

Pentesting lab with a Kali Linux instance accessible via ssh & wireguard VPN and with vulnerable instances in a private subnet
AWS Pen-Testing Laboratory
PenTesting laboratory deployed as IaC with Terraform on AWS. It deploys a Kali Linux instance accessible via ssh & wireguard VPN. Vulnerable instances in a private subnet.
NOTE:
- Ids only defined for region “eu-west-1”
- For other regions, kali ami id must be specified and metasploitable3 id (after building it)
Diagram
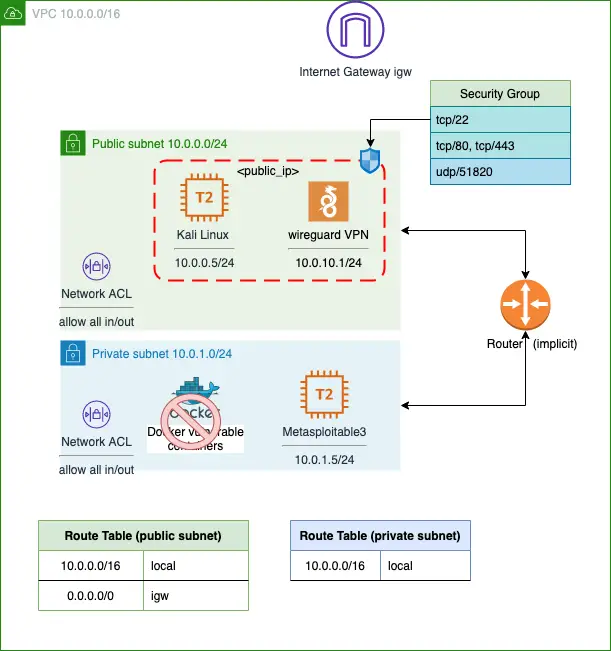
Components
- Kali 2020.4 instance (private key is saved into kali.pem)
- Wireguard VPN service: client file client_vpn.wg
- Accessible via ssh/scp
- Public Subnet 10.0.0.5/24
- Vulnerable machine “Metasploitable” (ami build is public)
- Private subnet 10.0.1.5/24
- More vulnerable labs/machines/docker (to-be-done)
How-To
- Requirements:
- Terraform CLI install guide
- AWS CLI install guide
- $PATH configured for AWS CLI & Terraform
- AWS account and configure credentials via aws cli:
aws configure - Kali Linux Subscription in AWS Marketplace (version 2020.04)
- Metasploitable3 AMI image previously built (public AMI available for eu-west-1 region) see
Deploy
terraform init
terraform plan
terraform apply -auto-approve
Usage
Either connect to Kali via ssh or wireguard:
- SSH: (Only command line) Use autogenerated private key (see terraform output)
- Wireguard: Connect your local kali instance via wireguard (see client_vpn.wg generated file)
Destroy
terraform destroy -auto-approve















Leave a Reply