
Best Web Penetration Testing Tools
By 2016, there were around 3426971237+ internet users over the world. Being a hub of many users, there comes a responsibility of taking care of the security of these many users. Most of the Internet is the collection of websites or web applications. So in order to prevent these web applications, there is a need of testing them again payloads and malware and for that purpose, we have a lot of tools in Kali Linux.
Kali Linux comes packed with 300+ tools out of which many are used for Web Penetration Testing. Though there are many tools in Kali Linux for Web Penetration Testing here is the list of most used tools.
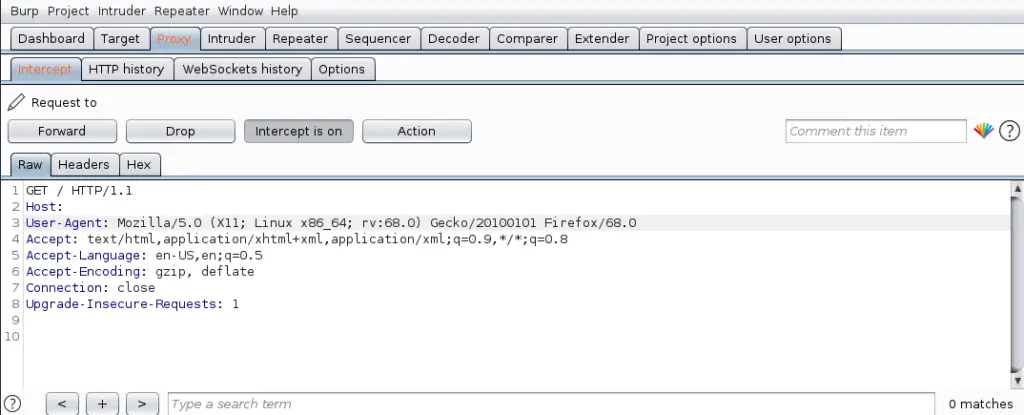
1. Burp Suite
Burp Suite is one of the most popular web application security testing software. It is used as a proxy, so all the requests from the browser with the proxy pass through it. And as the request passes through the burp suite, it allows us to make changes to those requests as per our need which is good for testing vulnerabilities like XSS or SQLi or even any vulnerability related to the web. Kali Linux comes with burp suite community edition which is free but there is a paid edition of this tool known as burp suite professional which has a lot many functions as compared to burp suite community edition.
To use burp suite:
- Read this to learn how to setup burp suite.
- Open terminal and type “burpsuite” there.
- Go to proxy tab and turn the interceptor switch to on.
- Now visit any URL and it could be seen that the request is captured.
2. Nikto
Nikto is an Open Source software written in Perl language that is used to scan a web-server for the vulnerability that can be exploited and can compromise the server. It can also check for outdated version details of 1200 servers and can detect problems with specific version details of over 200 severs. It comes packed with many features, a few of them are listed below.
- Full support for SSL
- Looks for subdomains
- Supports full HTTP Proxy
- Outdated component report
- Username guessing
3. Maltego
Maltego is a platform developed to convey and put forward a clear picture of the environment that an organization owns and operates. Maltego offers a unique perspective to both network and resource-based entities which is the aggregation of information delivered all over the internet – whether it’s the current configuration of a router poised on the edge of our network or any other information, Maltego can locate, aggregate and visualize this information. It offers the user with unprecedented information which is leverage and power.
Maltego’s Uses:
- It is used to exhibit the complexity and severity of single points of failure as well as trust relationships that exist currently within the scope of the infrastructure.
- It is used in the collection of information on all security-related work. It will save time and will allow us to work more accurately and in a smarter way.
- It aids us in thinking process by visually demonstrating interconnected links between searched items.
- It provides a much more powerful search, giving smarter results.
- It helps to discover “hidden” information.
4. SQLMap
SQLMap is an open-source tool that is used to automate the process of manual SQL injection over a parameter on a website. It detects and exploits the SQL injection parameters itself all we have to do is to provide it with an appropriate request or URL. It supports 34 databases including MySQL, Oracle, PostgreSQL, etc.
5. whois lookup
whois is a database record of all the registered domain over the internet. It is used for many purposes, a few of them are listed below.
- It is used by Network Administrators in order to identify and fix DNS or domain-related issues.
- It is used to check the availability of domain names.
- It is used to identify trademark infringement.
- It could even be used to track down the registrants of the Fraud domain.














Leave a Reply