

How to use Maltego like a pro by Anastasis Vasileiadis
Maltego is able to collect information about a network or an individual. Here we will focus on the first and leave the individual collection of information once again.
We will look at the collection of information for all subdomains, the range of IP addresses, the WHOIS information, all email addresses, and the relationship between the target domain and others.
Let’s start by running Kali and then opening Maltego.
Maltego can be found in many places in Kali, but the easiest way to get there is to go to Applications -> Kali Linux -> Top 10 Security Tools. Then, among the Top 10, you will find Maltego at number 5, as shown in the screenshot below.
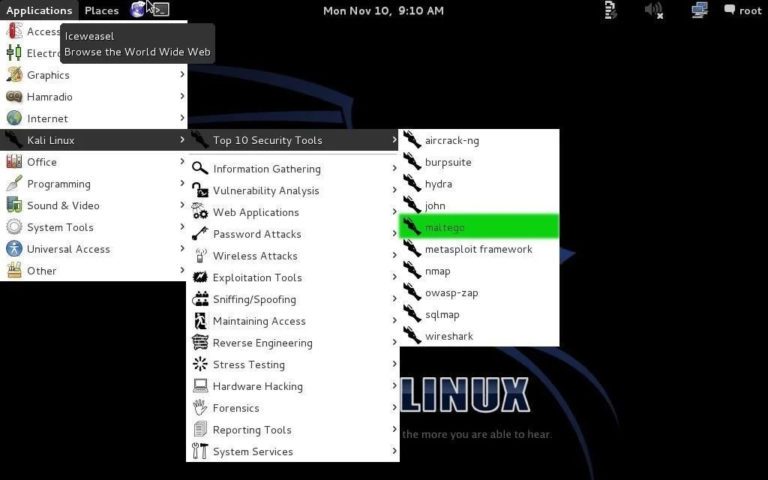
When you open Maltego, you have to wait a while for it to start. Once the upload is complete, you will be greeted by a screen asking you to sign up for Maltego.
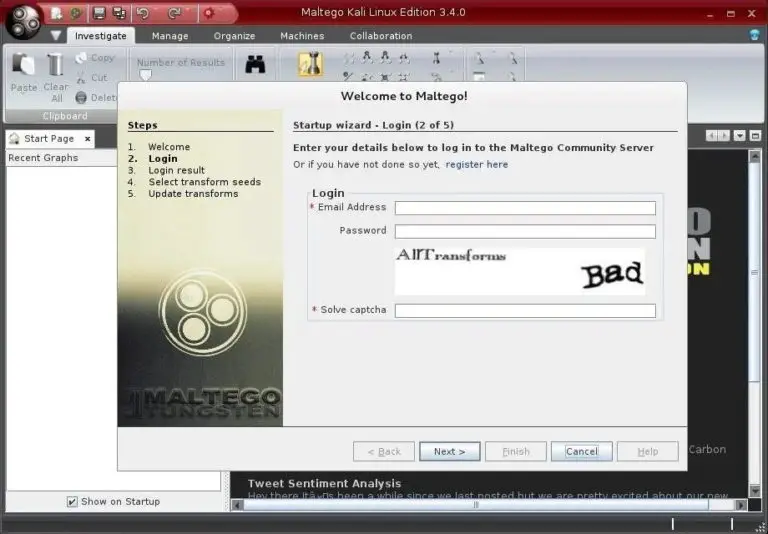
Go ahead, register and save your password, as you will need it again the next time you log in to Maltego.
Select attack and parameters
Once you have successfully registered and logged in to Maltego, you will need to decide what kind of “engine” you want to run against your target. In Maltego you have to choose what kind of footprinting you want to do against your target. Here, we focus on network footprinting, so our choices are:
- Company Stalker (collects email information)
- Footprint L1 (basic information collection)
- Footprint L2 (moderate amount of information collection)
- Footprint L3 (intensive and complete collection of information)
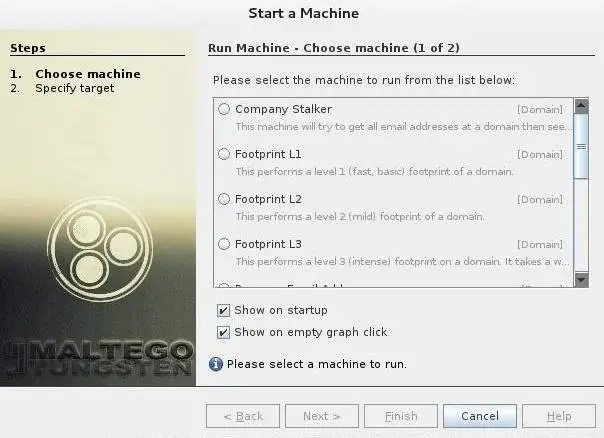
Let’s choose the L3 option that will gather as much information as possible. Although it is the most time consuming choice.
Choose a goal
Now that we have chosen a type of machine for our footprinting, we need to choose a target. Let’s choose our friends at GLUTEN , one of the leading security training and consulting companies in the world.
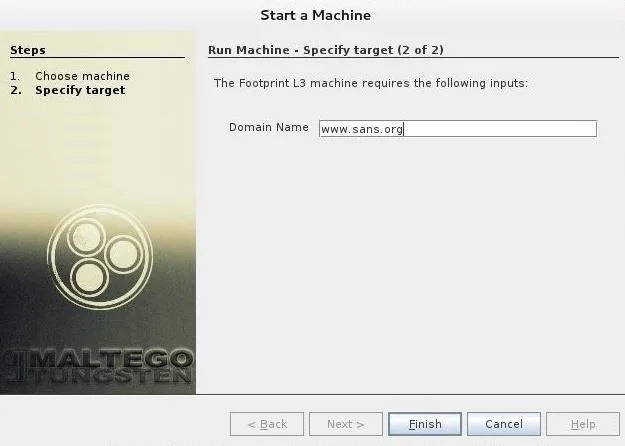
Now, click “Finish” and let Maltego do its job.
Results
Maltego will start collecting information about our target on sans.org and displaying it on the screen. In the screenshot below, we can see that Maltego has already collected the email addresses from the site, while collecting the name servers and mail servers.
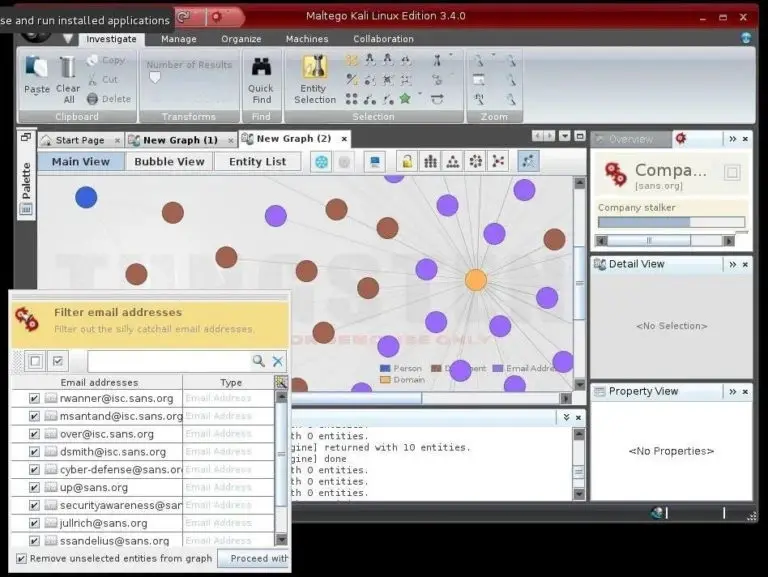
Finally, we can click on “Bubble View” when Maltego is completed and see all the relationships between our target and its subdomains, as well as the linked sites.
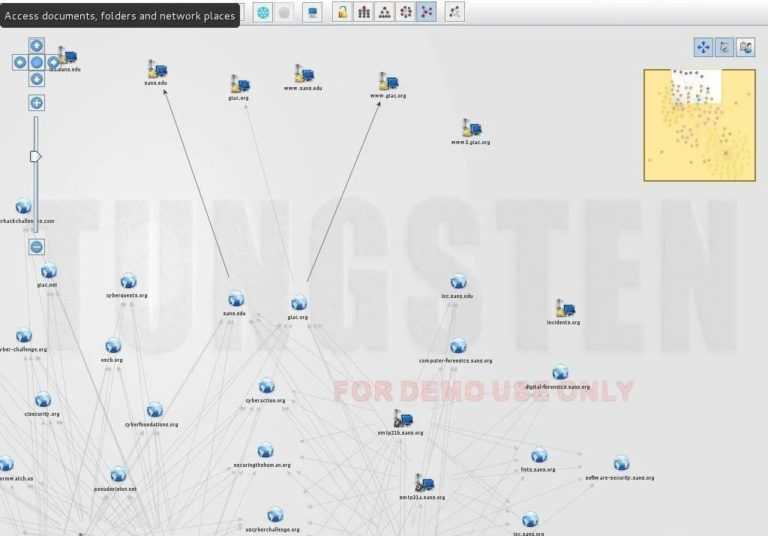
Maltego is a great tool to do network authentication on our potential target, allowing us to do many types of authentication in a single tool scan.
Finally Maltego is also capable of recognizing people, but we’ll leave that for our next iguru article.
Originally posted at: https://en.iguru.gr/2020/08/10/pos-chrisimopoiisete-maltego-san-epangelmatias/
About the Author : Anastasis Vasileiadis
PC Technician, Penetration Tester, Ethical Hacker, Cyber Security Expert, Malware Analyst, Information Security Researcher, Reverse engineering.


























Leave a Reply