

SSRF plugin for burp Automates SSRF Detection in all of the Request
If you are facing any problems or would like a new feature that is not listed below Please create a new issue below in this form
Upcoming Features Checklist
 It will soon have a user Interface to specifiy your own call back payload
It will soon have a user Interface to specifiy your own call back payload- It will soon be able to test Json & XML
- Test for SMTP SSRF
How to Install/Build
git clone https://github.com/ethicalhackingplayground/ssrf-king
gradle build- Now the file “ssrf-king.jar” could be found under build/libs which can then be imported Burpsuite.
- Alternatively, goto releases to download the compiled file.
Features
 Test all of the request for any external interactions.
Test all of the request for any external interactions. Checks to see if any interactions are not the users IP if it is, it’s an open redirect.
Checks to see if any interactions are not the users IP if it is, it’s an open redirect. Alerts the user for any external interactions with information such as:
Alerts the user for any external interactions with information such as:- Endpoint Vulnerable
- Host
- Location Found
It also performs the following tests based on this research:
Reference:
https://portswigger.net/research/cracking-the-lens-targeting-https-hidden-attack-surface
GET http://burpcollab/some/endpoint HTTP/1.1
Host: example.com
and
GET @burpcollab/some/endpoint HTTP/1.1
Host: example.com
and
GET /some/endpoint HTTP/1.1
Host: example.com:80@burpcollab
and
GET /some/endpoint HTTP/1.1
Host: burpcollab
and
GET /some/endpoint HTTP/1.1
Host: example.com
X-Forwarded-Host: burpcollab
Scanning Options
 Supports Both Passive & Active Scanning.
Supports Both Passive & Active Scanning.
Example
Load the website you want to test.
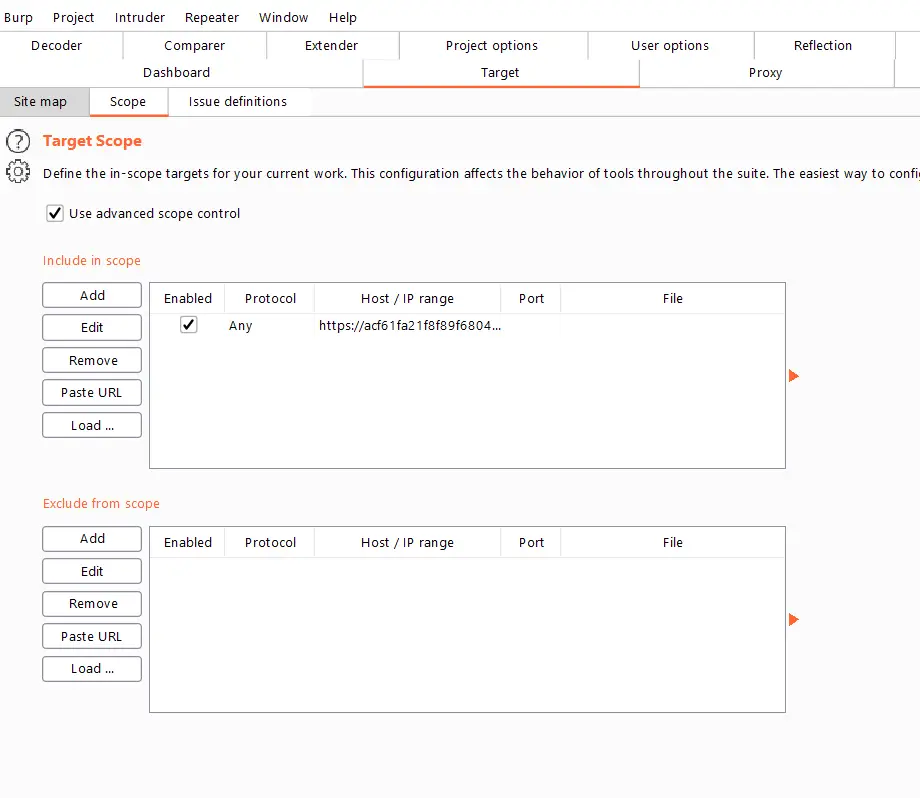
Add it as an inscope host in burp.
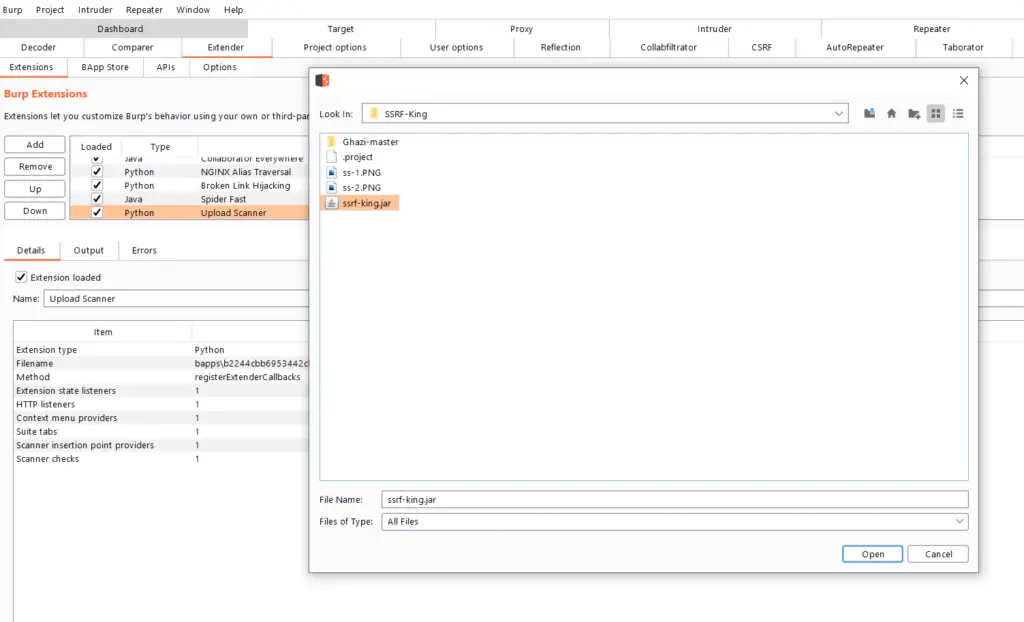
Load the plugin.
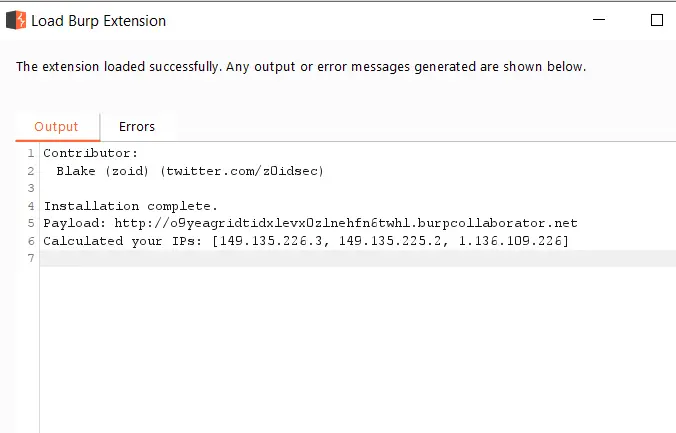
Keep note of the Burp Collab Payload.
Passively crawl the page, ssrf-king test everything in the request on the fly.
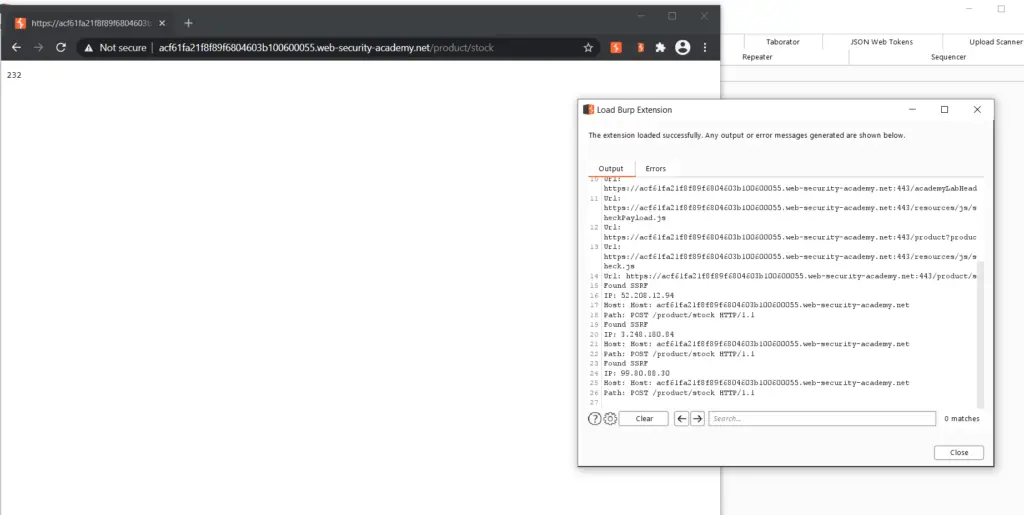
When it finds a vulnerabilitiy it logs the information and adds an alert.
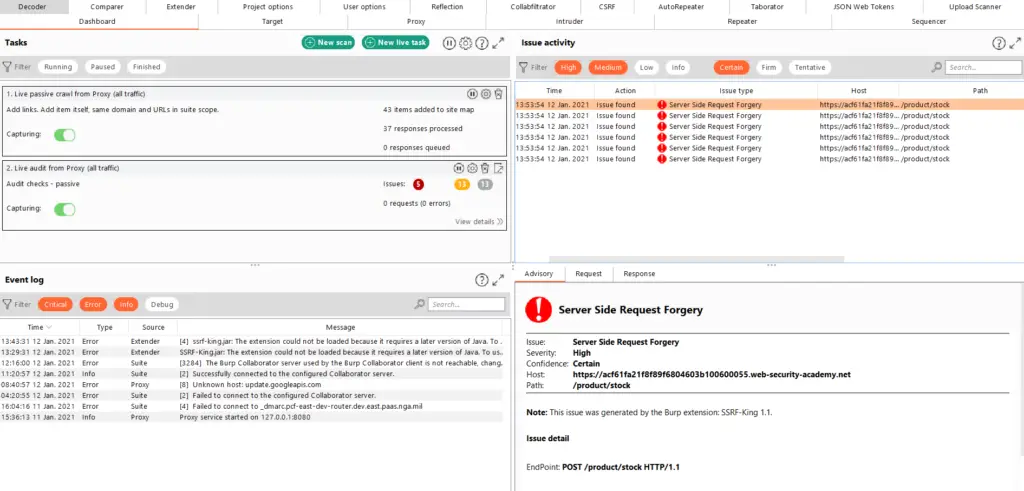
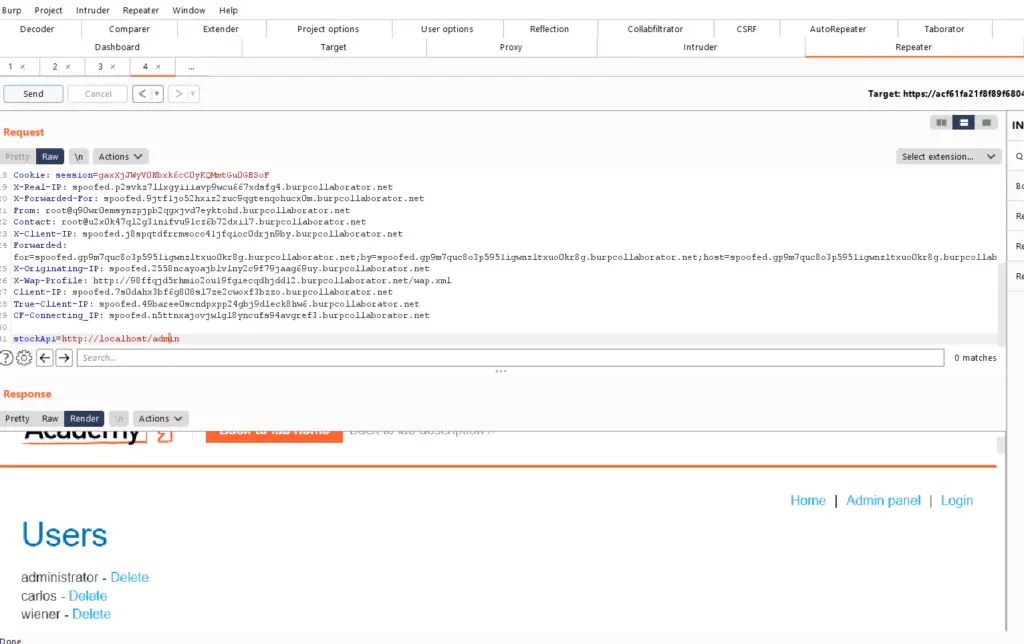
From here onwards you would fuzz the parameter to test for SSRF.
Video Demonstration
If you get a bounty please support by buying me a coffee




















Leave a Reply