
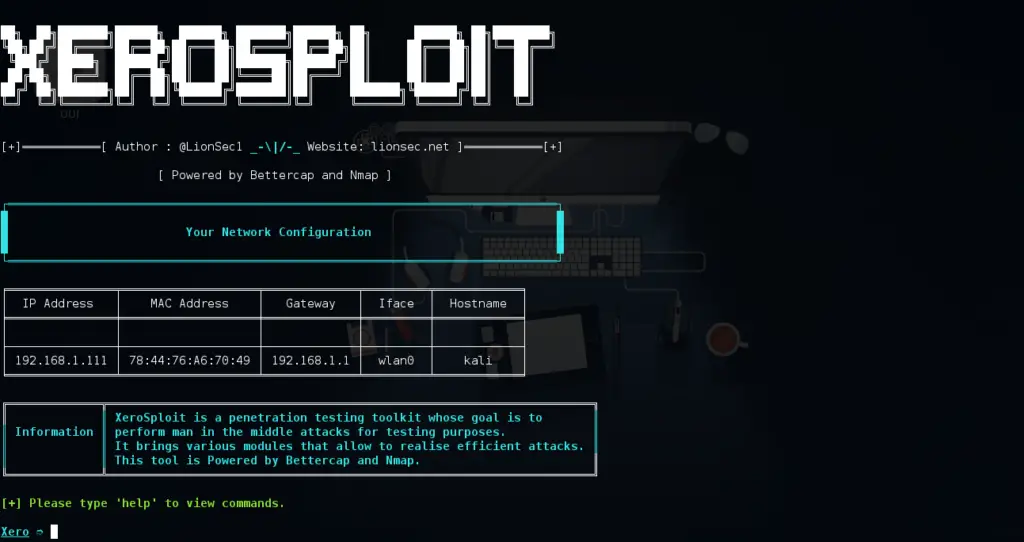
Xerosploit – Efficient and Advanced Man-In-The-Middle Framework
Xerosploit is a penetration testing toolkit whose goal is to perform man-in-the-middle attacks for penetration testing purposes. It brings various modules together that will help you perform very efficient attacks. You can also use it to perform denial of service attacks and port scanning.
Dependencies
- nmap
- hping3
- build-essential
- ruby-dev
- libpcap-dev
- libgmp3-dev
- tabulate
- terminaltables
Installation
You can download this tool by typing the given command in your terminal or you can download it by clicking here.
git clone https://github.com/LionSec/xerosploit.git
The following are some commands which will be used in this attack:
- scan: To scan your Local network.
- run: To execute the module
- back: To exit from a particular module
- help: To see all the available modules of this tool.
Once your download is completed, you have to install this tool by typing.
cd xerosploit/ls./install.py1
This will install the tool in your Kali. After successful installation of xerosploit tool, type
./xerosploit.py
to run it.
To scan your network, type scan This command will display all the devices which are connected to your network, and you can perform this attack on any of them.
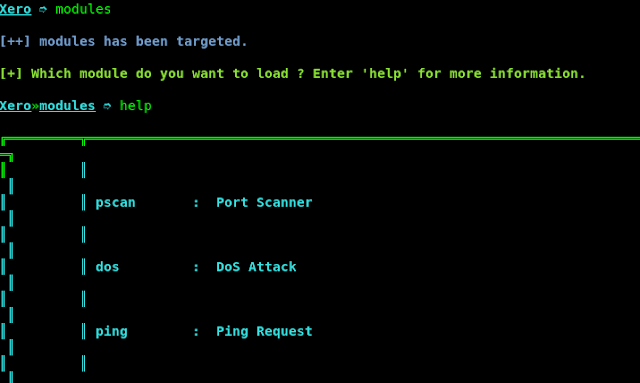
Type help to see all the modules which you can execute. Type modules and check the modules by using the help command. See the screenshot below:
As you can see, there are so many modules which can be used to attack windows machine. You can use any of them by simply typing the name of the module (which you want to use), and then type run to execute that module.
pscan run
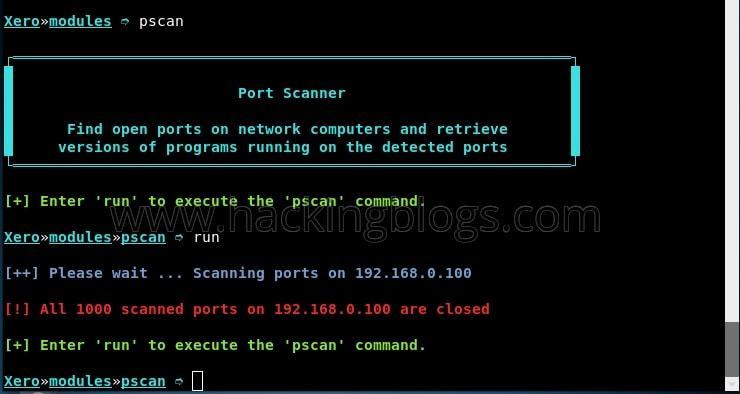
As you can see, I don’t have any open ports in my windows. Now type back to exit this module.There are some more interesting modules which can be used. It’s a very simple and user-friendly tool.
Here is the explanation of all the modules of this tool.
pscan: It scans all the ports of the victim’s machine, and shows you a list of all the open ports.
DOS: This module will make your victim’s machine unresponsive. After this attack, the victim’s machine hangs and doesn’t give any response.
ping: To ensure that your victim is reachable or not.
injecthtml: This module injects HTML code in your victim’s machine, and whenever your victim opens a website, your HTML code will be shown there.
injectjs: Similar to Injecthtml. Whenever your victim opens any website, your javascript also runs there.
sniff: It sniffs the packets of your victim’s machine.
dspoof: It will redirect all HTTP traffic to a specific Website, which you gave in this module.
yplay: Whenever your victim opens any website, a sound, which is specified in this module, is played in the background.
replace: This is also interesting. It replaced all the images of the victim’s browser with a specific image which you provided.
driftnet: This module captures every image seen by your victim.
move: This module moves everything in the web browser of your victim’s machine.
deface: This tool overwrites each web page with your particular HTML page.
Tested on
| Operating system | Version |
| Ubuntu | 16.04 / 15.10 |
| Kali linux | Rolling / Sana |
| Parrot OS | 3.1 |
Features
- Port scanning
- Network mapping
- Dos attack
- Html code injection
- Javascript code injection
- Download interception and replacement
- Sniffing
- Dns spoofing
- Background audio reproduction
- Images replacement
- Drifnet
- Webpage defacement and more
























Leave a Reply