
Step by step encrypt the Azure VM Disks
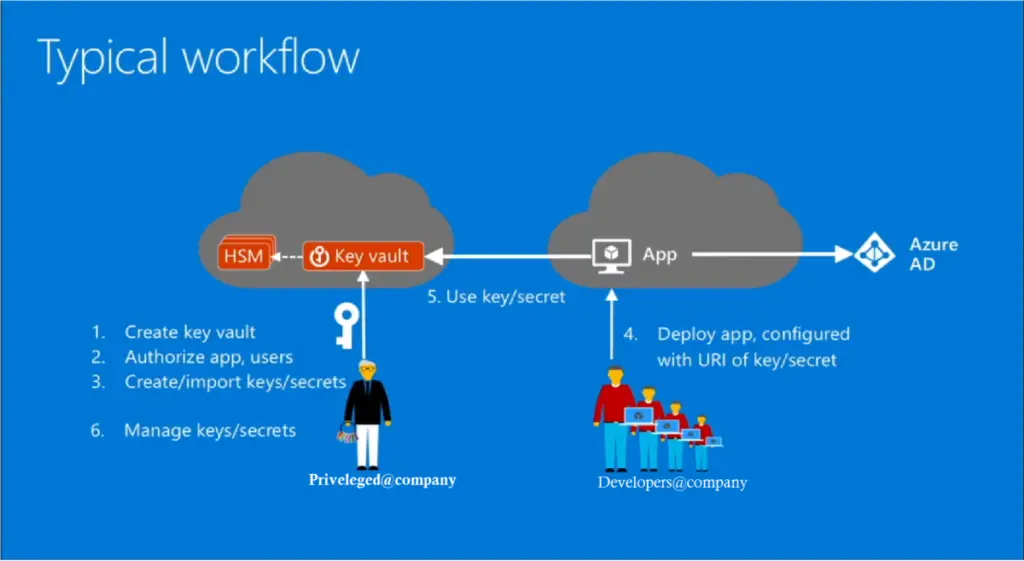
Today I will show you how we can encrypt the disks of an azure VM. Encrypion of VM now a days becoming a compliance requirement and all the enterprises are following one or the other way to encrypt their servers. Azure Disk Encryption helps protect and safeguard your data to meet your organizational security and compliance commitments. It uses the Bitlocker feature of Windows and Dm-Crypt feature of Linux. It is also integrated with Azure Key Vault to help you control and manage the disk encryption keys and secrets, and ensures that all data on the VM disks are encrypted at rest while in Azure storage.
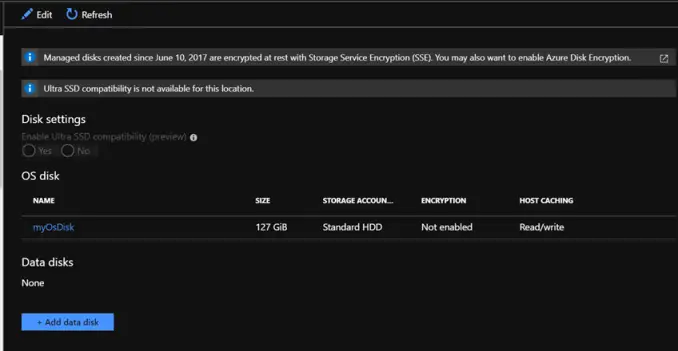
Now let’s see the steps here. As you can see below I have one small VM which I have created for this PoC. The VM is currently having only one disk, which is the OS Disk of the VM.
Once I RDP to the VM, I can see that the VM Disks were un encrypted as you can see below.
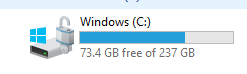
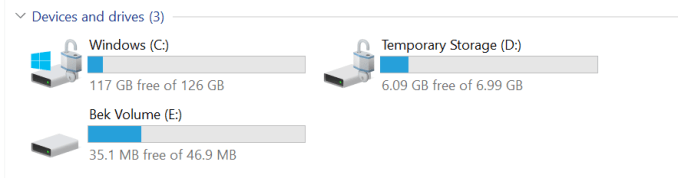
An encrypted disk will look like this with a lock icon.
From the Azure Portal Also you can setup the policies on the Key vault as you can see below
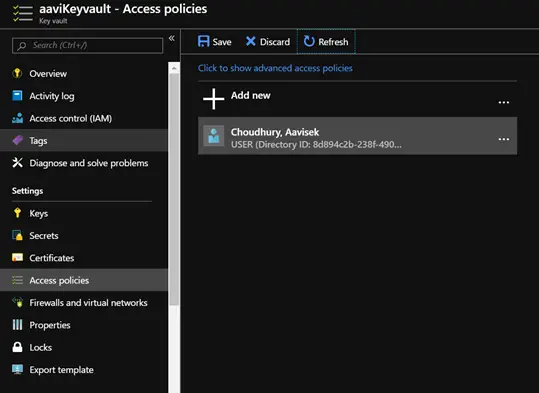
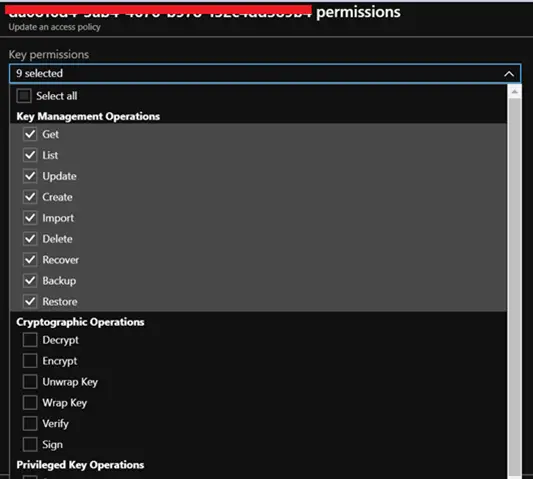
I have enabled the encrypt operations from the portal.
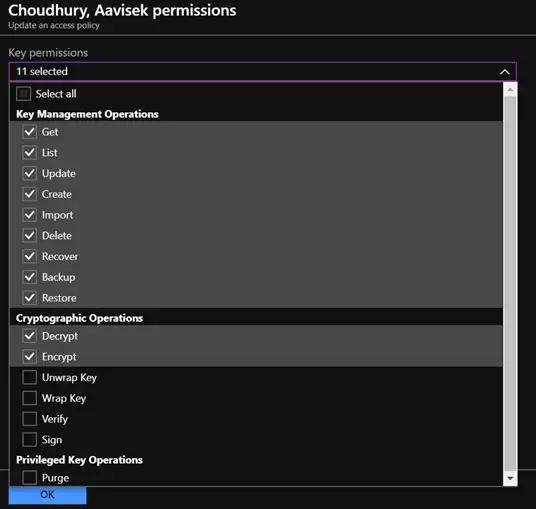
You need to enable advances access policies.
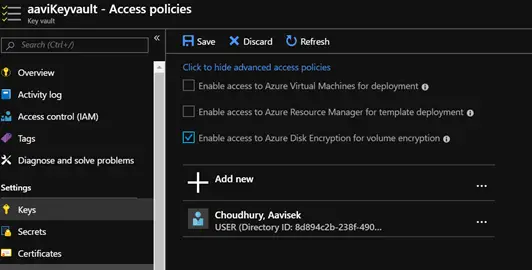
The same policy can also be applied through Powershell as you can see below

Set-AzKeyVaultAccessPolicy -VaultName $keyVaultName –EnabledForDiskEncryption
This switch parameter above will help in encrypting the disk.
-EnabledForDiskEncryption
Enables the Azure disk encryption service to get secrets and unwrap keys from this key vault.
| Type: | SwitchParameter |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Once everything is done in next steps I will show you how you can encrypt your VM with help of PowerShell as you can see below.
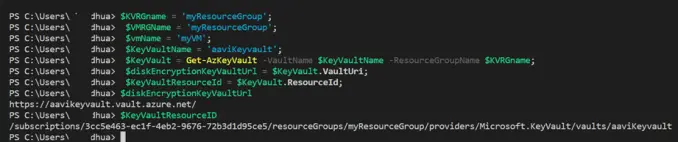

The same can be done with the help of the Azure CLI
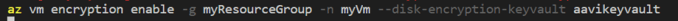
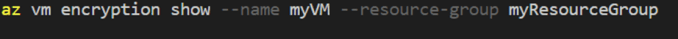
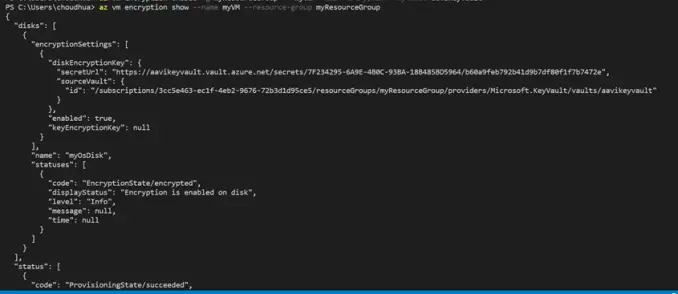
Once the encryption is done you should be able to see the JSON file. You can see this by running the below command.
Please check the displaystatus which is showing “Encryption is enabled on disk”
When your compliance and security requirement requires you to encrypt the data end to end using your encryption keys, including encryption of the ephemeral (locally attached temporary) disk, use Azure disk encryption. Alternatively, by default, Managed Disks are encrypted at rest by default using Azure Storage Service Encryption where the encryption keys are Microsoft managed keys in Azure. If this meets your compliance and security requirements, you can leverage the default Managed disk encryption to meet your requirements.
Once the disks are encrypted you can see the icons like this.
That’s all for today, I will bring more posts on Azure Security in future.





























Leave a Reply