
EarlyBird: a poc of using the tech with syscalls on powershell.exe
injecting cobalt strike shellcode to powershell.exe using EarlyBird Tech
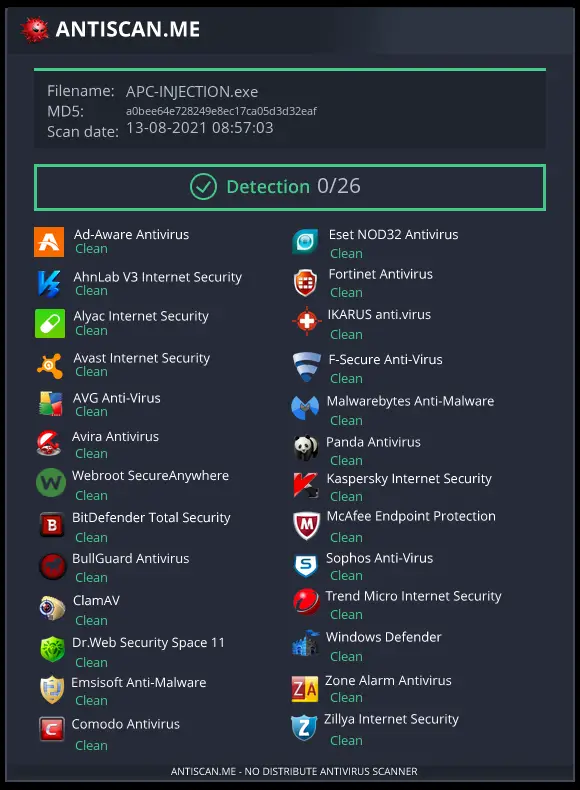
USAGE:
- first get ur self a nice profile
- generate ur x64 https shellcode (in c format)
- paste it in encoder.py and run it using python2
- copy and paste the output to here
- if u changed the key, change it in main.cpp too
DEMO:
Based on:
https://www.ired.team/offensive-security/code-injection-process-injection/apc-queue-code-injection https://github.com/odzhan/injection/tree/master/apc
















Leave a Reply