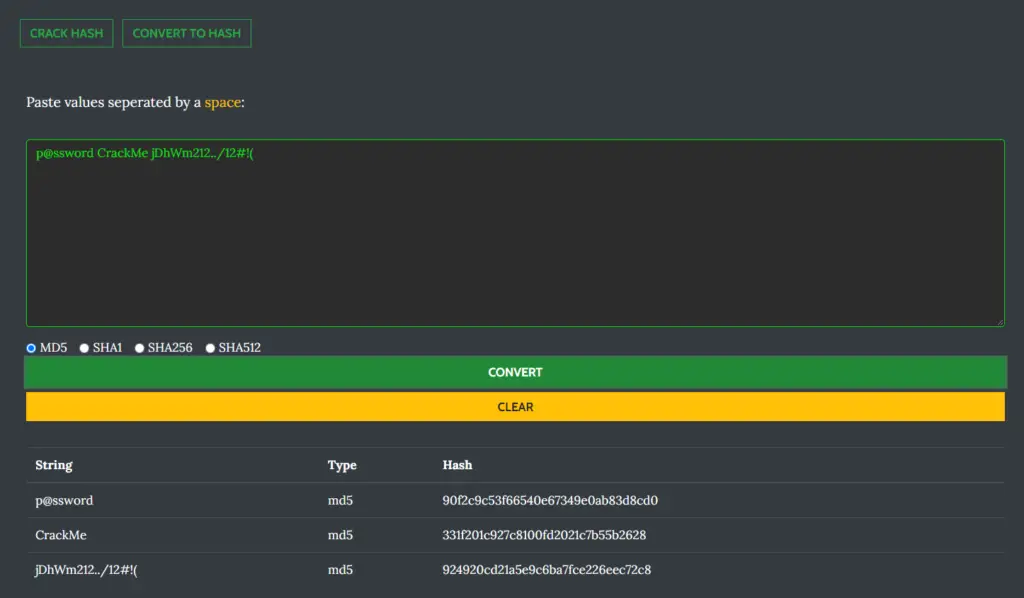
Generating Hashes
Karkinos can generate commonly used hashes such as:
- MD5
- SHA1
- SHA256
- SHA512
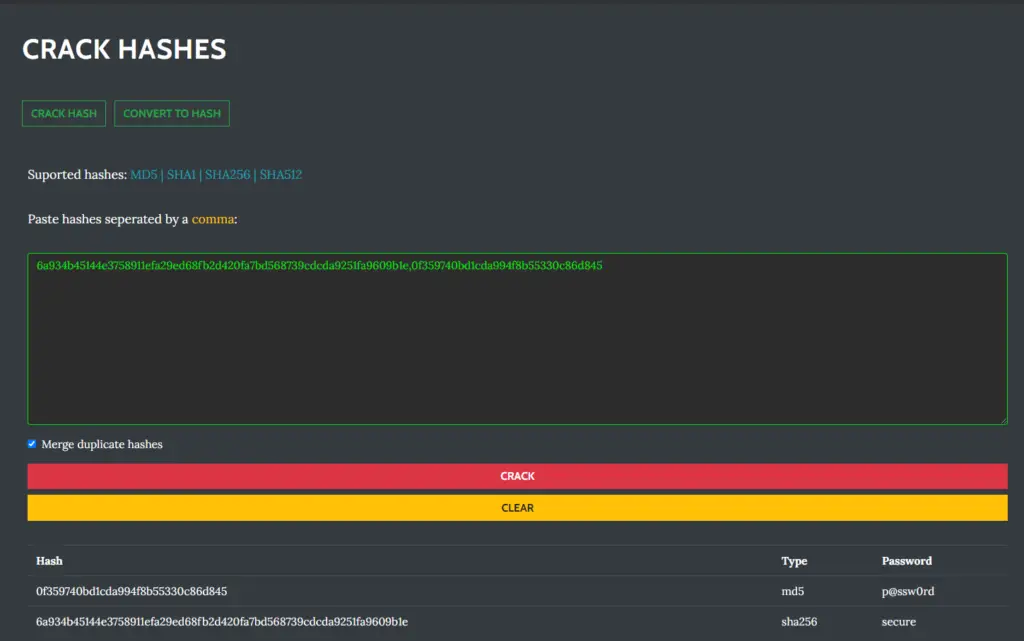
Cracking Hashes
Karkinos offers the option to simultaneously crack hashes using a built-in wordlist consisting of over 15 million common and breached passwords. This list can easily be modified and/or completely replaced.
Future Work
Pull requests and bug reports are always appreciated.
Below are known bugs and issues:
- Reverse shell handling server code is currently being reworked but it works fine
























Leave a Reply