
People tracker on the Internet: OSINT analysis and research tool by Jose Pino
Trape is an OSINT (Open Source Intelligence Tool) tracking tool that allows people to track and execute intelligent social engineering attacks in real time. The main purpose of creating this tool was to show people how an attacker can obtain confidential info, such as victim location beyond their IP addresses, without knowing the victim.
As a security specialist, you know that there are several ways to get information about your target/client, one of them is running a remote scan and checking for open ports or any exposed vulnerabilities. A second way that is becoming very common is targeted social engineering attacks by verifying online services for OSINT and sending phishing attacks. If you are interested in the second option, Trape is your best choice.
There are many great features this tool presents, below you will find only a few of them:
- Location Optimization: Trace the path between you and the target you’re tracking.
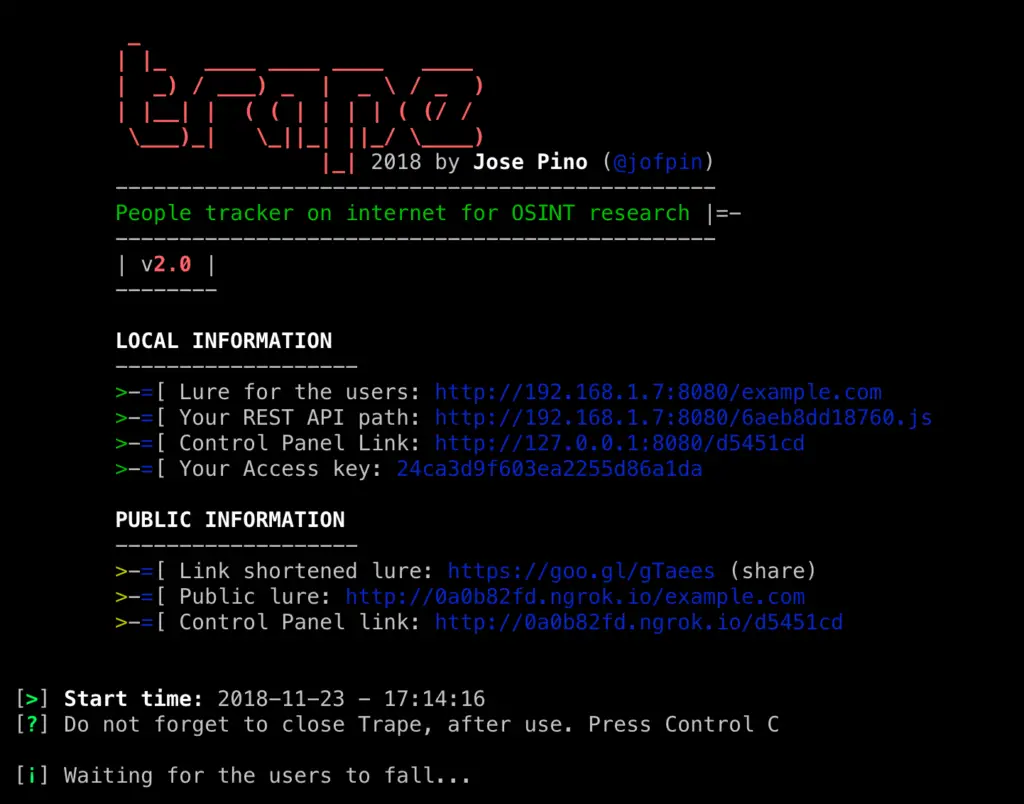
- REST API: Generates an API (random or custom), and through this you can control and monitor other web sites on the Internet remotely, getting the traffic of all visitors.
- Process Hooks: Manages social engineering attacks or processes in the target’s browser.
- Several: You can issue a phishing attack of any domain or service in real time as well as send malicious files to compromise the device of a target.
- Inject JS: You keep the JavaScript code running free in real time, so you can manage the execution of a keylogger or your own custom functions in JS that will be reflected in the target’s browser.
- Public Network Tunnel: Trape has its own API that is linked to ngrok.com to allow the automatic management of public network tunnels.
Using this tool will be useful during penetration testing you will perform for your client, to test your target with phishing and social engineering attacks and see how the target interacts with the links.
How to use it:
First unload the tool.
git clone https://github.com/jofpin/trape.git cd trape python2 trape.py -h
If it does not work, try to install all the libraries that are located in the file requirements.txt
python2 -m pip install -r requirements.txt
Example of execution
Example: python2 trape.py --url http://example.com --port 8080
HELP AND OPTIONS
user:~$ python2 trape.py --help usage: python trape.py -u <> -p <> [-h] [-v] [-u URL] [-p PORT] [-ak ACCESSKEY] [-l LOCAL] [--update] [-n] [-ic INJC] optional arguments: -h, --help show this help message and exit -v, --version show program's version number and exit -u URL, --url URL Put the web page url to clone -p PORT, --port PORT Insert your port -ak ACCESSKEY, --accesskey ACCESSKEY Insert your custom key access -l LOCAL, --local LOCAL Insert your home file -n, --ngrok Insert your ngrok Authtoken -ic INJC, --injectcode INJC Insert your custom REST API path -ud UPDATE, --update UPDATE Update trape to the latest version
–url In this option, you add the URL you want to clone, which works as a decoy.
–port Here you insert the port, where you are going to run the Trape server.
–accesskey You enter a custom key for the Trape panel, if you do not insert it will generate an automatic key.
–injectcode Trape contains a REST API to play anywhere, using this option you can customize the name of the file to include, if it does not, generates a random name allusive to a token.
–local Using this option, you can call a local HTML file, this is the replacement of the –url option made to run a local lure in Trape.
–ngrok In this option, you can enter a token, to run at the time of a process. This would replace the token saved in configurations.
–version You can see the version number of Trape.
–update Option used to upgrade to the latest version of Trape.
–help It is used to see all the above options, from the executable.
You can read more and download the OSINT tool over here: https://github.com/jofpin/
At the beginning of the year 2018 was presented at BlackHat Arsenal in Singapore: https://www.blackhat.com/asia-18/arsenal.html#jose-pino and in multiple security events worldwide.
Talk to and follow Jose Pino at https://twitter.com/jofpin














Leave a Reply