
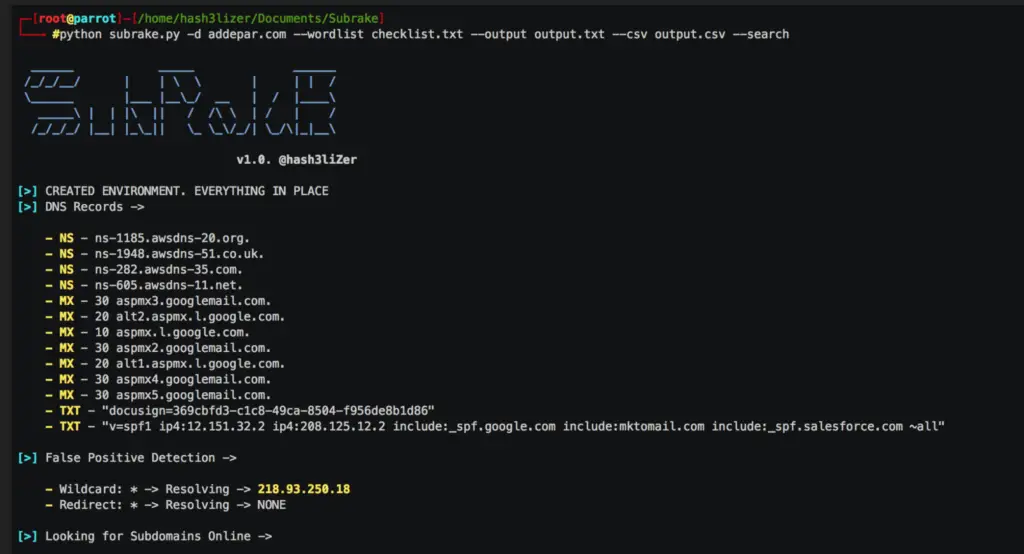
Subrake – A powerful Subdomain Scanner & Validator for Reconnaissance
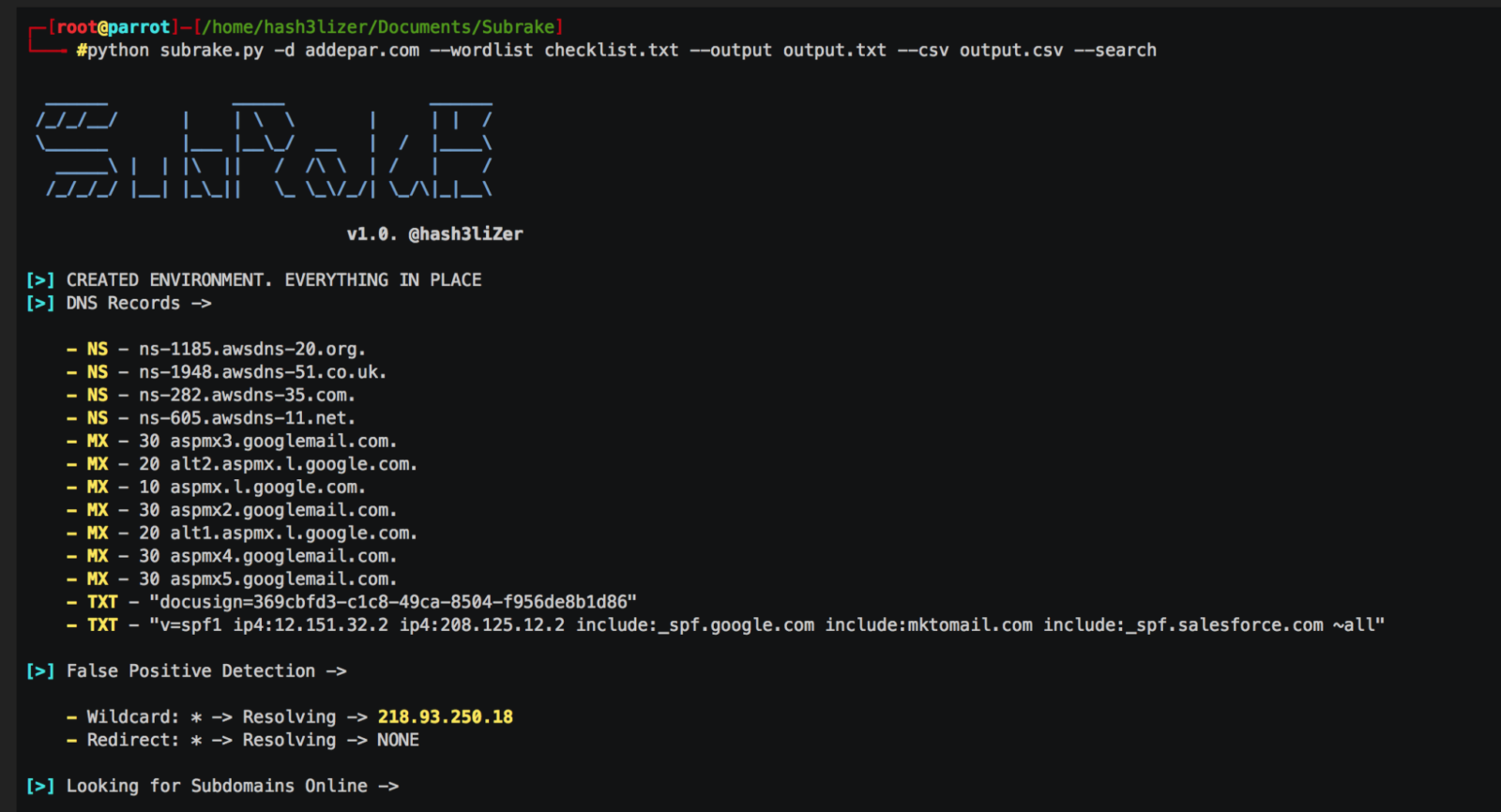
Subrake – A Powerful Subdomain Scanner & Validator Written in sockets and requests which makes it a lot more faster and easier to manage. It works by enumerating subdomains by searching them on web and by using local wordlists. It further identify the assets of a domain based on their ip and CNAME records and identify subdomains which are using the same IP addresses. It also scan ports if are given and enumerte possible server engines used on assets using the SERVER header returned in the response. It also enumerates possible returned HTTP status codes on port 80 and 443.
Key Features of Subrake
- Use built-in low level sockets to connect subdomains and other assets
- Search Subdomains Online on the Web.
- Validate Subdomains Using associated IP address.
- Identify False Positives.
- Internal Filtering using –filter option
- Store data in plain text and CSV formats.
- Built-in Port Scanning
- Fitering Into More Results by Removing False Positives.
Installation
Install the required modules from requirements.txt file:
$ pip install -r requirements.txtYou can take a start by cloning the source.
$ git clone https://github.com/hash3liZer/Subrake.git
$ cd Subrake/
$ python subrake -d yourdomain.tld -w wordlists/small.lstOptions
Syntax:
$ python subrake -d shellvoide.com -w [ Sublister Output ]
$ python subrake -d shellvoide.com -d shellvoide.com --wordlist wordlist/small.lst --filter --csv output.csv
Options:
Args Description Default
-h, --help Show this manual NONE
-d, --domain Target domain. Possible
example: [example.com] NONE
-w, --wordlists Wordlists containing subdomains
to test. Multiple wordlists can
be specified. NONE
-t, --threads Number of threads to spawn 25
-o, --output Store output in a seperate file NONE
-c, --csv Store output in CSV format NONE
-p, --ports Comma-seperated ports to scan. NONE
Depends on --scan-ports.
-s, --search Search for subdomains Online FALSE
--filter Filter subdomains with same IP FALSE
--scan-ports Turns on the port scanning
feature FALSE
--exclude-ips Exclude foll Ip Addresses from
Results. NONEExamples
Here are some of common examples of Subrake:
$ python subrake.py -d shellvoide.com --wordlist wordlists/small.lst
$ python subrake.py -d google.com -t 30 -o output.txt -f --search -w myrandomlist.txt
$ python subrake.py -d starbucks.com -w wordlists/small.lst -t 30 -o output.txt --csv output.csv --scan-ports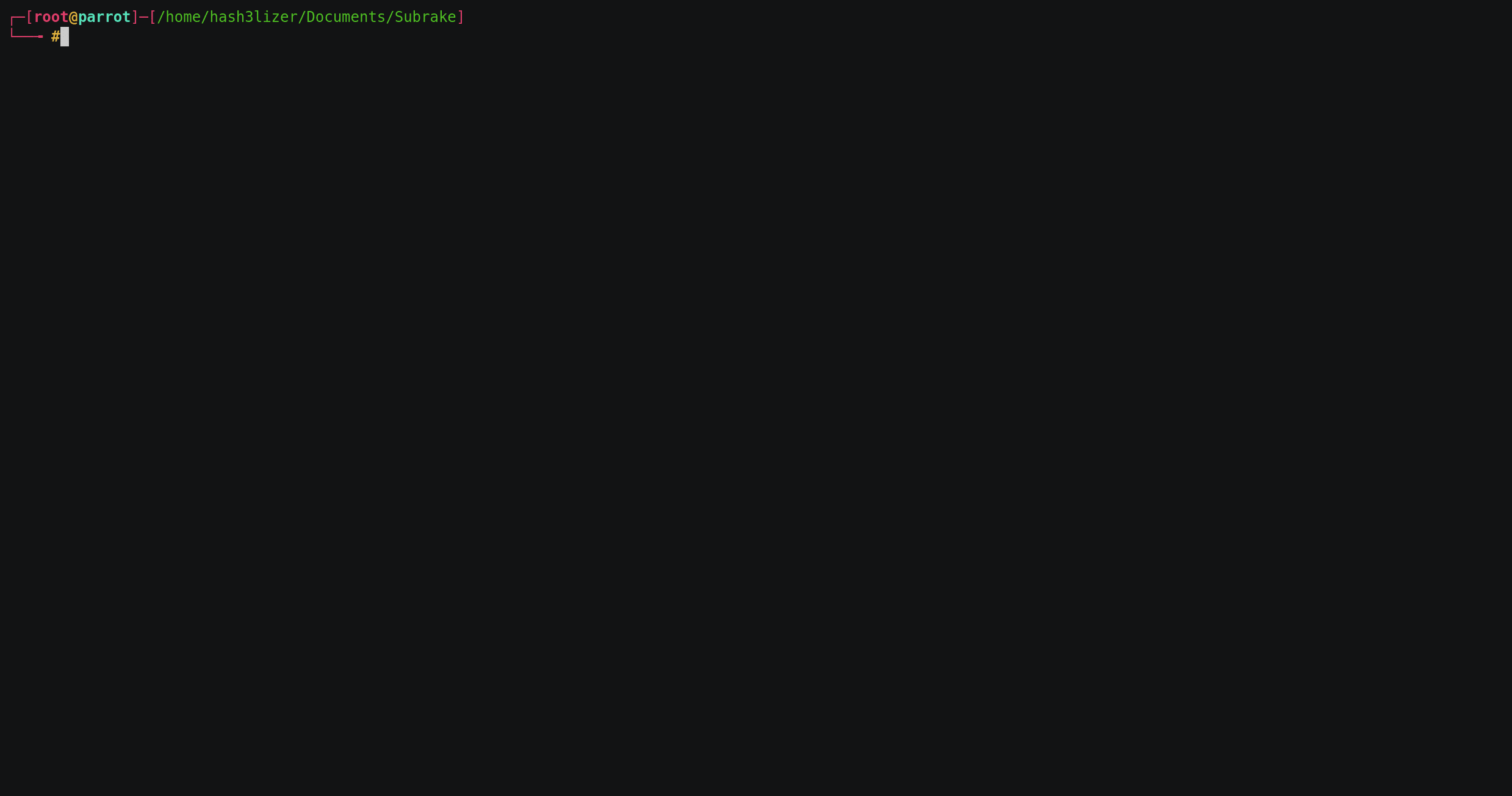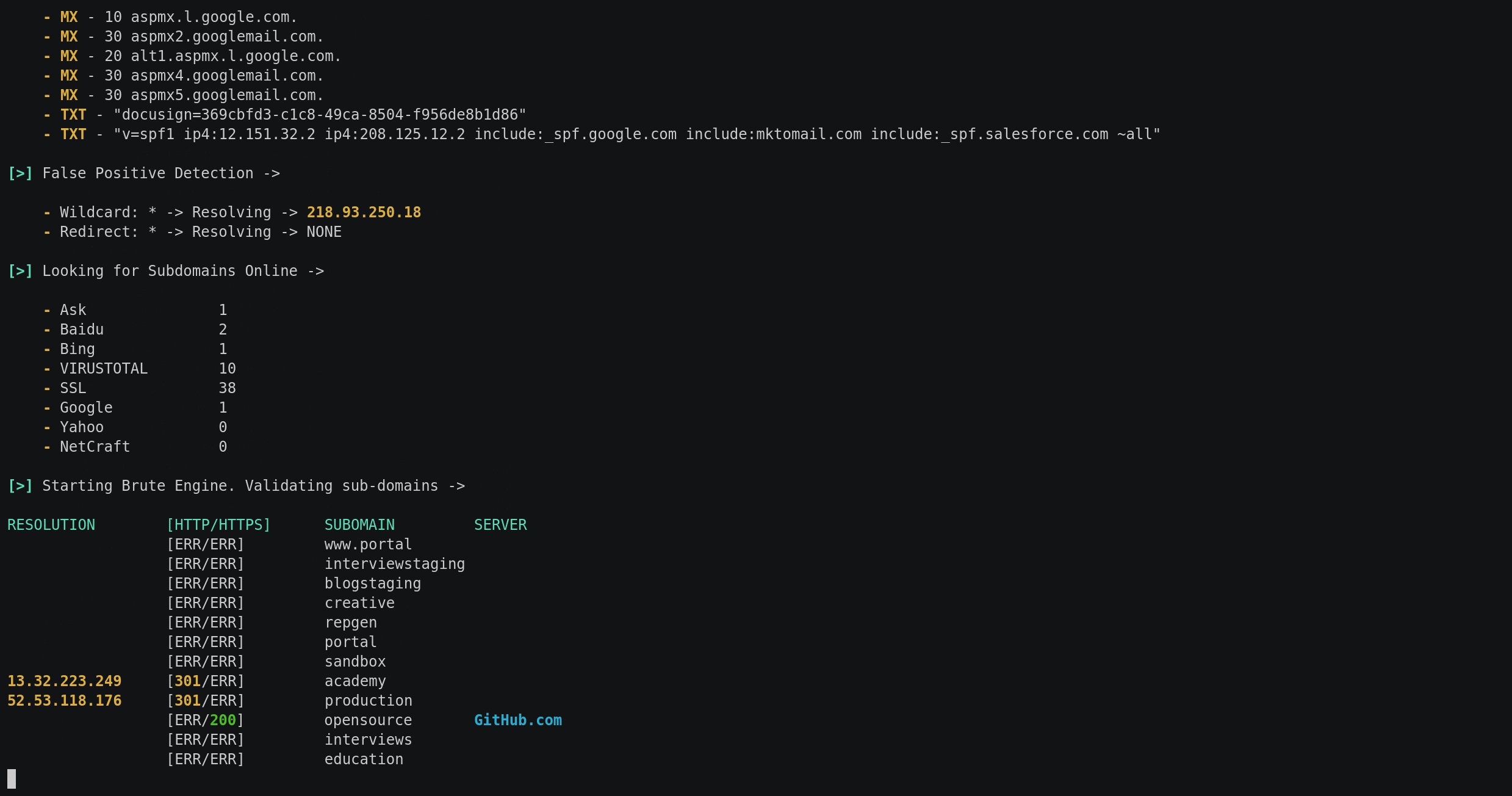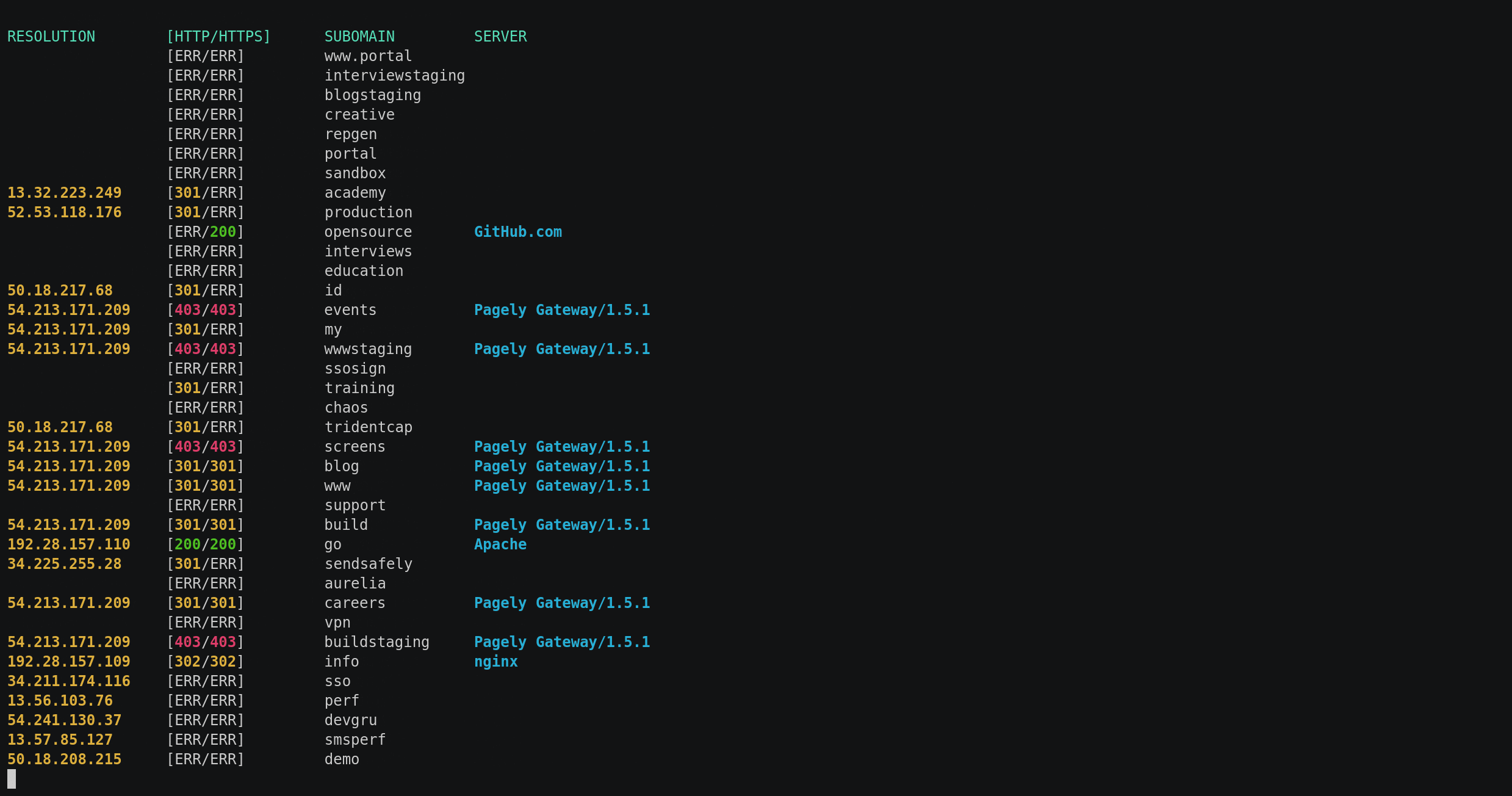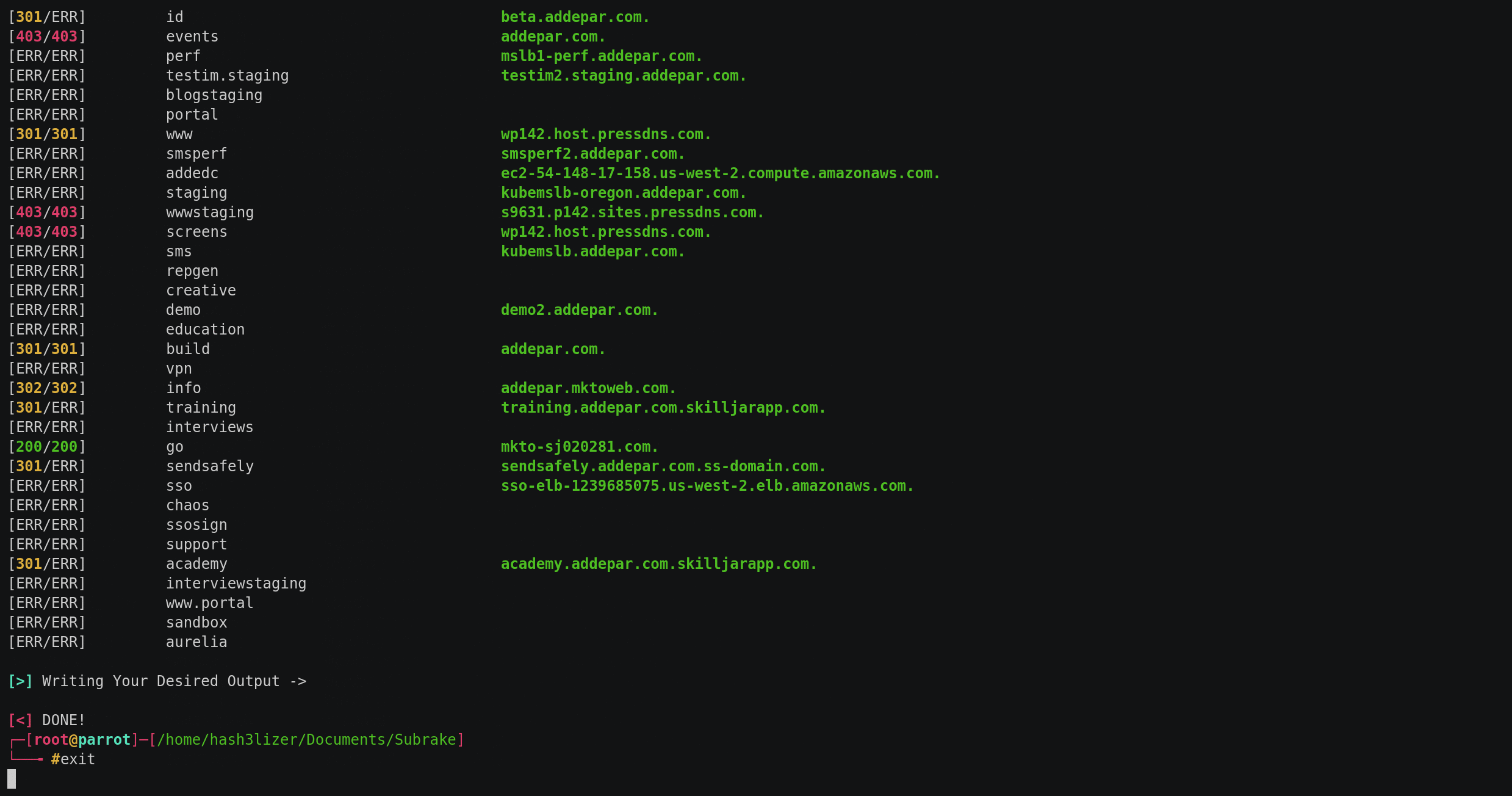
Contribution
You can contribute to the project in many ways:
- Report Bugs
- Fork the project and start building on your own.
- Suggestions for making it better
























Leave a Reply