

7-Zip through 21.07 on Windows allows privilege escalation and command execution when a file with the .7z extension is dragged to the Help>Contents area.
The CVE-2022-29072 POC is a github repository by Kağan Çapar
About 7-zip
7-Zip is a free and free file archiver. The Command Prompt version of 7-Zip is designed for Unix-like systems, including AmigaOS. It can also be run for DOS compatible Friendly Port or in Windows Command Prompt with HX-DOS extender.
CVE-2022-29072
I will write in Turkish and you learn some Turkish.
First of all, I would like to talk about my story of finding vulnerability. I saw a payload that made the XXE vulnerability on WinRAR. At the same time, it was possible to run commands via ActiveXObject and WScript.Shell via javascript using the HTML Helper file. This was no different from the HTA used in lolbins, I thought about how I could turn the situation in my favor.
https://www.exploit-db.com/exploits/47526
Actually, my aim was to get reverse-shell on the target computer after double-clicking on the extensions of compression technologies such as 7z, zip, rar etc. I was thinking if I could use the HTML Helper file in this. After long fuzzing processes with WinAFL, I discovered that there was heap-overflow on FzGM.exe, but it didn’t make any sense since my authority after heap overflow would be over the same user. That’s why I didn’t use CreateRemoteThread because I needed to call the API and I needed a chm file to be able to trigger this API. When I examined the source code, I noticed that there were erroneous operations, especially when calling the Windows API in two places, and this created a direct authorization problem. This discovery point creates a child process under FzGM.exe as seen in the picture below. Normally this process hh.
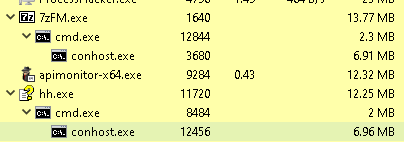
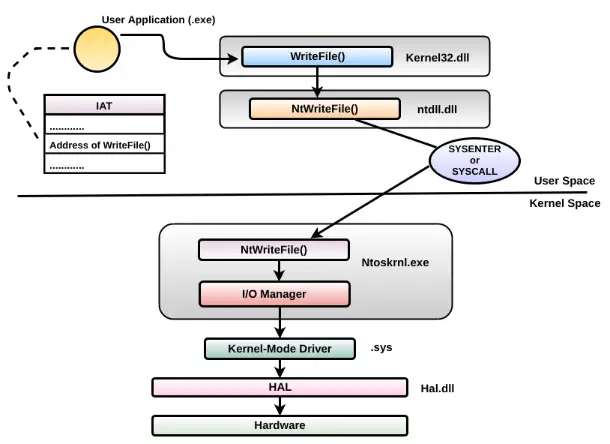
If the API was not included and there was a correct configuration through the function, I would expect it to create a child process under hh.exe, but the 7-zip.chm file calls it through itself. You can see a typical example if you edit the 7-zip.chm file and execute the command at that time. After the authorization problem of the API called after heap overflow, I took advantage of the misconfiguration in the 7z.dll file, which I have been dealing with for a long time. There’s no point in doing CreateRemoteThread() . What I need to run and call inside the payload is not the HTML Helper API itself, but the point where this API is hooked over 7-zip and I can execute that point, but this payload only works with hh.exe integration, so it’s like drag and drop. works with function. 7-zip. Calling the chm file with the HELP button over 7-zip and redirecting the “base pointer”, which has an authorization problem in the payload of the address called here, moves us to a higher user. The next step is to find psexec in the payload and raise it to system authority as nt authority/system with the psexec -s cmd.exe command.
Demo
ActiveXObject bypass hakkında
Most of the questions were about ActiveX warning. The most basic of this problem is you can fix it like this. Before Payload works;
<‘HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0’ -Name ‘1201’ -Value ‘0’ -PropertyType “DWord”> provides control if this value is 1, popup is displayed if 0 is new If a value is assigned, it is bypassed. But it should be noted that it affects whichever user payload is running at that moment.
Important note
I explained the necessary points to the developer and this was accepted by the CVE. I can’t understand the perception that people think they are the authority and I have to give them the exploit. Although I have already stated that I will publish after the update, I think this disrespect without the update is due to seeing yourself as an authority. I may never want to publish the poc code of the escalation attack, it’s my free will and I don’t care what anyone thinks about questioning the accuracy of this.
Action to be taken
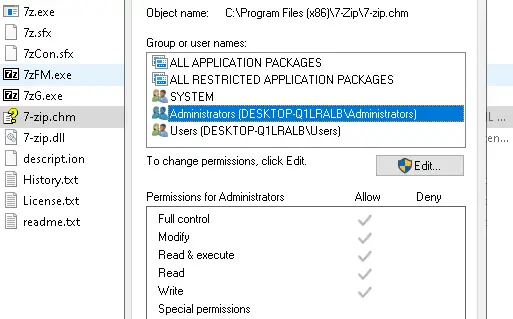
Method one: If the 7-zip update does not go through, the 7-zip.chm file can be deleted. Second method: All users in the program must access with read and execute permissions.
Sigma rule
Related sigma rule
https://github.com/kagancapar/CVE-2022-29072/blob/main/7z_CVE-2022-29072.yml

























Leave a Reply