
Proxy Cheat Sheet by James Kattler

With more cyber threats emerging and governments trying to access more information about our activity online, users turn to proxies to remain anonymous. However, mere anonymity is not the only reason why this technology became so popular over the past couple of years. Proxies are a great aid in a lot of business processes and complex tech tasks. To understand this tool, let’s study all the details about it.
First, let us define proxies
A proxy is a server users can connect to. It can be a standard server you’d imagine if you think about a data center, for example. And it can be some device that works as a proxy server. We will get into all the differences a bit later. For now, we will focus on the concept.
So, we have a remote server or a device, and we can connect to it. Doing so, we will reroute our traffic through it, and only then head to the destination website. On our way, we will pick up the IP address of the server or gadget and mask our real IP. Therefore, when we reach the destination website, it will not see our real data. That’s how we can pretend to be someone else by using proxies. And that’s how one can remain anonymous online.
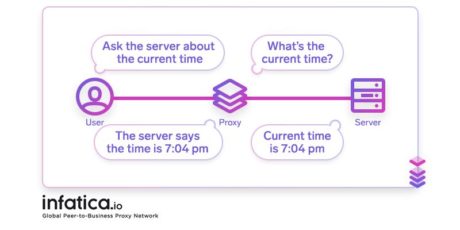
If you’re new to proxies, they might seem a bit fishy to you. But in reality, they’re completely legal, and you’re not breaking any law by using them. Well, until you try to use someone’s device as a proxy without their consent. But if you’re not an advanced enough hacker to do that, your proxy provider is responsible for making sure its network doesn’t violate anyone’s rights.
Proxies are very similar to a VPN, so many people confuse them. The primary difference is that you can apply a proxy to a certain stream of traffic — for example, your browser, or some other program that is connected to the Internet. Also, you can control what server you’re connecting to and, therefore, which IP you’re using. A VPN, on the other hand, applies changes to all the outgoing traffic and doesn’t let you choose IPs. So proxies are more precise, and for some tasks, that’s exactly the precision you need.
When proxies are used
The most widely spread use case for proxies is data gathering. Since you can apply this tool to a web scraper and control the rotation of IP addresses, proxies are very convenient for acquiring information from the internet. They allow a scraper to access geo-restricted pages, gather more accurate data, and avoid anti-scraping measures website owners use — this is how price aggregators can scale the process of gathering price intelligence.
Another way to utilize proxies is to make sure your target audience from different locations sees your targeted ads or to check out the ads of your competitors. That’s why this tool became so popular among marketing managers. SEO specialists also like using proxies to check the results of the optimization and gather some valuable information from websites of competitors. And SMM specialists use proxies to manage several accounts on social media without the risk of getting blocked.
Proxies are also useful for testing. One can apply them to make sure the interface of a site or app works properly from all locations. Also, proxies are useful for cybersecurity testing — using them, specialists can simulate attacks.
So, as you can see, there are many uses for proxies. However, many people get them to simply access geo-restricted content.
What are forward and reverse proxies?
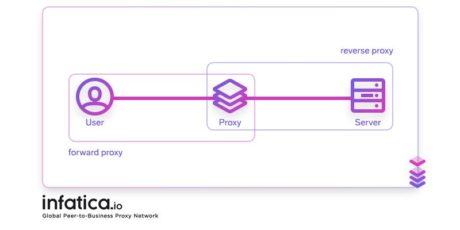
When trying to understand proxies, many users get confused when they meet the terms “forward” and “reverse”. It is a more advanced detail about proxies that will be useful for IT specialists.
Proxies that you’d use for accessing geo-restricted websites, scraping, social media marketing, marketing research, and so on, are forward ones. They process your traffic, apply their IP address to it, and forward it to a destination server — the website you want to visit. Thus, they hide your identity from the server.
Reverse proxies hide the main server from users. They retrieve the data from users without allowing them to access the main server. But the traffic, in the end, is assigned to this server. Reverse proxies are useful for protecting websites from DDOS attacks and malware. Also, they can distribute the traffic to several servers and reduce the load. Webmasters can use them to compress the content or force traffic through another website first.
But if you simply need to hide your IP for any reason, there is no need for you to fathom all the details of reverse proxies because you need forward ones.
Different kinds of forward proxies
Before we jump to all the types of proxies, we want to talk about free ones a bit. You can find free proxies, and they might satisfy your needs if all you want from them is to let you access a geo-restricted website. But they’re usually of low quality, and it will be very hard to use them for any more complex purposes. So if you’re looking for proxies for your professional needs, we advise you to stick to paid ones.
Some providers, such as Infatica, maintain a good balance between price and quality and offer reliable proxies at affordable costs. If you check out any of the existing vendors, you will see that they have different kinds of proxies.
Data center proxies
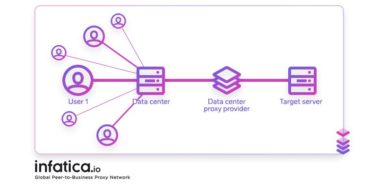
If you’re looking for the cheapest solution, these proxies should be your choice. Using them, you will connect to a shared server along with other customers of your provider. It will mask your IP address, but since there are many users connected to one server, you might experience issues with such tasks as scraping. Datacenter proxies can’t offer impeccable anonymity. However, they will be quite fitting for the needs of a social media manager, for example.
Residential proxies
Using these proxies you will connect to a device that has a unique IP address issued by a real ISP. Proxy vendors source such IPs through a completely compliant network, so you have nothing to worry about — you will not violate the rights of a device owner. Residential proxies offer high anonymity because you will appear like a real resident of the country where the device-mediator is located. They are perfect for scraping and marketing research.
Mobile proxies
These are residential proxies with IP addresses that are issued by a mobile operator and belong only to mobile devices. They’re great for testing and some specific marketing needs. Mobile proxies are the most expensive kind you can get because they’re difficult to source.
Now you can feel confident when looking for a proxy provider for your business needs. And remember — a good reliable vendor will always help you out if you can’t decide which proxies fit you best or you have some additional questions.
About the Author:
James Kattler is a web proxy solution specialist at infatica.io. His interests include information security, ethical hacking, and web development.














Leave a Reply