Pivoting is the method in which we get access obtained over ...
Vulnerabilities Scan: 15000+PoCs; 20 kinds of application password crack; 7000+Web fingerprints; ...
Find out how to effectively secure cloud environments using AWS, Azure, ...
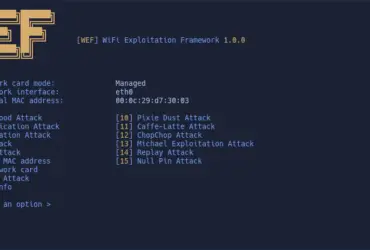
WEF – WiFi Exploitation Framework A fully offensive framework to the ...
The most powerful CRLF injection (HTTP Response Splitting) scanner. CRLFsuite – ...
Welcome to the world of forensics in Cybersecurity. A collection of ...
Awesome Hacking Resources A collection of hacking / penetration testing resources ...
A modern multiple reverse shell sessions/clients manager via terminal written in ...
Awesome Cybersecurity Internships a list of cybersecurity internships, designed to help ...
I Need More Information Check out our RPC Firewall blog post to gain ...