

Run all your bug bounty VPN profiles in parallel and expose them via multiple local SOCKS proxies.
Description
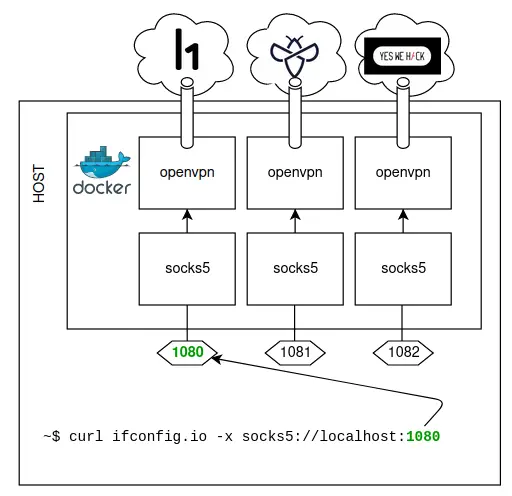
This project uses Docker to run multiple VPN tunnels simultaneously from the same machine, and exposes a SOCKS proxy for each separate VPN connection.
Setup
git clone https://github.com/honoki/bugbounty-openvpn-socks
- Edit the
.envfile with your platform credentials- Note – If your password or mail address contains a dollar character, you need to escape it with 3 backslashes, e.g.
pas$w0rdbecomespas\\\$w0rd. - If you want to allow unauthenticated access to your SOCKS proxy, remove the
PROXY_USERNAMEandPROXY_PASSWORD
- Note – If your password or mail address contains a dollar character, you need to escape it with 3 backslashes, e.g.
- Download the
ovpnfiles of each platform to the corresponding/vpn/<platform>folder:- Hackerone: https://hackerone.com/settings/vpn
- Intigriti: ?
- YesWeHack: https://yeswehack.com/user/vpn
docker-compose up
- Check that the VPN connections are working:
curl ifconfig.io # direct
curl ifconfig.io -k -x socks5://username:password@localhost:1080; #hackerone
curl ifconfig.io -k -x socks5://username:password@localhost:1081; #intigriti
curl ifconfig.io -k -x socks5://username:password@localhost:1082; #yeswehack
SOCKS5
The SOCKS5 proxy ports will be available on:
localhost:1080for the Hackerone VPN;localhost:1081for the Intigriti VPN;localhost:1082for the YesWeHack VPN;
Below is a selection of tools that have SOCKS proxy support out of the box:
nuclei -proxy-socks-url socks5://username:password@localhost:1080
ffuf -x socks5://username:password@localhost:1080
curl -x socks5://username:password@localhost:1080
If you are using tools without built-in proxy support, you can use proxychains to force everything through the proxy regardless.
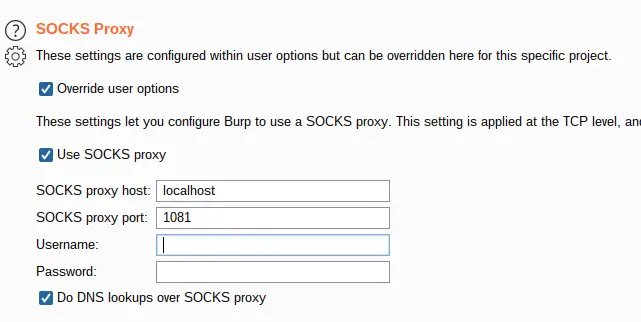
Burp Suite
You can use the SOCKS proxy to tunnel Burp traffic through the VPN via “Project options”:
BBRF
If you’re a BBRF user, you will not be surprised to learn this integrates nicely. BBRF v1.2 contains some additional features to store and use proxy configurations.
First, I recommend deploying this project on a public VPS. (It runs nicely alongside BBRF Server if you have it deployed!) Please make sure to set up authentication on your SOCKS proxies by editing the PROXY_USER and PROXY_PASSWORD variables in .env.
After that, configure your proxy settings in BBRF as follows:
bbrf proxy set hackerone socks5://user:pass@yourserver.com:1080
bbrf proxy set intigriti-1 socks5://user:pass@yourserver.com:1081
bbrf proxy set yeswehack socks5://user:pass@yourserver.com:1082
bbrf proxy set intigriti-2 socks5://user:pass@yourserver.com:1083
Now you can update or create a program’s proxy settings with a custom tag proxy as follows:
bbrf program update my_hackerone_program -t proxy:hackerone
bbrf new secret_program -t proxy:intigriti-1
Now update your automation scripts to always send traffic through the right tunnel, e.g.:
# use the vpn config in whatever tool you're running
# note that the use of double quotes will allow this
# to work even if `bbrf proxy` returns an empty string
curl -x "$(bbrf proxy)" ifconfig.co


























Leave a Reply