

Goblyn is a Python tool focused to enumeration and capture of website files metadata.
Metadata Enumeration
What’s Goblyn?
Goblyn is a tool focused to enumeration and capture of website files metadata.
How it works?
Goblyn will search for active directories in the website and so enumerate the files, if it find some file it will get the metadata of file.
Why Goblyn?
- Supports multiple file types;
- Simple to use;
- Easy installation;
- Fast.
Installing Goblyn
- Download this repository and run:
sudo python3 setup.py install
- Download the
exiftool:
sudo apt install exiftool
- Have fun 🙂
sudo goblyn [OPTIONS]
How to use Goblyn?
You can use the -help argument to explore help banner of Goblyn.
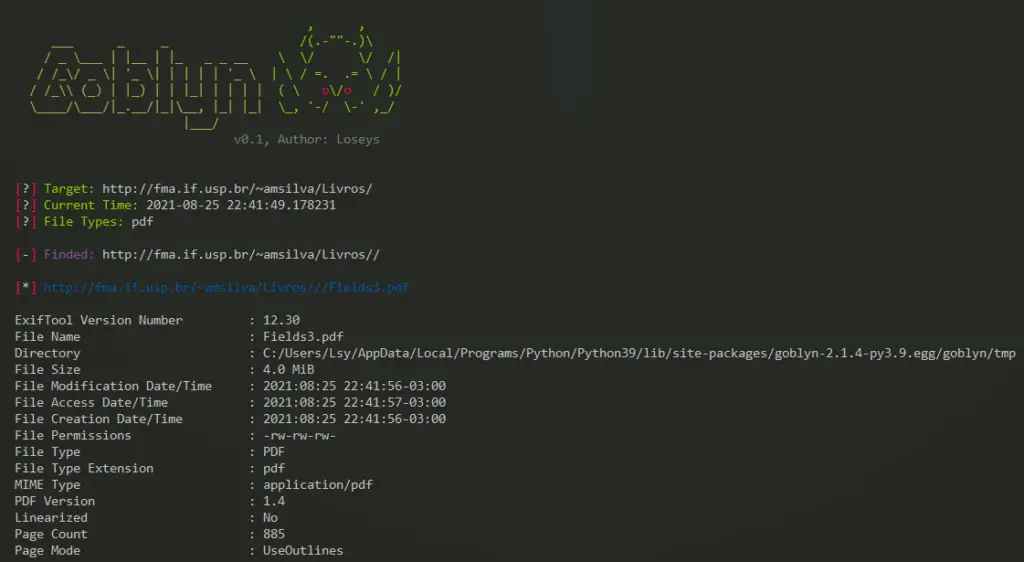
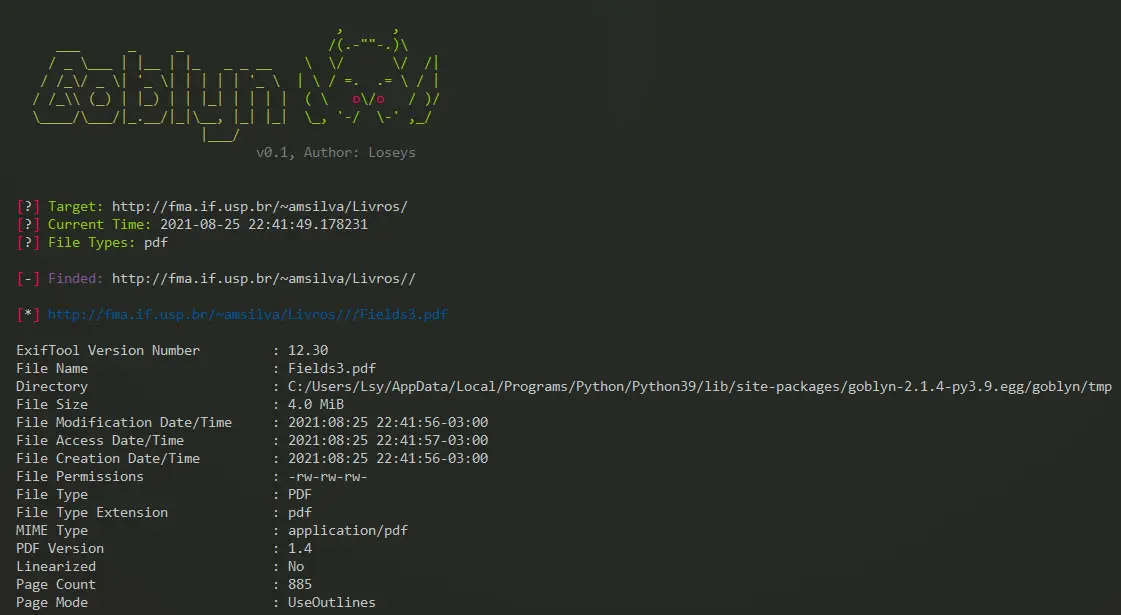
Example of use:
sudo goblyn -t http://fma.if.usp.br/~amsilva/Livros/ -wl C:\Users\Lsy\Desktop\common.txt --file-types=pdf,docx,png
Call for Contributions
If you finds this tool useful and wants to add some functionality, improve the code performance or improve something in the Goblyn, the best way to get it added is to submit a pull request.

























Leave a Reply